The cybersecurity landscape continues to evolve as threat actors deploy increasingly sophisticated phishing techniques to bypass security controls and steal user credentials.
Security researchers at Push Security have recently identified a concerning development in the Phishing-as-a-Service (PhaaS) ecosystem: the Sneaky2FA phishing kit has incorporated the Browser-in-the-Browser (BitB) technique to target Microsoft account credentials with unprecedented stealth.
Sneaky2FA operates as a fully-featured Telegram bot, providing customers with licensed, obfuscated source code for independent deployment.
This distribution model creates identifiable codebase similarities that allow security teams to track and profile threats reliably. However, the latest iteration represents a significant tactical shift from typical reverse-proxy Attacker-in-the-Middle (AiTM) implementations.
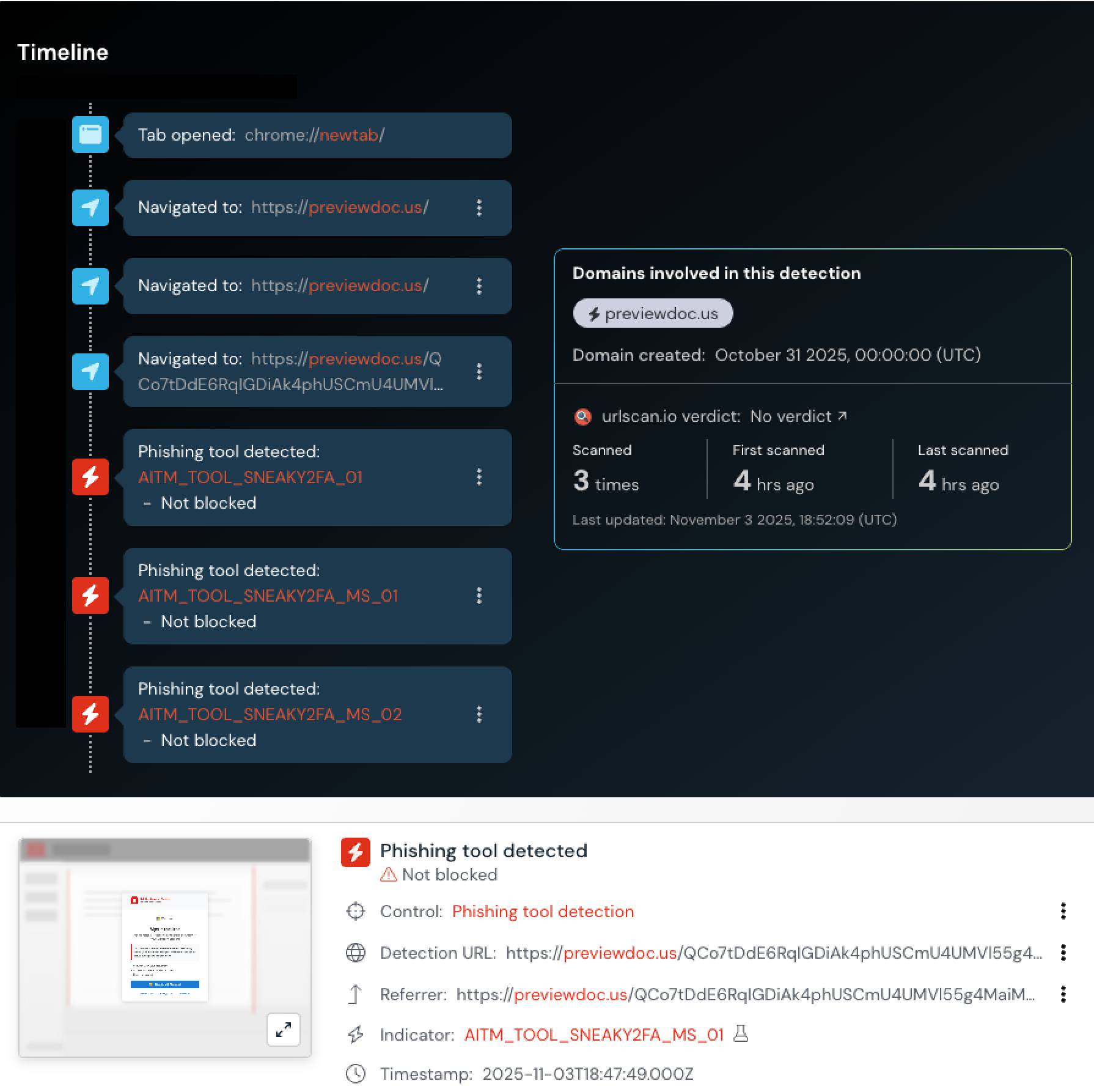
Push Security researchers recently detected a Sneaky2FA server featuring an embedded browser window containing the actual phishing page.
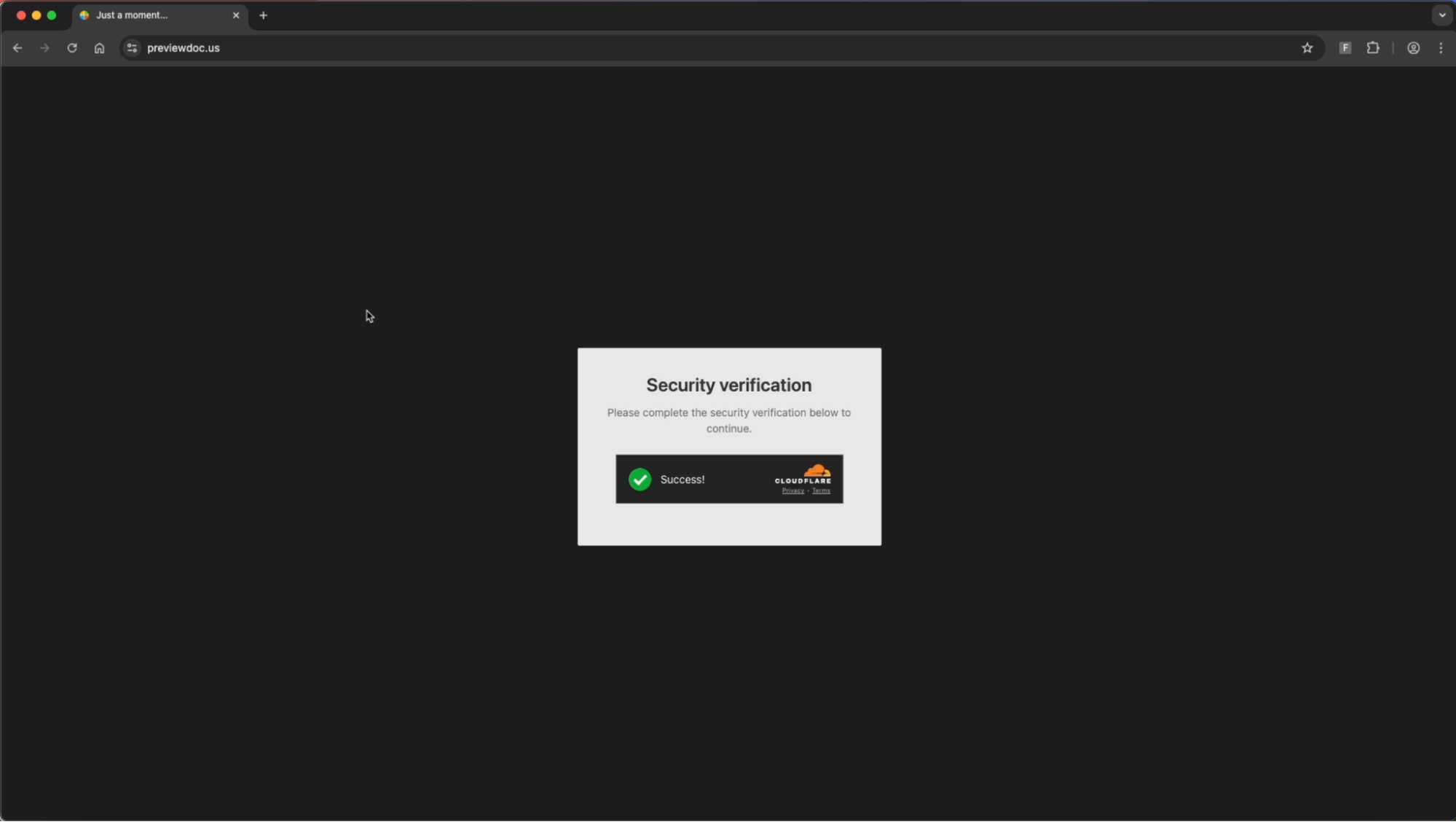
When victims access the malicious URL, they first encounter a Cloudflare Turnstile bot protection check.
After passing this verification, users are redirected to a subdomain prompting them to “Sign in with Microsoft” to view a document styled to resemble Adobe Acrobat Reader.
The sophistication becomes apparent when victims click the sign-in button: a reverse-proxy phishing page mimicking Microsoft’s login form loads within an embedded browser window, complete with a custom background image designed to resemble a document library.
The system dynamically adjusts the pop-up window appearance based on the visitor’s operating system and browser, creating a convincing authentication experience that results in credential theft and account takeover.
Why Browser-in-the-Browser Matters
Originally coined as a technique in 2022 by security researcher Mr.d0x, BitB primarily aims to mask suspicious phishing URLs by simulating standard in-browser authentication flows through pop-up login forms.
The technique replicates pop-up window design using iframes pointing to malicious servers, displaying fake but legitimate-looking Microsoft login URLs instead of revealing the actual phishing server address.
This Sneaky2FA implementation incorporates multiple detection evasion techniques commonly baked into PhaaS kits.
Conditional loading techniques block unwanted visitors including known security vendor IPs and VPN services while targeting specific organizations or users.
When incorrect parameters are detected, the system redirects to benign wikibooks pages to avoid suspicion.
Bot protection technologies like CAPTCHA and Cloudflare Turnstile prevent security bots from analyzing pages and automatically flagging malicious content.
Sneaky2FA employs heavily obfuscated HTML and JavaScript to evade static detection and pattern-matching.
Techniques include breaking up UI text with invisible tags, embedding background elements as encoded images, and disabling browser developer tools to block malicious content analysis.
The kit also utilizes domain rotation and URL masking strategies, with each campaign using fresh, randomized 150-character URLs on benign-looking or compromised domains that remain dormant until right before attacks.
The Growing PhaaS Threat Landscape
PhaaS kits like Tycoon, NakedPages, Flowerstorm, Salty2FA, and Evilginx variations dominate the phishing ecosystem by making sophisticated capabilities accessible to criminals with lower technical barriers.
Completing authentication will result in the user’s Microsoft credentials and active session being stolen by the attacker, facilitating account takeover.
This “burn-and-replace” approach significantly weakens traditional security defenses relying on domain reputation or pattern-matching.
Evidence suggests Sneaky2FA’s shift to BitB may signal broader industry movement, with another PhaaS service, Raccoon0365, announcing a “BITB mini-panel” as part of service enhancements.
This competitive environment has fueled innovation where MFA-bypass is standard, phishing-resistant authentication faces downgrade attacks, and detection evasion circumvents email scanners, web-crawling tools, and web proxies.
With identity-based attacks continuing as the leading breach cause, the continuous refinement of phishing infrastructure through techniques like BitB means traditional security controls will face ongoing challenges in protecting enterprise environments.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
