Cybersecurity researchers have observed the emergence of a novel Android banking trojan, RatOn in recent months that seamlessly combines remote access capabilities with NFC relay technology and Automated Transfer System (ATS) functions.
Initially detected in mid-July 2025, RatOn’s multi-stage architecture leverages a dropper application to install subsequent payloads, culminating in full device takeover and fraudulent transaction execution.
The trojan is distributed via adult-themed domains masquerading as third-party installers, targeting Czech and Slovakian users in its early campaign.
Its sophisticated design allows attackers to abuse Accessibility and Device Administrator permissions for both screen-state monitoring and automated interactions with legitimate banking applications.
Threat Fabric analysts noted that RatOn’s developers appear to have written the malware entirely from scratch, with no apparent code reuse from existing Android banking families.
Following installation, the first payload requests Accessibility service access through a WebView interface and subsequently escalates privileges to manage system settings and contacts.
.webp)
Once granted, these permissions enable the trojan to operate stealthily in the background, capturing on-screen elements via Accessibility API rather than resource-intensive screen casting.
RatOn then loads a third-stage payload—NFSkate malware—originally designed for NFC relay attacks, effectively combining card skimming with remote device control.
Threat Fabric researchers identified that the automated transfer feature focuses specifically on a Czech banking application, “George Česko.”
Upon receiving a JSON-formatted command from its control server, RatOn launches the targeted banking app and simulates user interactions, including PIN entry, to execute unauthorized transfers.
This level of precision indicates a deep understanding of the bank’s user interface, down to coordinate-based clicking when element-based search fails.
Notably, the trojan automatically confirms transaction PINs, which are harvested during earlier phishing or overlay steps, ensuring fraudulent transfers proceed without user intervention.
.webp)
In one observed transfer routine, the operator issues a JSON object to RatOn containing recipient details:-
{
"command_id": "transfer",
"receiver_name": "John Doe",
"account_number": "CZ6508000000001234567899",
"amount": "15000",
"currency": "CZK"
}Infection Mechanism
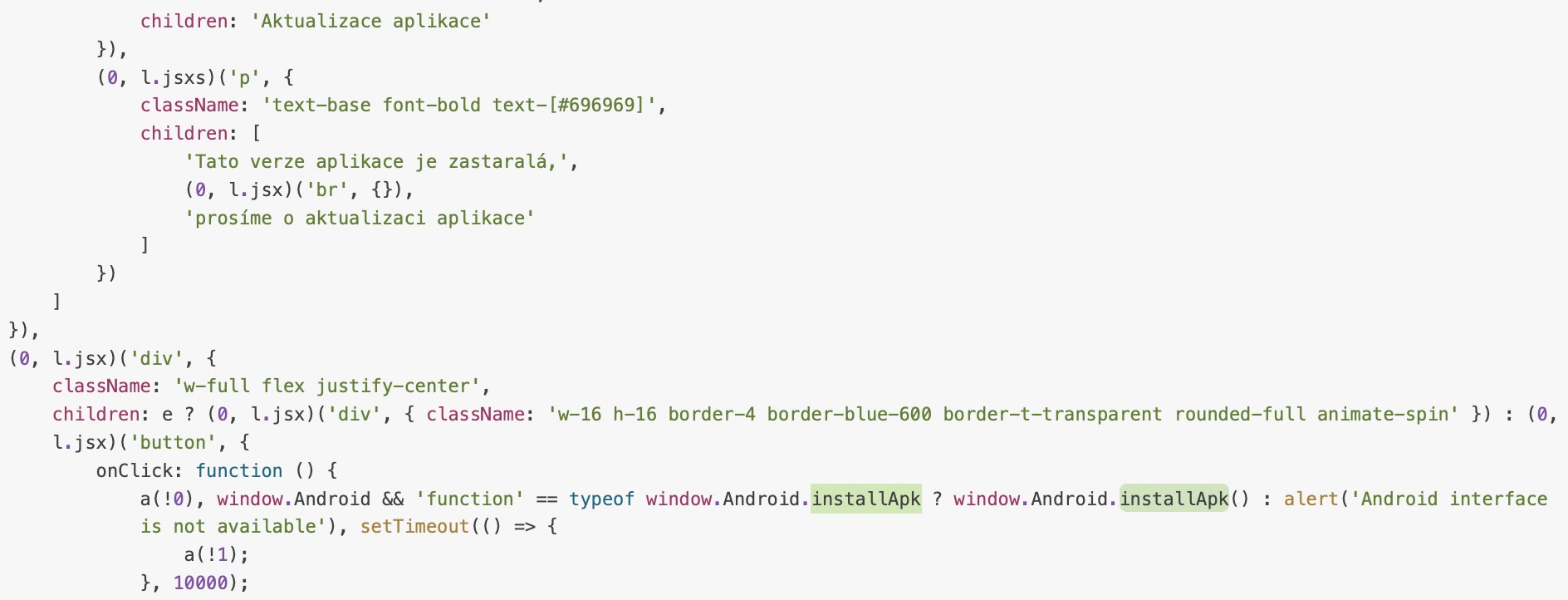
RatOn’s infection chain begins with a dropper application that prompts the victim to enable third-party app installations.
Upon user approval, the dropper creates a WebView pointing to a hardcoded URL and exposes an installApk() function to the page.
When the victim taps the on-screen button, the dropper invokes installApk() to sideload the second-stage payload:-
webView.addJavascriptInterface(new Object() {
@JavascriptInterface
public void installApk() {
PackageInstaller.SessionParams params =
new PackageInstaller.SessionParams(PackageInstaller.SessionParams.MODE_FULL_INSTALL);
int sessionId = packageInstaller.createSession(params);
// ... install logic for payload.apk ...
packageInstaller.openSession(sessionId).write(...);
packageInstaller.openSession(sessionId).commit(...);
}
}, "DropperInterface");After installation, the payload immediately requests Accessibility and Device Admin privileges via additional WebView dialogs.
By exploiting these elevated permissions, RatOn establishes persistence and evades detection: it intercepts permission dialogs, automatically accepts requests, and locks the device for ransom if necessary.
The combination of overlay attacks, NFC relay components, and automated transactions makes RatOn one of the most advanced banking trojans to date.
Boost your SOC and help your team protect your business with free top-notch threat intelligence: Request TI Lookup Premium Trial.
