A new malware-as-a-service (MaaS) information stealer named SantaStealer is being advertised on Telegram and hacker forums as operating in memory to avoid file-based detection.
According to security researchers at Rapid7, the operation is a rebranding of a project called BluelineStealer, and the developer is ramping up the operation ahead of a planned launch before the end of the year.
SantaStealer appears to be the project of a Russian-speaking developer and is promoted for a Basic, $175/month subscription, and a Premium for $300/month.
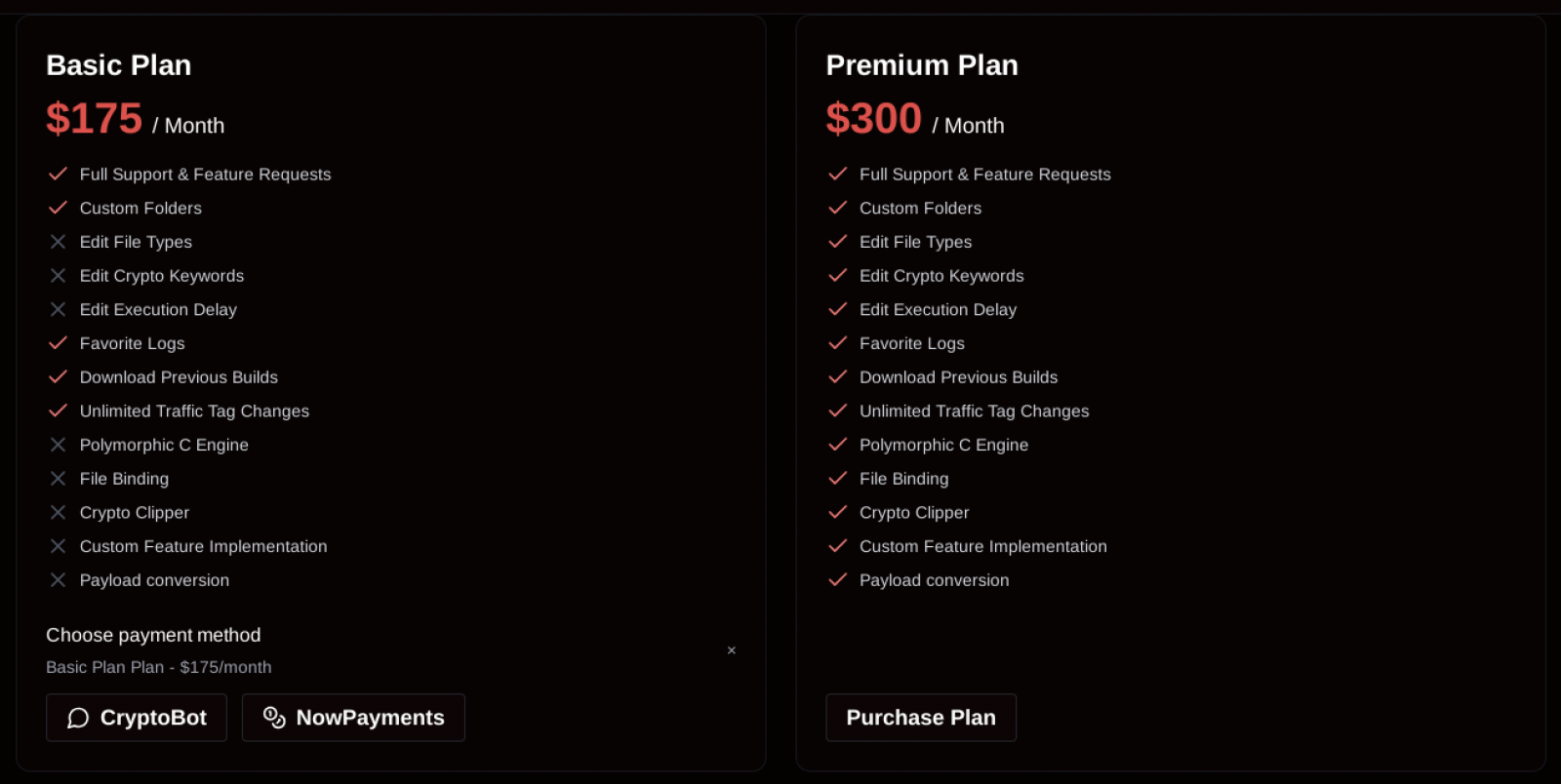
Source: Rapid7
Rapid7 analyzed several SantaStealer samples and obtained access to the affiliate web panel, which revealed that the malware comes with multiple data-theft mechanisms but does not rise to the advertised feature for evading detection and analysis.
“The samples we have seen until now are far from undetectable, or in any way difficult to analyze,” Rapid7 researchers say in a report today.
“While it is possible that the threat actor behind SantaStealer is still developing some of the mentioned anti-analysis or anti-AV techniques, having samples leaked before the malware is ready for production use – complete with symbol names and unencrypted strings – is a clumsy mistake likely thwarting much of the effort put into its development and hinting at poor operational security of the threat actor(s),” Rapid7 says.
The panel features a user-friendly design where ‘customers’ can configure their builds with specific targeting scopes, ranging from full-scale data theft to lean payloads that only go after specific data.
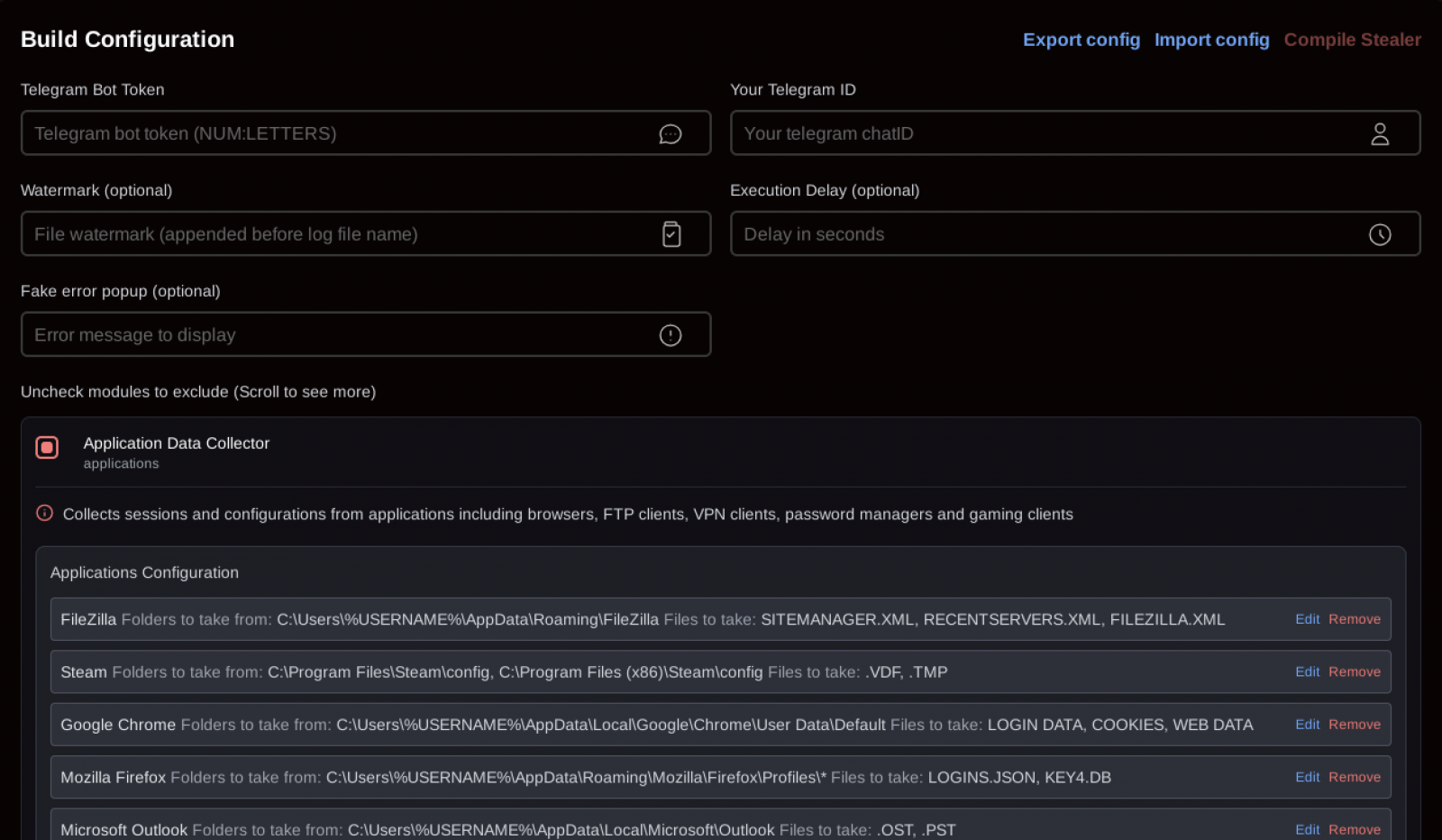
Source: Rapid7
SantaStealer uses 14 distinct data-collection modules, each running in its own thread, writing stolen data to memory, archiving it into a ZIP file, and then exfiltrating it in 10MB chunks to a hardcoded command-and-control (C2) endpoint via port 6767.
The modules target information in the browser (passwords, cookies, browsing history, saved credit cards), Telegram, Discord, and Steam data, cryptocurrency wallet apps and extensions, and documents. The malware can also take screenshots of the user’s desktop.
The malware uses an embedded executable to bypass Chrome’s App-Bound Encryption protections, first introduced in July 2024, and bypassed by multiple active info-stealers.
Other configuration options allow its operators to exclude systems in the Commonwealth of Independent States (CIS) region and delay execution to misdirect victims with an inactivity period.
As SantaStealer isn’t fully operational and hasn’t been distributed en masse, it is unclear how it will spread. However, cybercriminals lately seem to prefer ClickFix attacks, where users are tricked into pasting dangerous commands into their Windows terminal.
Phishing, pirated software, or torrent downloads are also common distribution methods, as are malvertising and deceptive YouTube comments.
Rapid7 recommends users check links and attachments in emails they don’t recognize. They also warn of running unverified code from public repositories for extensions.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.





