A recent investigation of acoustic side-channel attacks was carried out by a group of researchers drawn from a number of the most prestigious educational institutions in the United Kingdom. They claimed in a report that was connected to this that it was possible to steal data by utilizing a microphone to capture the keystrokes that were being made on a keyboard, and that the accuracy rate might approach 95%.
Side-Channel Attacks (SCA) entail the collection and interpretation of signals sent by a device. These signals may include sound, electromagnetic waves, power usage, mobile sensors, and more. Even while it is common knowledge that the electromagnetic radiation given out by wireless keyboards may be detected and read, there is another form of radiation that is much more widespread that the vast majority of people choose to ignore, and that is the sound made by key presses. In addition, as a result of its pervasiveness, it is not only simple to acquire, but it also raises the probability that prospective victims would be less cautious around it. For instance, when individuals type in a password, they often take precautions to guarantee that it is not visually detected, but they nearly never take measures to hide the sound of the keyboard.
Acoustic side-channel attacks did not pose a substantial threat in the past since the relevant technology had not yet reached its full maturity stage. However, as a result of recent developments in microphone performance and the performance of deep learning models, attackers have started to question whether or not such attacks are even feasible. Acoustic attacks, on the other hand, have become more straightforward as a result of the proliferation of microphone-equipped devices, which enables high-quality audio recording. Other types of side-channel attacks, on the other hand, call for certain requirements to be met and are limited by data speeds and distance.
In order to launch the attack, keystrokes from the victim’s keyboard are first captured for the purpose of training the prediction algorithm. This may be accomplished by utilizing a microphone that is close by or by using an infected phone that has access to the microphone.
The Zoom-based recording of keystrokes creates a connection between the sound recordings that rogue participants have made and the messages that have been written. Researchers trained data by pressing 36 keys on a modern MacBook Pro 25 times and capturing the produced sounds.
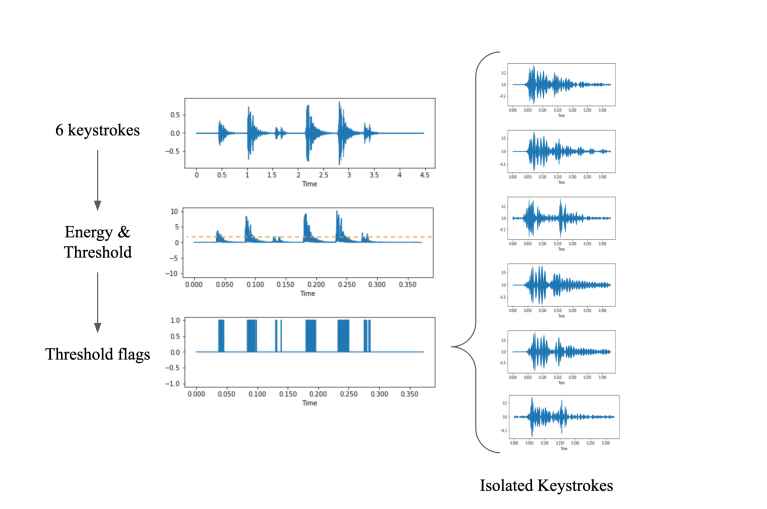
In order to attain the highest possible level of accuracy in its predictions, the image classifier known as CoAtNet was trained using spectrograms. This training method required experimenting with the following factors:
- Epoch
- Learning rate
- Data splitting parameters
During the course of this experiment, the security analysts will make use of the following things:
Keyboard for a standard Apple laptop iPhone 13 mini (positioned 17 centimeters away from the target)
Zoom
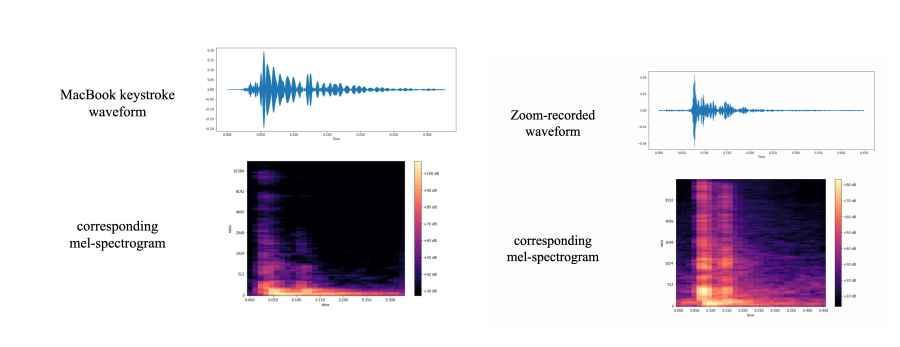
It is not difficult to think of a hypothetical attack scenario in which a phone or computer is compromised by malicious software and given authorization to record through the microphone. This is a situation that is readily imaginable. In addition, even if the tool itself is foolproof, there are still plenty of dangerous situations that may occur in the actual world. It is not difficult, for instance, to gather keyboard noises in public places like libraries or coffee shops. Additionally, the other side may record the sound of keyboard strikes while utilizing conference chat software. In addition, computers of the same model often have the same keyboards. This indicates that if a popular laptop model is vulnerable to an acoustic side-channel attacks, a sizeable section of the population might be at danger.
As the sophistication of these attacks increases, they have the potential to have major repercussions for data security. Sensitive information such as passwords, chat messages, and work papers might possibly be disclosed to third parties that are malevolent.
The research also highlights the fact that even for extremely quiet keyboards, the attack model has been shown to be very successful. As a result, adding dampeners to mechanical keyboards or converting to membrane keyboards is not likely to be of benefit in this situation. The last section of the study presents some appropriate precautionary steps, such as the following, that may be taken to reduce the hazards posed by these acoustic side-channel attacks:
Accuracy in terms of accomplishments
The following is a list of the accomplishments that CoANet has obtained in terms of its accuracy:
Recordings made on smartphones indicate an accuracy of 95%
Accuracy at 93% while using zoom
The accuracy of Skype captures is 91.7%.
Recommendations
The following is a list of all the advice that the cybersecurity researchers have to provide, which can be found below:
- Modify your typing patterns or use passwords that are randomly generated to protect yourself against acoustic side-channel attacks.
- Additional security methods include the use of software that replicates the sounds of keyboards, white noise, and audio filters that are specific to keystrokes.
- Be careful to implement biometric authentication methods wherever they are available.
Make sure that secure password managers are being used.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
