It is getting more difficult to introduce malware into organizations that are being targeted. Many of the conventional payload types, such as .exe files and Office macros, are now subjected to intensive scrutiny, or proactive measures have been taken to address them in order to lessen their effectiveness. In a similar vein, payload distribution channels like as phishing are undergoing increased levels of monitoring and security as part of efforts to make it more difficult for malware distributed by threat actors to infect end-user devices. In order for a phishing campaign to circumvent all anti-phishing security measures and get in the inbox of a target, it is necessary to circumvent mail security controls, IP blocklists, domain reputation, email HTML, content inspection, third-party mail security solutions, and URL filtering, among many other anti-phishing security controls.
In light of this, threat actors and red teams alike are searching for payload distribution channels that are both more recent and perhaps underutilized. The Microsoft Teams External Tenants platform is one of these unique avenues. Experts identified a vulnerability in Team last week that made it possible for malicious actors to transmit malware payload over Team. In addition, a new open-source application has just been made available, which makes it possible to automate this process. TeamsPhisher is a Python3 software that was designed to make it easier for phishing messages and attachments to be sent to users of Microsoft Teams whose companies or organizations permit connection with outside parties.
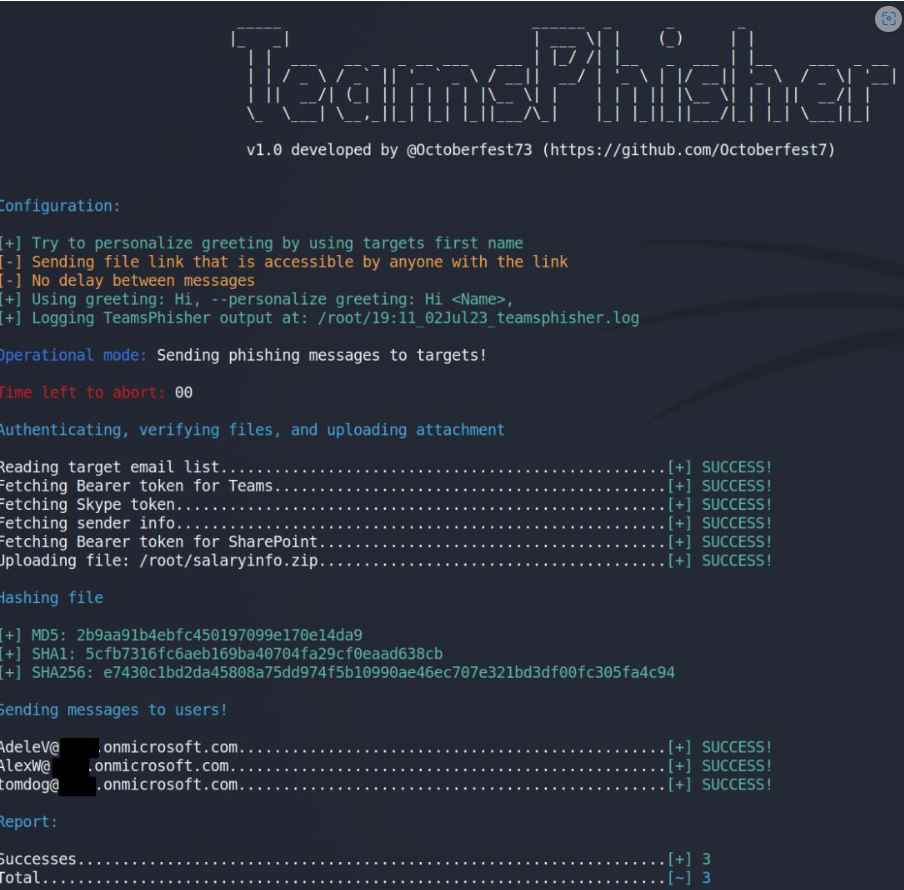
It is not feasible to transfer files to users of Teams who are not part of one’s company in most circumstances. This method, which was found by Jumsec specialists, is included into TeamsPhisher.
You will need to provide TeamsPhisher with an attachment, a message, and a list of people to target. After that, it will go over the list of targets while simultaneously uploading the attachment to the sender’s Sharepoint.
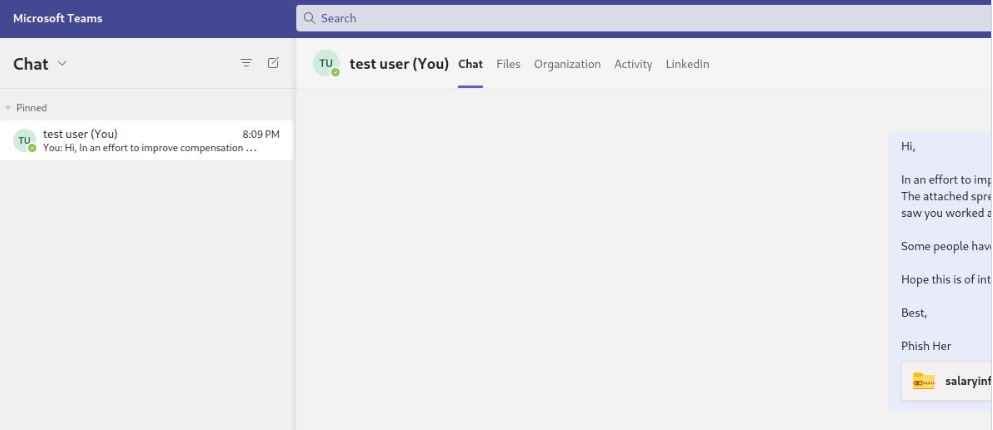
First, TeamsPhisher will enumerate the target user and check to see whether that person really exists and is able to receive messages from the outside world. After that, it will initiate a new conversation with the person you choose. Note that this is technically a “group” conversation since TeamsPhisher contains the target’s email address twice; that will circumvent the “Someone outside your organization messaged you, are you sure you want to view it” splash screen that might offer our targets a reason to stop and think twice about viewing the message.
The user who was identified will get the message that was sent to them along with a link to the attachment that was stored in Sharepoint after a new thread has been established between our sender and the target.
As soon as this first message has been sent, the newly established thread will be available in the sender’s Teams GUI and may be engaged with manually, if necessary, on a case-by-case basis. Start TeamsPhisher in preview mode so that you may check the accuracy of your target list, see what their “friendly names” will be (if TeamsPhisher is able to resolve them thanks to the –personalize flag), and send a test message to your own sender account to ensure that everything appears the way you want it to. Users of TeamsPhisher are required to have a Microsoft Business account (as opposed to a personal one such as @hotmail, @outlook, etc.) that is licensed for both Teams and Sharepoint in order to utilize the software.
This indicates that you will require an AAD tenant as well as at least one user who has a license that corresponds to it. At the time of publishing, the AAD licensing center does have some free trial licenses available for download that are capable of meeting all of the prerequisites for using this product.
The vulnerability that TeamsPhisher takes advantage of is still active, and Microsoft informed the researchers at Jumpsec that the vulnerability did not fulfill the criteria for prompt maintenance.
Information security specialist, currently working as risk infrastructure specialist & investigator.
15 years of experience in risk and control process, security audit support, business continuity design and support, workgroup management and information security standards.
