Researchers from Top10VPN report to Cyber Security News that they have uncovered major vulnerabilities in tunneling protocols that allow attackers to hijack millions of internet hosts, including VPN servers and private home routers.
Researchers have disclosed critical vulnerabilities in widely-used internet tunneling protocols, leaving over 4.2 million hosts at risk of exploitation.
Also highlights the alarming extent to which attackers can hijack internet hosts to conduct anonymous attacks, perform denial-of-service (DoS) campaigns, and gain unauthorized access to private networks.
Key Attacks Identified:
- Ping-pong Amplification Attack:
This novel attack loops packets between vulnerable hosts, amplifying the volume of traffic sent by the attacker. It can also cause Economic Denial of Sustainability (EDoS) by overloading cloud services with outgoing traffic. - Tunneled-Temporal Lensing (TuTL):
This attack sends traffic through chains of vulnerable hosts, creating a peak of inbound traffic at the victim’s endpoint. This overloads the victim’s system, causing benign traffic to be dropped. - Routing Loop DoS:
By sending an IPv6 packet with an invalid destination, this attack causes the packet to loop on the tunneling interface, effectively flooding the system with traffic until it crashes. - Abusing Abuse Reports:
Attackers can spoof traffic that triggers abuse reports toward the victim. This could lead to an administrative DoS, where the victim’s hosting provider disables their account due to multiple abuse reports.
Investigate Real-World Malicious Links & Phishing Attacks With ANY.RUN Malware Sandbox - Try for Free
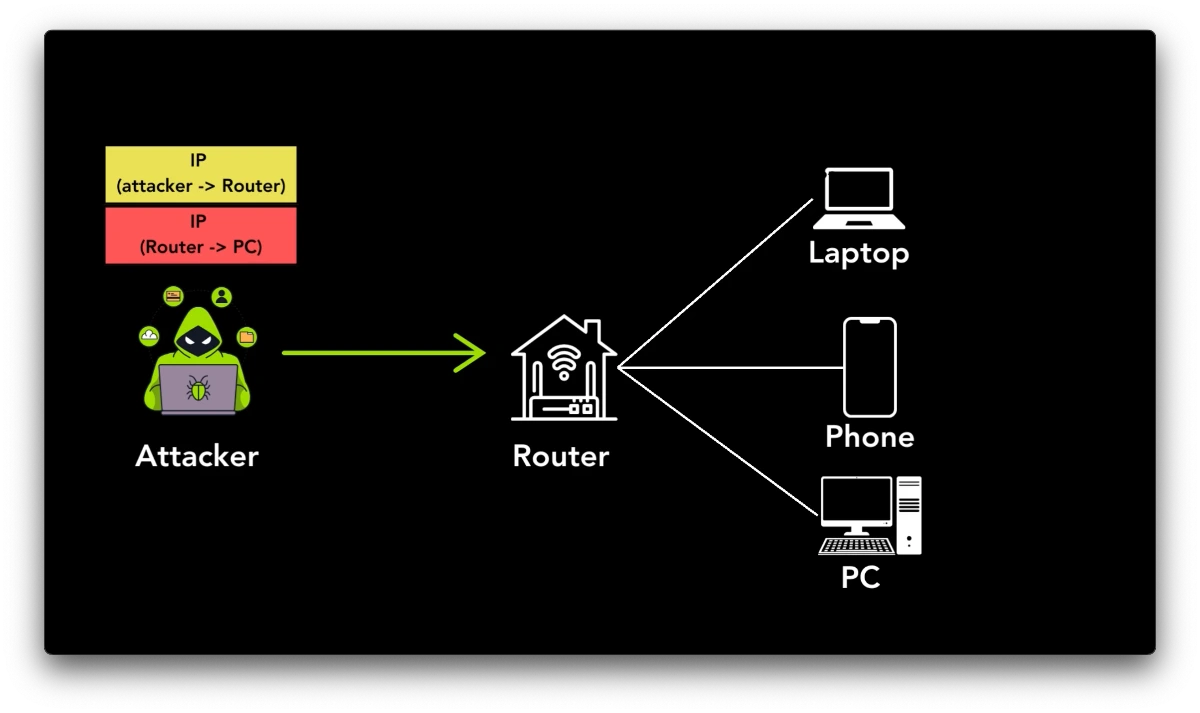
The vulnerabilities stem from the fact that certain tunneling protocols fail to authenticate the origin of incoming packets. This flaw allows adversaries to exploit hosts as “one-way proxies” for launching attacks or accessing private networks. The affected protocols include:
- IPIP/IP6IP6
- GRE/GRE6
- 4in6
- 6in4
Over 4.26 million vulnerable hosts have been identified, spanning a wide range of devices, including VPN servers, ISP home routers, CDN nodes, mobile network gateways, and core internet routers.
Here’s the data in a table format:
| Tunneling Protocol | Vulnerable Hosts | Spoofing Capable |
|---|---|---|
| IPIP | 530,100 | 66,288 |
| IP6IP6 | 217,641 | 333 |
| GRE | 1,548,251 | 219,213 |
| GRE6 | 1,806 | 360 |
| 4in6 | 130,217 | 4,113 |
| 6in4 | 2,126,018 | 1,650,846 |
The global impact is significant, with China, France, the United States, Japan, and Brazil being among the most affected countries.
Additionally, more than 11,000 Autonomous Systems (ASs) were found to be vulnerable, including major networks such as China Mobile, Softbank, and Telmex.
Top10VPN informed Cybersecurity News that “the identified vulnerabilities could allow attackers to exploit systems in various ways, including launching anonymous attacks via unauthenticated packet forwarding and IP spoofing.”
They can also execute advanced denial-of-service (DoS) techniques, such as Ping-Pong Amplification and Routing Loop Attacks.
Additionally, these weaknesses enable the spoofing of DNS queries, manipulation of network traffic, and unauthorized access to private networks via hijacked devices.
New Attack Techniques
Two novel denial-of-service (DoS) attack methods, Tunneled-Temporal Lensing (TuTL) and Economic Denial of Sustainability (EDoS), exploit specific vulnerabilities in networks and devices.
TuTL strategically floods traffic during narrow time windows, overwhelming the victim’s resources, while EDoS amplifies data traffic to increase operational costs, particularly for cloud-hosted services.
These attacks target a wide array of devices, including consumer and enterprise VPN servers, home routers (notably those linked to French ISP Free, affecting over 726,000 devices), and critical enterprise infrastructure reliant on GRE/GRE6 protocols.
A global analysis reveals vulnerabilities across 218 countries, with China and France hosting the majority of spoofing-capable hosts.
Additionally, two autonomous systems are responsible for nearly half of the identified weaknesses, highlighting the systemic nature of the risk.
Tunneling Protocols Vulnerabilities
Professors Vanhoef and Beitis conducted a comprehensive scan of the IPv4 and IPv6 address spaces, identifying 4.26 million vulnerable hosts across multiple tunneling protocols, with 1.86 million capable of IP spoofing.
These vulnerabilities span critical networking protocols, including IPIP/IP6IP6, GRE/GRE6, and 6in4/4in6, commonly used for routing, VPN connections, and facilitating IPv6 and IPv4 interoperability.
The findings highlight significant security gaps, particularly in devices exposed to the internet.
The IPIP and IP6IP6 protocols, affecting 747,741 hosts, are commonly used in Linux-based networking and VPN setups but lack authentication and encryption mechanisms.
Many of the vulnerable systems, primarily servers with open HTTP/HTTPS ports, were linked to domains such as Facebook’s CDN and Tencent’s cloud services.
These protocols often encapsulate IPsec traffic but expose endpoints due to their inherent insecurity.
GRE and GRE6 protocols, with over 1.55 million vulnerable hosts, were widely exploited in enterprise and mobile networks.
These protocols add minimal security layers and were used on core internet routers, including those managing BGP and GTP traffic.
Major domains affected included ISPs and telecom operators, pointing to risks in critical infrastructure.
The 6in4 and 4in6 protocols accounted for nearly half of all vulnerabilities, affecting over 2.25 million hosts.
These tunneling methods enable IPv6 traffic over IPv4 networks and vice versa, underscoring the challenges of slow IPv6 adoption.
Most affected devices were ISP-provided routers with open NTP and SNMP ports, tied to ISPs in countries like France, India, and Japan.
Affected Devices
- VPN Servers: Over 1,365 vulnerable servers identified, with actual numbers potentially reaching 46,000. Affected providers include AoxVPN and defunct services like AmanVPN.
- Dynamic DNS Routers: About 1,200 Synology routers and French ISP Free’s FreeboxOS domains were misconfigured, exposing devices to attacks.
- Business VPNs: 171 company VPNs in 33 countries, mainly using GRE, were at risk. Affected countries include the U.S., China, and Hong Kong.
- ISP Home Routers: French ISP Free had 726,000 vulnerable home routers, which have since been secured. These flaws allowed DoS attacks and network infiltration.
Most Affected ISPs:
- Free (France): 726,194 hosts
- Softbank (Japan): 238,841 hosts
- Eircom Ltd (Ireland): 7,557 hosts
Mitigation Measures
Security experts have proposed defense strategies at both the host and network levels:
- Host-Level Defenses: Restrict tunneling traffic to trusted sources and implement more secure protocols like IPsec or WireGuard.
- Network-Level Defenses: ISPs are urged to filter malicious traffic, inspect deep packet structures, and block unencrypted tunneling packets.
This study builds on earlier work by researcher Livneh Yannay, who discovered similar flaws in IPv4 tunneling protocols in 2020. The latest findings expand the scope, exploring vulnerabilities in IPv6, additional tunneling protocols, and their security implications.
Working with CERT/CC, Professor Vanhoef and his team have alerted affected parties worldwide, prompting companies and ISPs to secure their networks.
Integrating Application Security into Your CI/CD Workflows Using Jenkins & Jira -> Free Webinar
