CyberVolk, a pro-Russia hacktivist group first documented in late 2024, has resurfaced with a sophisticated ransomware-as-a-service (RaaS) offering called VolkLocker after months of dormancy caused by Telegram enforcement actions.
The group returned in August 2025 with version 2.x, featuring advanced Telegram-based automation and cross-platform capabilities targeting both Linux and Windows systems.
VolkLocker is built in Golang, enabling compatibility across multiple operating systems. Unlike many competing RaaS platforms, the malware ships without native obfuscation, requiring operators to apply UPX packing for stealth manually.
To generate new payloads, affiliates must configure several parameters including a Bitcoin wallet address, Telegram bot token ID, chat ID, encryption deadline, custom file extension, and self-destruct preferences.
The ransomware initiates attacks with privilege escalation attempts, exploiting the “ms-settings” UAC bypass technique to hijack the HKCUSoftwareClassesms-settingsshellopencommand registry key for elevated execution rights.
This technique corresponds to MITRE ATT&CK framework identifier T1548.002, demonstrating the group’s adherence to established adversary tactics.
VolkLocker Ransomware
VolkLocker incorporates sophisticated virtual machine detection capabilities to identify sandbox environments and security analysis tools.
The malware performs environmental discovery by checking MAC addresses against known virtualization vendor prefixes, specifically targeting VMware (00:05:69, 00:0C:29, 00:1C:14, 00:50:56) and Oracle VirtualBox (08:00:27, 0A:00:27) identifiers.
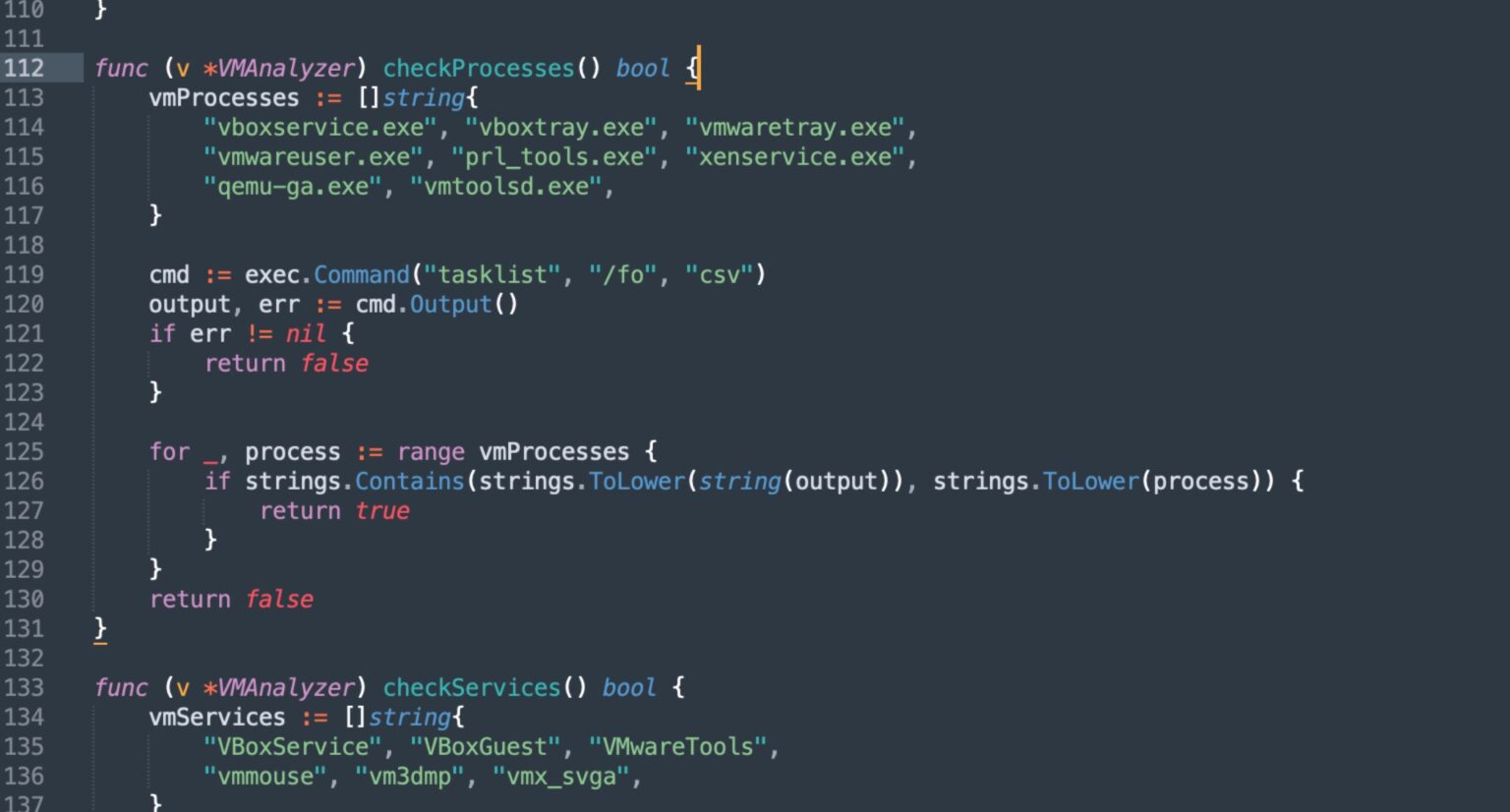
Additionally, it queries registry locations associated with VirtualBox and VMware installations to determine whether it’s operating in an analysis environment.
Once the environment is validated, VolkLocker enumerates all available drives from A: through Z: and applies exclusion filters based on predefined path and extension lists embedded in the code.
This selective targeting ensures system stability while maximizing encryption impact on valuable user data.
The ransomware employs AES-256 encryption in GCM (Galois/Counter Mode) for file encryption, generating a random 12-byte nonce for each file’s initialization vector.
However, security researchers have identified a critical design flaw that fundamentally undermines the operation’s effectiveness.
The malware hardcodes master encryption keys as hex strings within binaries and, more critically, writes these keys in plaintext to %TEMP%system_backup.key during initialization.
This backup file contains the victim’s unique identifier, the complete 64-character master encryption key, and the attacker’s Bitcoin address.
Although the file receives Hidden and System attributes to obscure it from casual directory listings, its existence provides victims with a trivial decryption pathway.
The backupMasterKey() function responsible for this behavior appears to be a test artifact inadvertently included in production builds, suggesting quality control challenges as the operation aggressively recruits affiliates.
Persistence Mechanisms
VolkLocker implements extensive registry modifications to inhibit system recovery and analysis capabilities.
The malware disables Windows Defender real-time monitoring, Task Manager, Registry Editor, Command Prompt, and various system recovery features through both registry manipulation and PowerShell commands.
It terminates security analysis processes including Process Hacker, Process Explorer, and Task Manager using taskkill.exe.
For persistence, the ransomware creates identical copies of itself across multiple system locations including the Startup folder, Public Documents, ProgramData, and Temp directories.
The malware disguises these copies with legitimate-sounding filenames such as svchost.exe, wlanext.exe, and WindowsUpdate.exe.
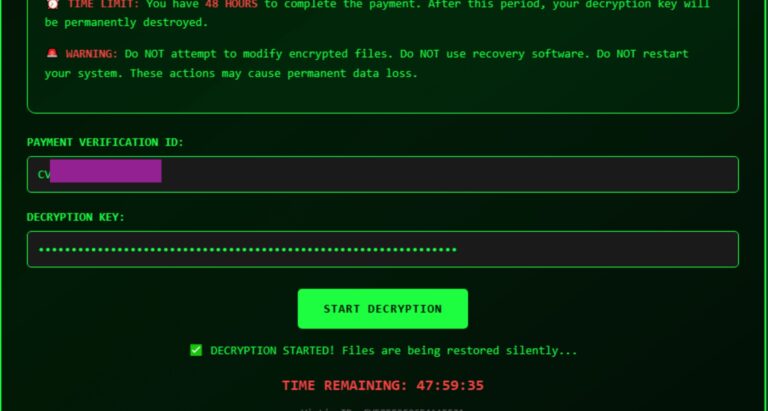
VolkLocker deploys a dynamic HTML ransom note (cybervolk_ransom.html) featuring a countdown timer with a default 48-hour duration.
While the JavaScript-based timer is cosmetic, a separate enforcement timer operates independently using Golang’s time.After() function.
When the deadline expires or incorrect decryption attempts exceed the configured maximum (default: three attempts), the ransomware triggers SystemCorruptor() and DestroySystem() functions.
The destruction mechanism deletes Documents, Desktop, Downloads, and Pictures folders from user profiles, eliminates Volume Shadow Copies using vssadmin, and ultimately triggers a Blue Screen of Death by calling NtRaiseHardError() after a 10-second delay.
Beyond ransomware capabilities, CyberVolk expanded its offerings in November 2025 to include standalone Remote Access Trojan (RAT) and keylogger tools.
The pricing model ranges from $800-$1,100 USD for single-OS RaaS licenses to $1,600-$2,200 USD for combined Linux and Windows support, with standalone RAT or keylogger tools priced at $500 USD each. Bundle discounts are reportedly available for multi-service purchases.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.