WAFFLED is a recently disclosed technique that evades leading Web Application Firewalls (WAFs) by targeting subtle parsing inconsistencies rather than tampering with the malicious payload itself.
By mutating innocuous elements such as boundary delimiters in multipart/form-data, character sets in application/json, or namespace features in application/xml, the attack convinces a WAF that a request is benign while the downstream web framework faithfully reconstructs and executes the embedded exploit code.
Key Takeaways
1. WAFFLED exploits parsing differences between WAFs and applications to bypass security filters.
2. All major WAF providers are vulnerable, with 1,207 bypasses affecting 90% of sites.
3. Mitigation is available through the HTTP-Normalizer proxy or updated WAF rulesets.
WAFFLED Attack Exploits WAFs
According to a team of researchers from Northeastern and Dartmouth, WAFFLED combines grammar-guided fuzzing with automated differential testing to discover “split-brain” interpretations between a frontline WAF and the application framework behind it.
A single HTTP request is generated, then mutated everywhere except the payload. Typical manipulations include:
- Inserting a raw x00 byte into a multipart boundary.
- Re-ordering header parameters (e.g., boundary*0=re;boundary*1=al).
- Swapping newline characters for horizontal tabs in header continuations.
When the WAF and the framework parse the same message differently, the malicious section slips through.
The researchers validated 1,207 unique bypasses across AWS WAF, Azure WAF, Google Cloud Armor, Cloudflare WAF, and ModSecurity, confirming that every mainstream parsing model could be fooled in at least one configuration.
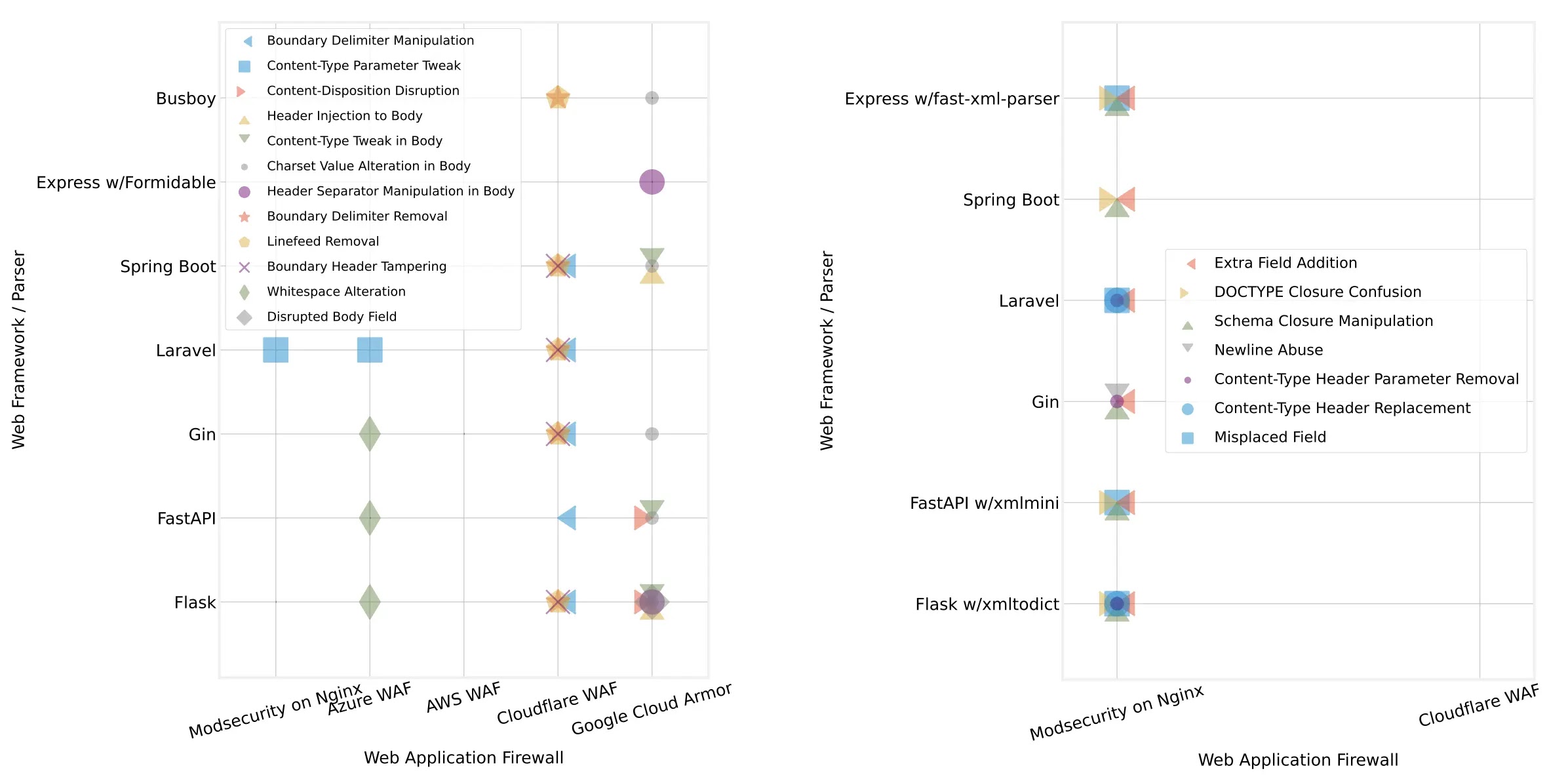
In this cut-down proof-of-concept, Cloudflare’s parser stops at the first fake boundary, sees only harmless data, and forwards the request.
Flask, however, honors the RFC 2231 parameter continuation, concatenates the real boundary, and dutifully executes the XSS payload.
The study shows that more than 90% of live sites accept multipart/form-data when they originally expected application/x-www-form-urlencoded, meaning the vast majority of production forms are trivially exposed to WAFFLED’s multipart bypasses.
Google classified the issue as a Tier 1, Priority 1 vulnerability and paid a bug bounty; Cloudflare, Microsoft, and the ModSecurity community likewise acknowledged the flaw and are rolling out fixes.
AWS WAF’s stricter parser escaped the test suite unscathed, underscoring that meticulous RFC compliance is an effective—if performance-intensive defense.
Mitigation Strategies
The authors released HTTP-Normalizer, an open-source proxy that re-parses incoming messages with a grammar in which invalid states are unrepresentable, then reserializes a canonical form.
Early trials show it rejected or sanitized 100% of sampled WAFFLED inputs with negligible overhead. Organizations unable to deploy an extra proxy can still blunt the attack by:
- Upgrading to the latest managed rulesets (Azure DRS 2.1, ModSecurity CRS 3.3).
- Disabling exotic content-types unless explicitly required.
- Enforcing strict Content-Type, Content-Length, and Transfer-Encoding checks at both the WAF and application layer.
WAFFLED reminds defenders that security devices must not only look at every byte but also agree on what each byte means. RFC-true, tight parsing logic continues to be the most reliable defense against this new class of evasion tactics.
Boost detection, reduce alert fatigue, accelerate response; all with an interactive sandbox built for security teams -> Try ANY.RUN Now