Trend Micro researchers have been monitoring a threat actor known as Water Orthrus since 2021, as they employed pay-per-install networks to distribute the CopperStealer malware.
The malware has undergone several modifications and upgrades by the threat actor to serve different illicit objectives like:-
- Injecting network advertisements
- Obtaining personal information
- Stealing cryptocurrency
While apart from this, cybersecurity experts suggest a potential association between them and the previously reported “Scranos” threat campaign from 2019.
Credential Phishing Campaign
Analysts discovered two new campaigns in March 2023, introducing malware called “CopperStealth” and “CopperPhish,” which share similarities with CopperStealer and are believed to be the work of the same author, suggesting they are the new activities of Water Orthrus.

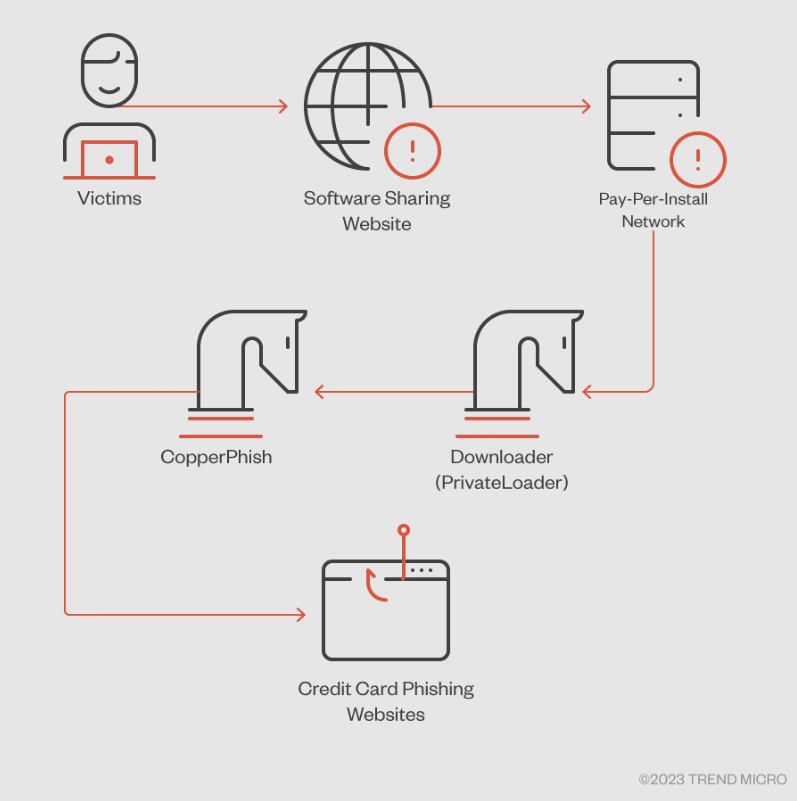
On March 8, 2023, the initial campaign deployed CopperStealth through installers offered on a popular Chinese software-sharing website, masking the malware as free software and focusing on Chinese users.
CopperStealth deploys a rootkit that injects payloads into explorer.exe and other system processes, initiating a download and execution of additional tasks.
Also, the rootkit prevents the execution of certain executables and drivers and blocks access to blocklisted registry keys.
The installer includes encoded URLs that, upon execution, decode and download files from those URLs onto the compromised system, with one of the files being identified as the CopperStealth dropper.
CopperStealth incorporates the “HelloWorld” export function, carried over from previous versions of CopperStealer, and the dropper determines the system architecture to retrieve the related driver from its resources.
There is a file system filter driver that is registered with the rootkit and has specialized handlers for IRP_MJ_CREATE, IRP_MJ_READ, and IRP_MJ_SHUTDOWN in the DriverEntry function.
When the rootkit loads a new process as a driver, it searches for specific byte sequences that are blacklisted, and if found, the entry point of the driver is modified to return:-
Here below we have mentioned all the byte sequences and among them, one of the byte sequences comes embedded with blocklisted drivers:-
- Beijing Huorong Network Technology Co., Ltd.
- Beijing Kingsoft Security Software Co., Ltd.
- Beijing Qihu Technology Co., Ltd.
- HuoRongBoRui (Beijing) Technology Co., Ltd.
- Qihoo 360 Software (Beijing) Co., Ltd.
The statistics module, cnzz, increases a counter in HKCUSoftwareMicrosoftcount_a0b1c2d3 upon execution, verifies internet connection through hxxp://www[.]msftconnecttest[.]com/connecttest.txt, obtains a unique machine ID, reports statistics to hxxp://cnzz_url&m=
CopperPhish begins with downloaders like PrivateLoader, distributed through pay-per-install (PPI) networks via fake download links in advertisements.
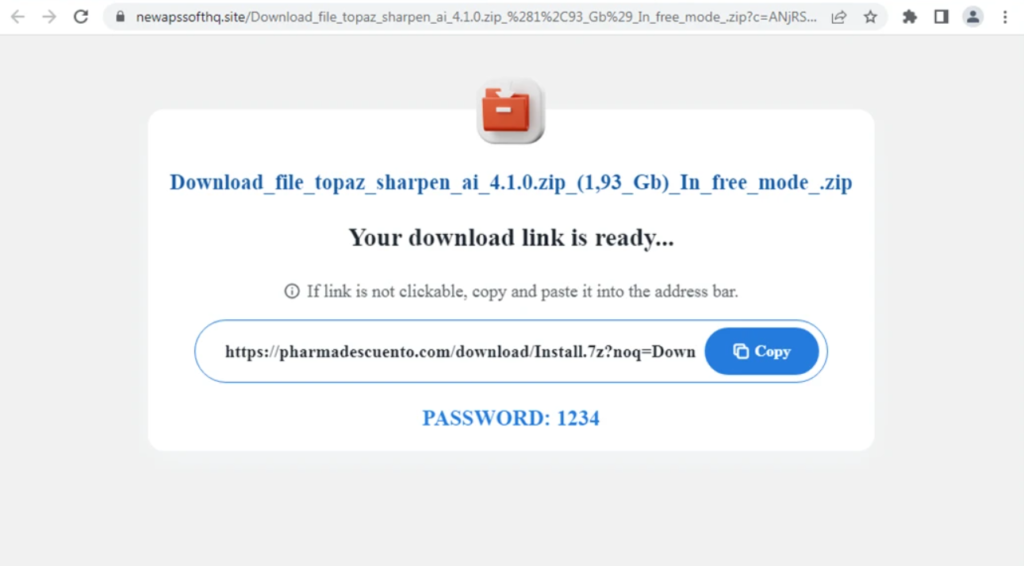
The web browser program employs an Internet Explorer object and the SHDocVwCtl class to manage its behavior, extracting the value from the victim’s “checkcode” input field and sending an exit message to the main payload through the mentioned pipes if the input is correct.
Stealing CC data
The phishing webpage, featuring a Microsoft logo and QR code, lacks controls to minimize or close it, requiring victims to terminate both the browser process and the main payload process to prevent persistence, and a confirmation code serves as proof of correct information provided by the victim.
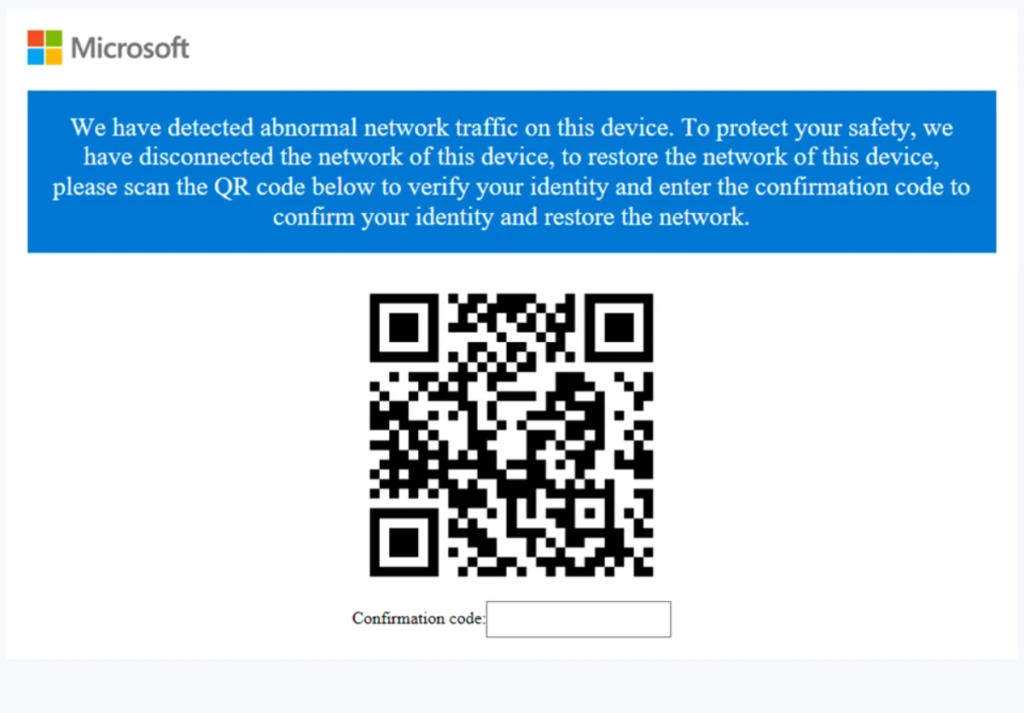
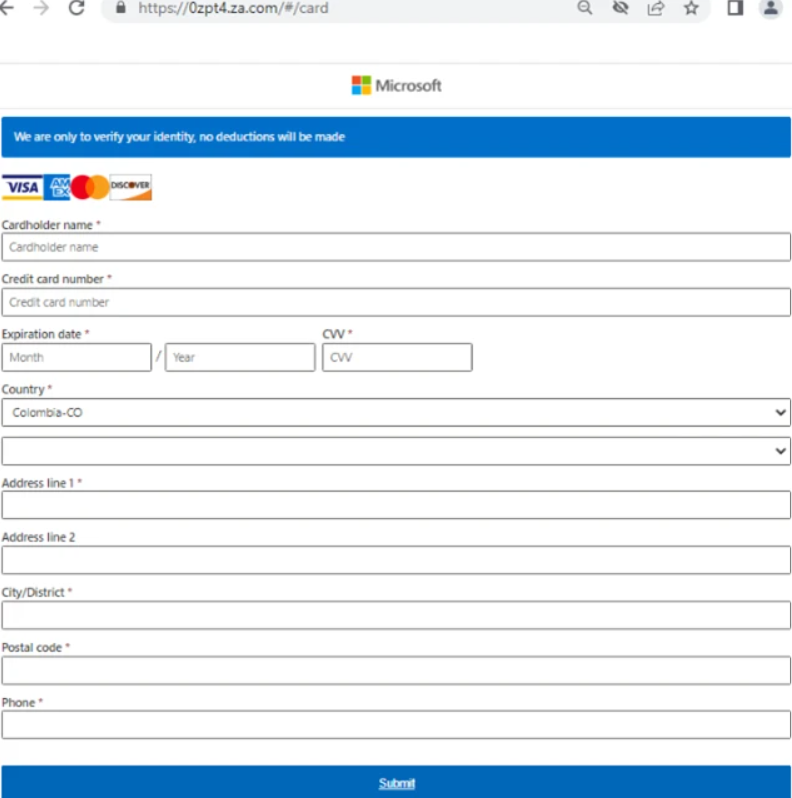
The phishing URL presents the victim with a confirmation page, followed by a page requesting sensitive information such as credit card details like:-
- Credit card number
- Expiration date
- CVV code
CopperPhish is a global phishing campaign targeting credit card information, suggesting that the threat actor has multiple objectives concurrently.
Apart from this, the cybersecurity analysts also highlighted that Water Orthrus had shifted its focus from personal information and cryptocurrency to targeting credit card information.

However, proactive security measures can safeguard organizational devices against such threats.
Struggling to Apply The Security Patch in Your System? –
Try All-in-One Patch Manager Plus
