Microsoft is now using a Windows driver to prevent users from changing the Windows 10 and Windows 11 default browser manually or through software.
The driver was quietly introduced to users worldwide as part of the February updates for Windows 10 (KB5034763) and Windows 11 (KB5034765).
IT consultant Christoph Kolbicz was the first to notice the change when his programs, SetUserFTA and SetDefaultBrowser, suddenly stopped working.
SetUserFTA is a command line program that lets Windows admins change file associations through login scripts and other methods. SetDefaultBrowser works similarly but is only for changing the default browser in Windows.
Starting with Windows 8, Microsoft introduced a new system for associating file extensions and URL protocols with default programs to prevent them from being tampered with by malware and malicious scripts.
This new system associates a file extension or URL protocol to a specially crafted hash stored under the UserChoice Registry keys.
For example, the default web browser assigned to the HTTPS URL protocol is found under:
Windows Registry Editor Version 5.00
[HKEY_CURRENT_USERSOFTWAREMicrosoftWindowsShellAssociationsUrlAssociationshttpsUserChoice]
“ProgId”=”ChromeHTML”
“Hash”=”N3eikAB1HhI=”
If the correct hash is not used, Windows will ignore the Registry values and use the default program for this URL protocol, which is Microsoft Edge.
Kolbicz reverse engineered this hashing algorithm to create the SetUserFTA and SetDefaultBrowser programs to change default programs.
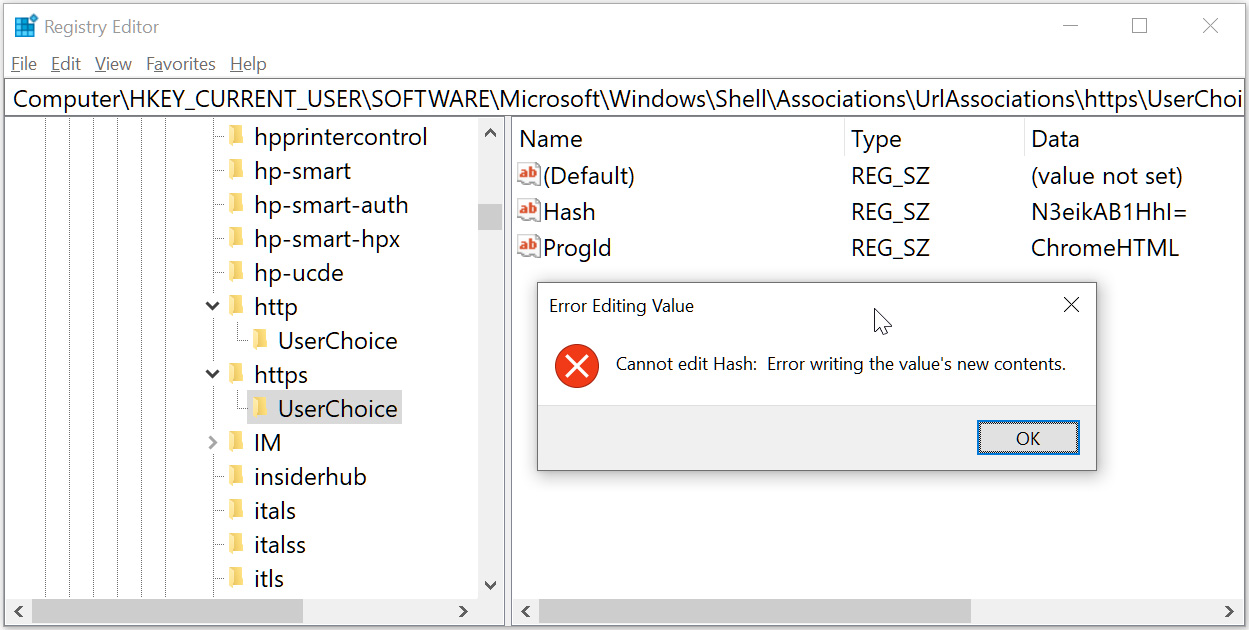
However, with the Windows 10 and Windows 11 February updates installed, Kolbicz noted that these Registry keys have now been locked down, giving errors when edited outside the Windows settings.
For example, using the Windows Registry Editor to modify these settings gives an error stating, “Cannot edit Hash: Error writing the value’s new contents.”
Source: BleepingComputer
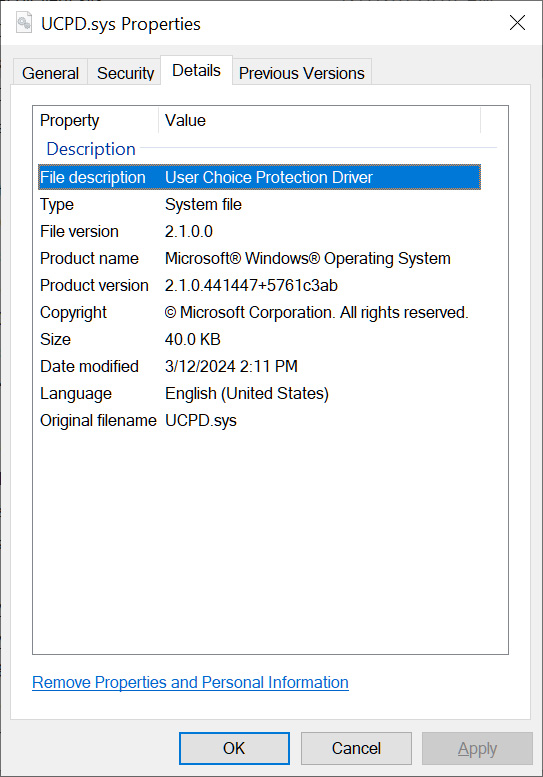
After further research, Kolbicz discovered that Microsoft introduced a new Windows filter driver (c:windowssystem32driversUCPD.sys) as part of the February updates.
Source: BleepingComputer
This driver is described as a “User Choice Protection Driver,” and when loaded, prevents direct editing of the Registry keys associated with the HTTP and HTTPS URL associations and the .PDF file association.
The associated Registry keys are:
HKCUSoftwareMicrosoftWindowsShellAssociationsUrlAssociationshttpUserChoice
HKCUSoftwareMicrosoftWindowsShellAssociationsUrlAssociationshttpsUserChoice
HKCUSoftwareMicrosoftWindowsCurrentVersionExplorerFileExts.pdfUserChoice
It should be noted that in BleepingComputer’s tests, the driver was rolled out to our Windows 11 and Windows 10 devices, but it only locked down the Registry keys on our Windows 10 devices.
In a blog post, Kolbicz explains that while you cannot unload the driver, you can disable it in the Registry.
“We cannot simply unload this driver, BUT we can of course disable it! this can be done by this one-liner – in an elevated PowerShell followed by a reboot.
New-ItemProperty -Path “HKLM:SYSTEMCurrentControlSetServicesUCPD” -Name “Start” -Value 4 -PropertyType DWORD -Force
This brings back the functionality of SetUserFTA, but sadly requires administrative permissions and a reboot.”
❖ Christoph Kolbicz
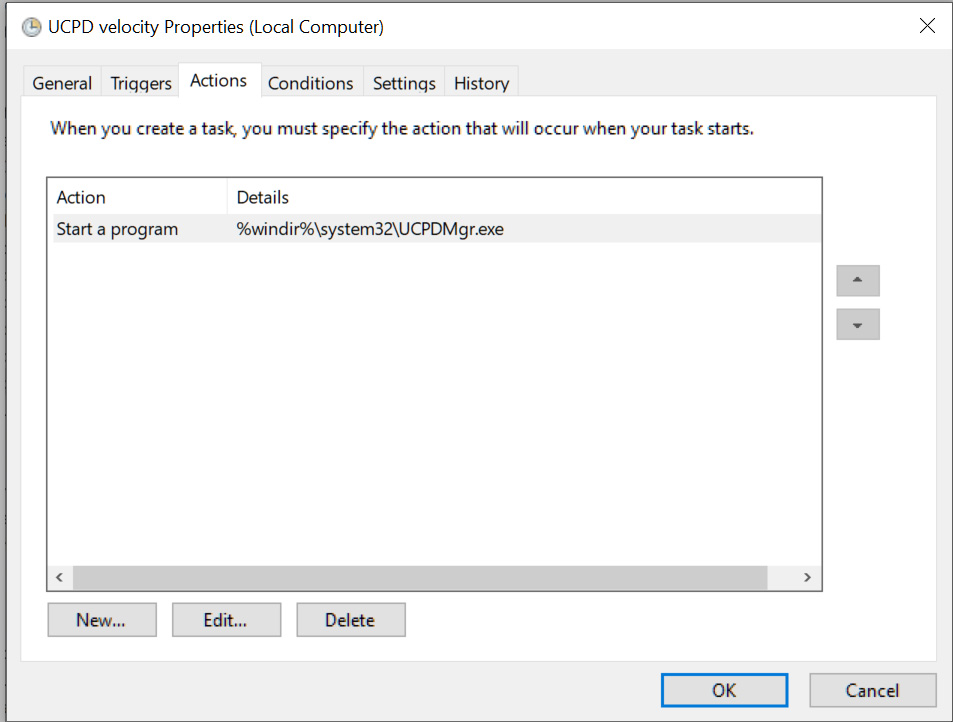
However, a blog post by Gunnar Haslinger explains that a newly created ‘UCPD velocity’ scheduled task under MicrosoftWindowsAppxDeploymentClient will automatically enable the service again if disabled.
Source: BleepingComputer
Due to this, the only way to disable the driver is to turn it off via the Registry and delete/disable the Scheduled Task.
Possibly related to DMA compliance
Kolbicz believes this change may be to comply with Europe’s Digital Markets Act (DMA), which aims to ensure fair competition and the prevention of anti-competitive practices by six large companies, known as “gatekeepers.”
These designated gatekeepers are Alphabet, Amazon, Apple, ByteDance, Meta, and Microsoft, who had until March to comply with the new regulations.
In November 2023, Microsoft outlined changes coming to Windows in March 2024 to comply with the new DMA regulations.
These changes included new default browser policies for users in the European Economic Area (EEA) that force Windows to use users’ default browser when opening a link rather than using Microsoft Edge.
“In the EEA, Windows will always use customers’ configured app default settings for link and file types, including industry standard browser link types (http, https),” explained Microsoft.
“Apps choose how to open content on Windows, and some Microsoft apps will choose to open web content in Microsoft Edge.”
However, this new driver has also rolled out to Windows 10 and Windows 11 devices in the USA that do not have to comply with the DMA act, shedding doubt on this theory.
BleepingComputer contacted Microsoft about the lockdown of these Registry keys in March, but they said they had nothing to share at this time.
