Be cautious of the newly advertised ExelaStealer infostealer malware, now making the rounds on dark web forums and Telegram. Its primary aim is to target Windows-based devices.
KEY FINDINGS
FortiGuard Labs has discovered a new infostealer in the cybercrime landscape called ExelaStealer mostly targeting Windows devices.
The infostealer is written in Python but uses resources in many different languages when required.
The malware deployment entails a decoy PDF file and executing obfuscated Python code.
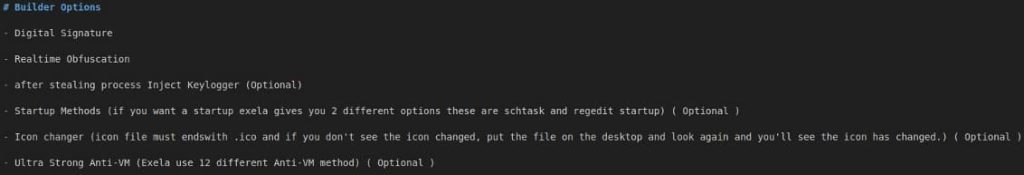
It can steal sensitive user data, including session data and cookies, credit card details, passwords, and keystrokes.
It can collect extensive system data, including WLAN profiles and firewall status.
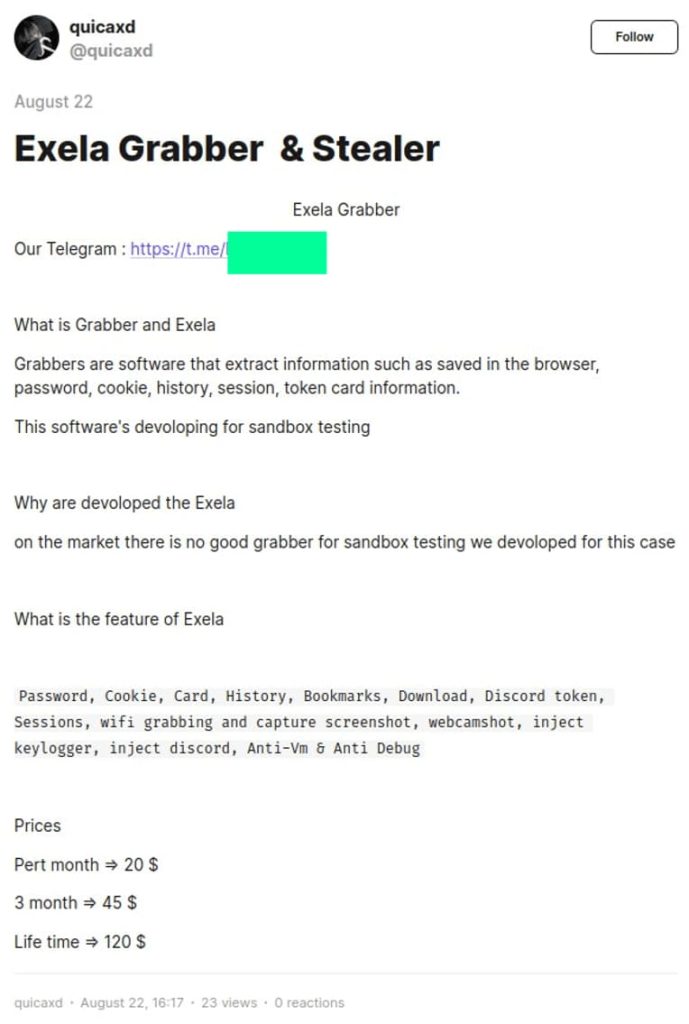
ExelaStealer is available in open-source and paid versions on the Dark web. The paid version comes with additional customization features.
ExelaStealer uses code obfuscation techniques to block analysis and reverse engineering efforts.
We have seen many infostealing malware emerging in cyberspace including Raccoon, RedLine, Vidar, and the relatively new entrant ThirdEye. However, the buzz in the cybersecurity world is that the yet-unknown ExelaStealer is far more dangerous than these.
The cybersecurity researchers at FortiGuard Labs discovered ExelaStealer in August 2023 and provided a detailed account of ExelaStealer’s workings in its new blog post. Per its research, the infostealer is offered as open-source and paid versions on the dark web, with the paid one featuring extended capabilities.
The malware is written in Python but often uses other language resources such as JavaScript. Windows-based systems are its key targets, whereas the malware looks for sensitive data such as passwords, session data, cookies, keystrokes, and credit card details.
Both versions of ExelaStealer are advertised on Dark Web forums with all the ads posted by a single contact using the handle “quicaxd.” For the paid version, the pricing structure varies. A monthly subscription is offered at $20, a three-month subscription is $45, and a lifetime subscription is $120.
It is worth noting that, according to FortiGuard Lab’s report, an active Telegram channel is used for facilitating purchases and getting access to the GitHub repository for the open-source version.
Given the infostealer’s open-source feature, it is possible for anyone with basic programming skills to create their own binaries using its source code. At the moment, ExelaStealer’s packaging and configuration are such that they can only affect Windows systems.
As per Fortiguard Labs, the binaries they analyzed have been released as part of a specific campaign, and the involvement of a decoy document further supports this assumption.
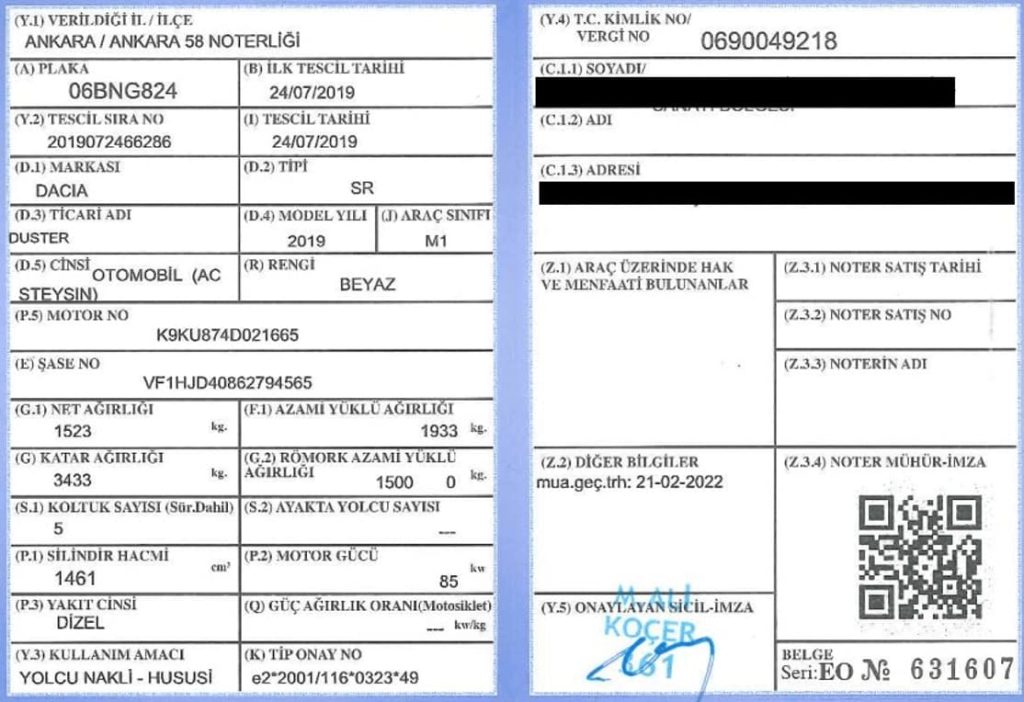
Researchers couldn’t identify the initial attack vector, but they suspect it could be achieved through malware deployment, watering holes, or phishing attacks. The binary is the attack’s first stage, which spawns an executable (sirket-ruhsat-pdf.exe) and launches a PDF viewer to display a decoy document titled ‘BNG 824 ruhsat.pdf’ to the user. Sirket-ruhsat-pdf.exe and BNG 824 ruhsat.pdf are planted into the C: drive’s root directory in which the former is a PyInstaller-generated file while the latter is a decoy file.
Regarding the attack stages, FortiGuard Labs researchers noted that the malware’s core functionality is embedded in a file titled Exela.py. The build process starts with a batch file that invokes Python and the ‘build.py’ file. The builder then uses a file titled ‘obf.py’ to hide the infostealer’s code and evade detection, reverse engineering, and analysis efforts.
Except for the library components, the obfuscated code is consolidated into a file titled ‘Obfuscated.py’ which is then deployed. The malware then starts gathering data along with executing a base64-encoded PowerShell command. The information is sent to the attacker’s Telegram channel, where the files are packaged into a ZIP archive and sent to a Discord webhook.
Look out for Watering Hole and Phishing Attacks
To protect yourself from ExelaStealer, users need to be on the lookout for watering holes and phishing attacks. A watering hole attack is a type of cyberattack in which the attacker identifies and compromises a website that is frequented by a particular group of individuals or organizations.
The goal of this attack is to infect the visitors’ computers with malware or exploit vulnerabilities in their systems. The term “watering hole” is derived from the concept of predators waiting near watering holes in the wild to ambush their prey when they come to drink.
To protect against watering hole attacks, individuals and organizations should regularly update their software, use strong security measures, and be cautious when visiting websites, especially those that might be of interest to potential attackers. Additionally, security solutions that can detect and block malicious activity are essential for identifying and mitigating such attacks.
KEY FINDINGS
- Formbook Takes the Throne as Most Prevalent Malware
- New version of Jupyter infostealer delivered through MSI installer
- Fake ChatGPT and AI pages on Facebook are spreading infostealers