ESET researchers have unveiled an espionage campaign called eXotic Visit. The campaign targets Android users by masquerading as benign messaging apps.
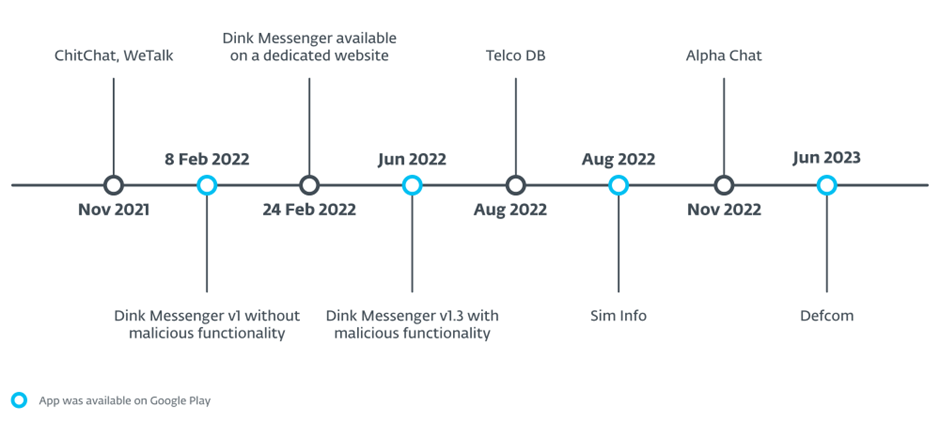
This campaign, active since late 2021, cleverly disguises the open-source XploitSPY malware within seemingly functional messaging services.
The primary victims of this sophisticated attack are located in India and Pakistan, marking a significant threat to their digital security landscape.

The eXotic Visit campaign has meticulously distributed malicious Android applications through dedicated websites and, for a period, via the Google Play store.

Although these apps have been removed from the Google Play store due to their low install numbers and malicious nature, the threat persists through other distribution channels.
Trustifi’s Advanced threat protection prevents the widest spectrum of sophisticated attacks before they reach a user’s mailbox. Stopping 99% of phishing attacks missed by
other email security solutions. .
The campaign’s focus on Android users in India and Pakistan highlights a targeted approach.
Approximately 380 victims have already been ensnared by the malware’s deceptive allure.
Technical Complications of XploitSPY
XploitSPY, the malware at the heart of this campaign, showcases a unique integration with the chat functionality of the impersonated messaging apps.
This integration is believed to be the work of the Virtual Invaders group, a moniker ESET researchers assigned to the unidentified threat actors behind this campaign.
The malware leverages a native library, commonly used in Android app development, for performance enhancement and system feature access.
However, in this malicious context, the library serves a more sinister purpose:
Concealing sensitive information such as the addresses of the Command and Control (C&C) servers.
This obfuscation tactic significantly complicates the analysis of the app by security tools, making the malware more elusive and dangerous.

The eXotic Visit campaign’s targeted nature, with a focus on Indian users, raises significant concerns about digital security in the region.
The impersonation of messaging apps—a digital communication staple—underscores modern cyber threats’ sophistication and deceptive capabilities.
Indian users, particularly those who frequently download apps from sources outside the Google Play store, are at an elevated risk of falling victim to this espionage campaign.
Prevention and Security Measures
To safeguard against threats like XploitSPY, users are advised to adhere to the following security measures:
- Download Apps from Reputable Sources: Limit app downloads to official app stores, such as Google Play, with stringent security checks.
- Stay Informed: Awareness of cyber threats can help users recognize and avoid potential dangers.
- Use Security Software: Installing reputable security software on Android devices can provide additional protection against malware.
- Check App Permissions: Be wary of apps that request unnecessary permissions, as this can be a red flag for malicious intent.
The discovery of the exotic Visit campaign and the XploitSPY malware it propagates is a stark reminder of the evolving landscape of cyber threats.
Users in India and globally must remain vigilant and adopt robust security practices to protect their digital lives.
As the battle against cybercrime continues, staying informed and prepared is our best defense.
Secure your emails in a heartbeat! To find your ideal email security vendor, Take a Free 30-Second Assessment.
