A sophisticated new variant of the macOS.ZuRu malware has emerged, targeting macOS users through a weaponized version of the popular Termius SSH client.
This latest iteration, discovered in late May 2025, represents a significant evolution in the threat actor’s tactics, moving beyond their traditional Baidu search engine poisoning campaigns to directly compromise legitimate applications used by developers and IT professionals.
The ZuRu malware family first surfaced in July 2021 when a Chinese blogger identified trojanized versions of popular macOS utilities being distributed through poisoned search results.
Initially targeting applications like iTerm2, SecureCRT, and Microsoft Remote Desktop, the malware has consistently focused on tools commonly used by backend developers and system administrators who require SSH and remote connection capabilities.
SentinelOne researchers identified this latest variant as part of their ongoing monitoring of macOS threats, noting significant technical improvements in the malware’s deployment methodology.
The threat actors have abandoned their previous dynamic library injection technique in favor of a more sophisticated approach that embeds malicious components directly within the target application’s helper processes.
%20and%20the%20trojan%20(bottom)%20with%20two%20extra%20binaries%20(Source%20-%20SentinelOne).webp)
The weaponized Termius application arrives as a disk image file measuring 248MB, noticeably larger than the legitimate 225MB version due to the embedded malicious binaries.
The attackers have replaced the original developer signature with their own ad hoc signature to circumvent macOS code signing requirements, demonstrating their understanding of Apple’s security mechanisms.
This evolution represents a concerning shift toward more direct application compromise, potentially bypassing traditional detection methods that focus on external library injection.
The malware’s continued success suggests that environments lacking robust endpoint protection remain vulnerable to these sophisticated social engineering attacks.
Infection Mechanism and Persistence Tactics
The malware employs a multi-stage infection process that begins with the modification of the legitimate Termius Helper.app component.
The original 248KB Termius Helper binary is renamed to .Termius Helper1, while a massive 25MB malicious replacement takes its place.
Upon execution, this trojanized helper launches both the original application to maintain normal functionality and the malware loader .localized to initiate the infection chain.
.webp)
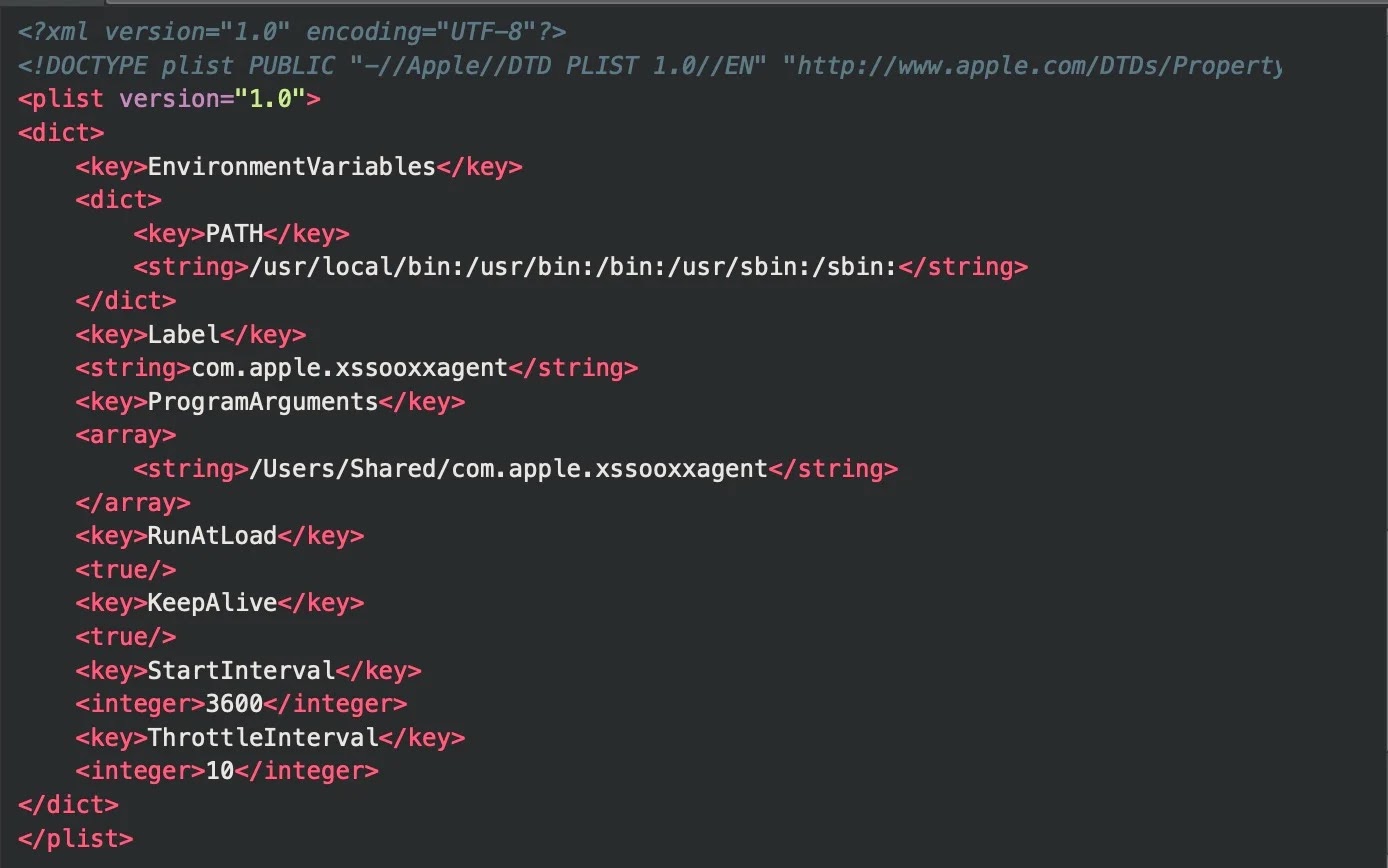
The loader establishes persistence by creating a LaunchDaemon with the label com.apple.xssooxxagent, scheduled to execute every hour from /Users/Shared/com.apple.xssooxxagent.
It downloads an encrypted payload from download.termius[.]info/bn.log.enc using the hardcoded decryption key my_secret_key, writing the decrypted Khepri C2 beacon to /tmp/.fseventsd.
The beacon maintains a rapid 5-second heartbeat with the command and control server at ctl01.termius[.]fun, using port 53 to blend with legitimate DNS traffic while employing www.baidu[.]com as a decoy domain.
Investigate live malware behavior, trace every step of an attack, and make faster, smarter security decisions -> Try ANY.RUN now
