Nike is investigating what it described as a “potential cyber security incident” after the World Leaks ransomware gang leaked 1.4 TB of files allegedly stolen from the sportswear giant.
“We always take consumer privacy and data security very seriously,” the company told BleepingComputer in an email statement. “We are investigating a potential cyber security incident and are actively assessing the situation.”
This comes after the extortion group added Nike to its dark web data-leak site, claiming it stole nearly 190,000 files containing corporate data providing information on Nike’s business operations.

Before this article was published, World Leaks removed the Nike entry from its leak, suggesting that it may be negotiating with the company or that Nike has already paid a ransom to have the allegedly stolen documents removed.
However, Nike has yet to confirm the extortion gang’s claims of data theft, and BleepingComputer couldn’t independently verify whether the leaked files contained legitimate data.
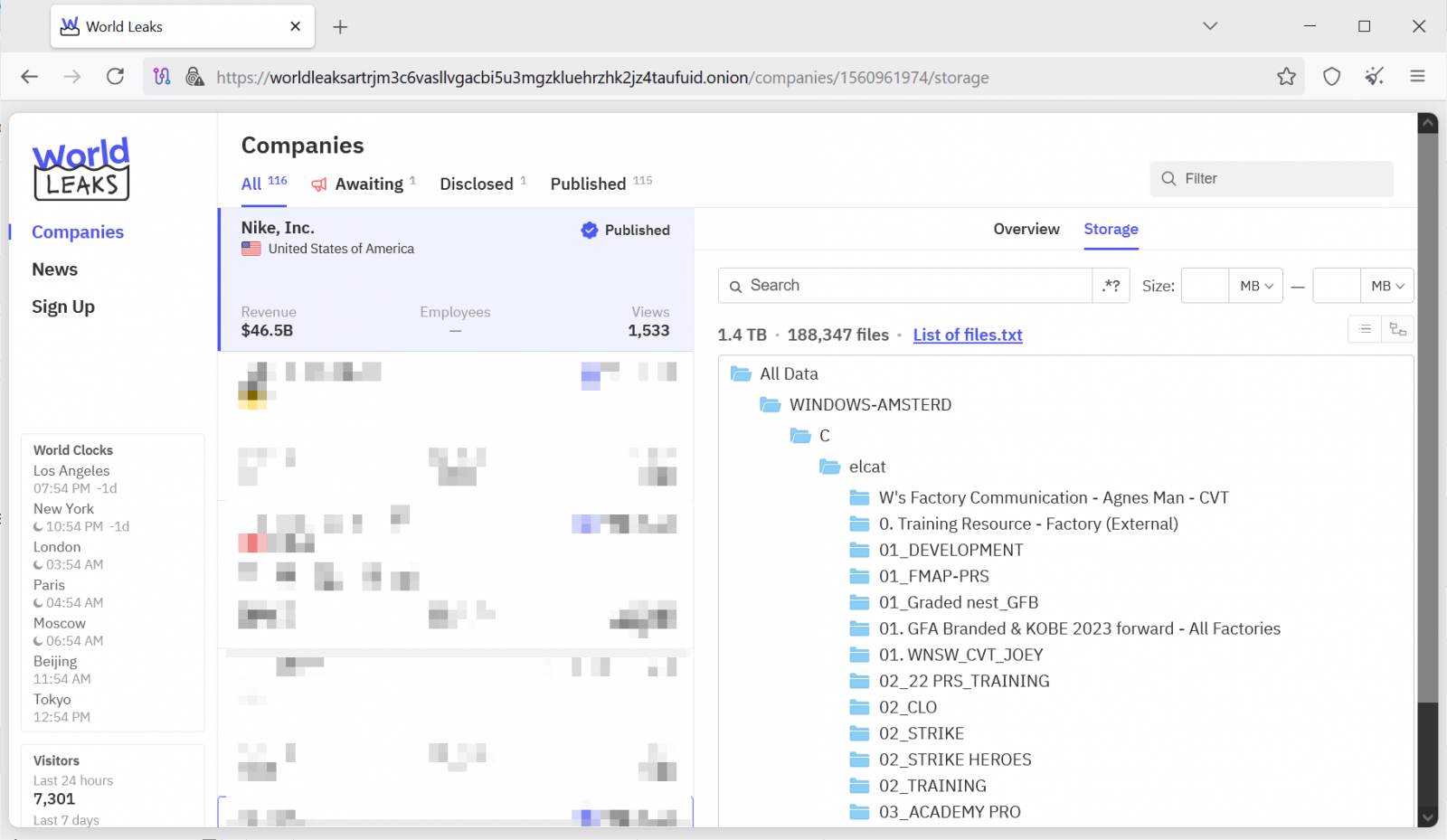
World Leaks is believed to be a rebrand of the Hunters International ransomware, following a switch from file encryption to data theft and extortion-only attacks in January 2025, citing concerns that ransomware operations were becoming too risky and were no longer profitable.
Hunters International emerged in late 2023 and was itself flagged as a possible Hive ransomware rebrand due to code similarities, after claiming responsibility for over 280 attacks.
The list of victims includes the U.S. Marshals Service, the Indian multinational tech giant Tata Technologies, the Japanese optics giant Hoya, the North American automobile dealership AutoCanada, and the U.S. Navy contractor Austal USA.
Since it surfaced, World Leaks has also published data stolen from dozens of organizations worldwide on its data leak site.
In July, World Leaks affiliates were linked to the breach of one of Dell’s product demonstration platforms and to the exploitation of end-of-life SonicWall SMA 100 devices to install custom OVERSTEP rootkit malware on compromised systems.

As MCP (Model Context Protocol) becomes the standard for connecting LLMs to tools and data, security teams are moving fast to keep these new services safe.
This free cheat sheet outlines 7 best practices you can start using today.
