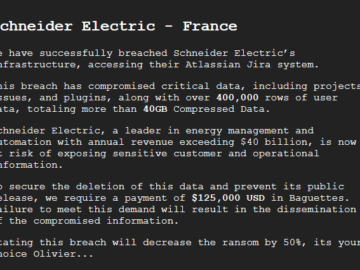
A new and powerful ransomware as a service (RAAS) has emerged and is marketing its prowess on the dark web.
Dubbed as NoBit RAAS builder, the malicious software is being promoted by an elusive threat actor and is being called the “hottest product” on the dark web.
The threat actor responsible for promoting NoBit RAAS builder is not holding back on its claims of destructive capabilities. The ransomware builder’s straightforward interface enables even novice hackers to easily create potent ransomware strains.
Creation and features of NoBit RAAS builder

One of the aspects of NoBit RAAS builder is its ability to encrypt virtually any file, leaving no data safe from its grasp.

This includes sensitive information tucked away in directories like the recycle bin and AppData, where users often store personal and important files.
Utilizing fast AES and SHA encryption algorithms, NoBit RAAS builder ensures swift and efficient encryption, causing chaos and panic in record time.
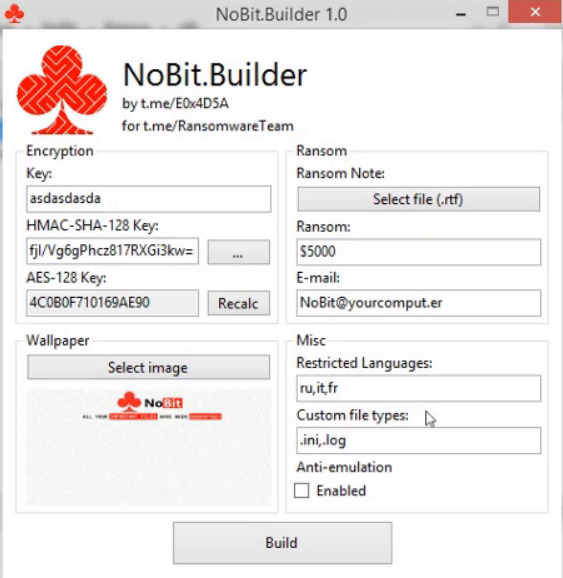
According to the threat actor’s post, the NoBit RAAS builder offers a range of powerful features that make it the weapon of choice for malicious actors.
For $200, users gain access to a lifetime license for the builder, allowing them to create unlimited ransomware strains. If they wish to explore the source code and delve into the program’s inner workings, it comes at a higher price tag of $1000.
The builder comes equipped with a range of essential blocks that users can manipulate to customize their ransomware.
Among these are a key block, an AES-128 key, and a wallpaper editor, allowing users to craft a unique and ominous message for their victims.
Additionally, there’s a ransom note block where users can draft and upload their demands in .rtf file format, specifying the ransom amount and the contact email for negotiating the payment.
A separate miscellaneous section allows users to omit language restrictions, ensuring that the ransom demand reaches a wide audience.
Modus Operandi of NoBit RAAS builder
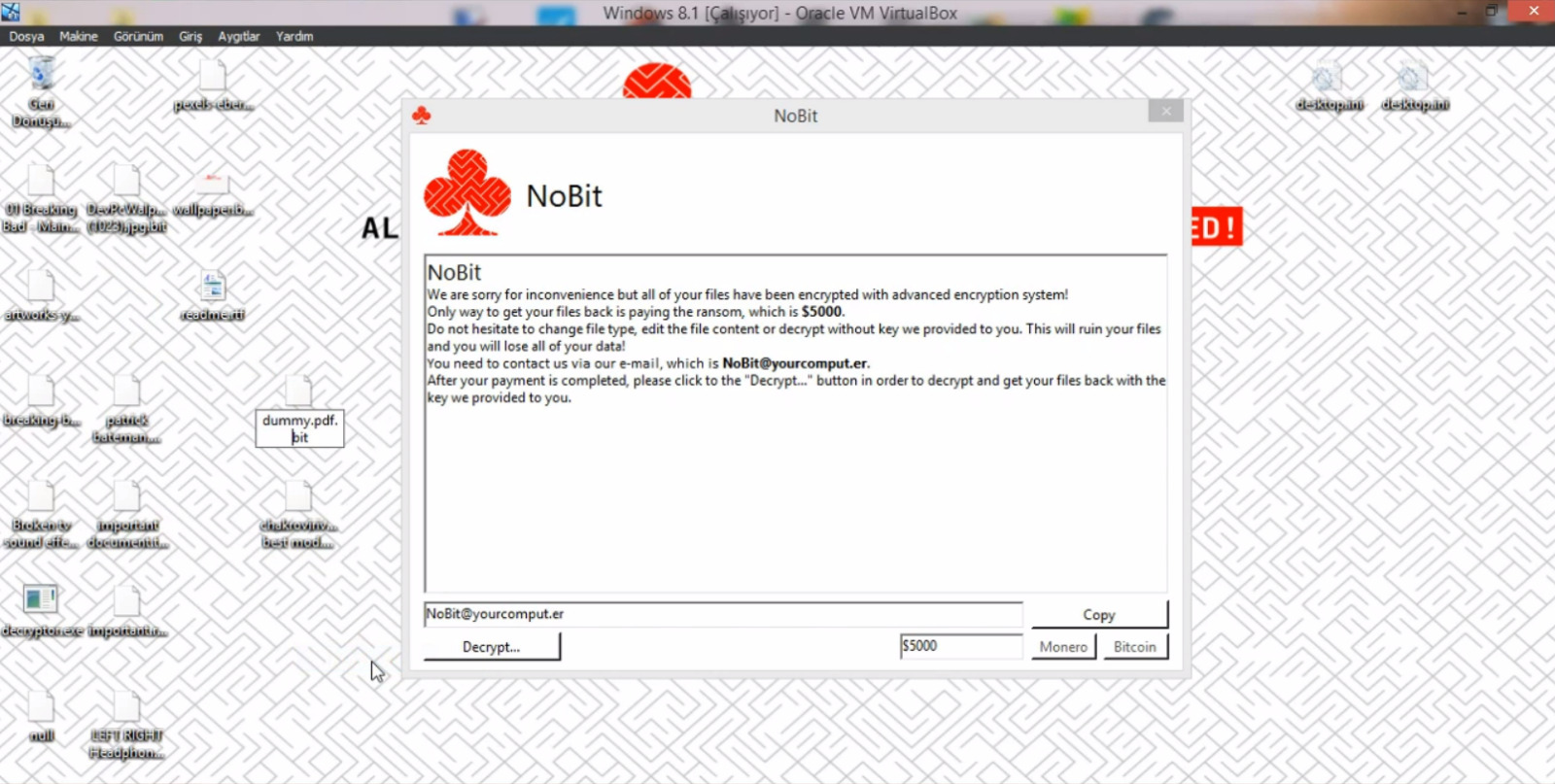
Once the NoBit RAAS attack has been successfully executed on a victim’s computer, a threat message is displayed on the desktop, leaving them with very few options.
The message explicitly states that all their files have been encrypted using an advanced encryption system, and the only way to regain access to their precious data is by paying the hefty ransom of $5000.
The threat actors are cunning enough to warn victims against changing file types, editing the content, or decrypting the files without the provided key, as it could lead to irreversible data loss.
The contact email, [email protected], serves as the point of contact between the victims and the malicious actors. Once the payment is made, victims are instructed to click the “Decrypt…” button to initiate the decryption process using the provided key.
NoBit RAAS builder is a dangerous and sophisticated ransomware as a service that highlights the increasing sophistication of cybercriminals.
Since NoBit RAAS builder is active on the dark web marketplaces, threat actors might want to invest in this service to create ransomware strains, which can later be used to target unsuspecting victims.
Apart from RAAS builders, leaked code also come handy for cybercriminals.
Researchers have been finding instances of cybercriminals reusing the code of long gone ransomware group Babuk.
Newbie threat actor RA Group is the latest ransomware player in the list, noted Cisco Talos researchers.
This group has taken advantage of the leaked Babuk ransomware source code to create its own variant of the malicious software, adding to the growing concern of ransomware attacks.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.