Nokoyowa Leaks, the official communication channel for the Nokoyowa ransomware group, has re-emerged on the darkweb, revealing a distressing list of 24 new victims.
Interestingly, some of these victims overlap with those targeted by the infamous Snatch ransomware group, raising questions about a potential connection between these malicious entities.
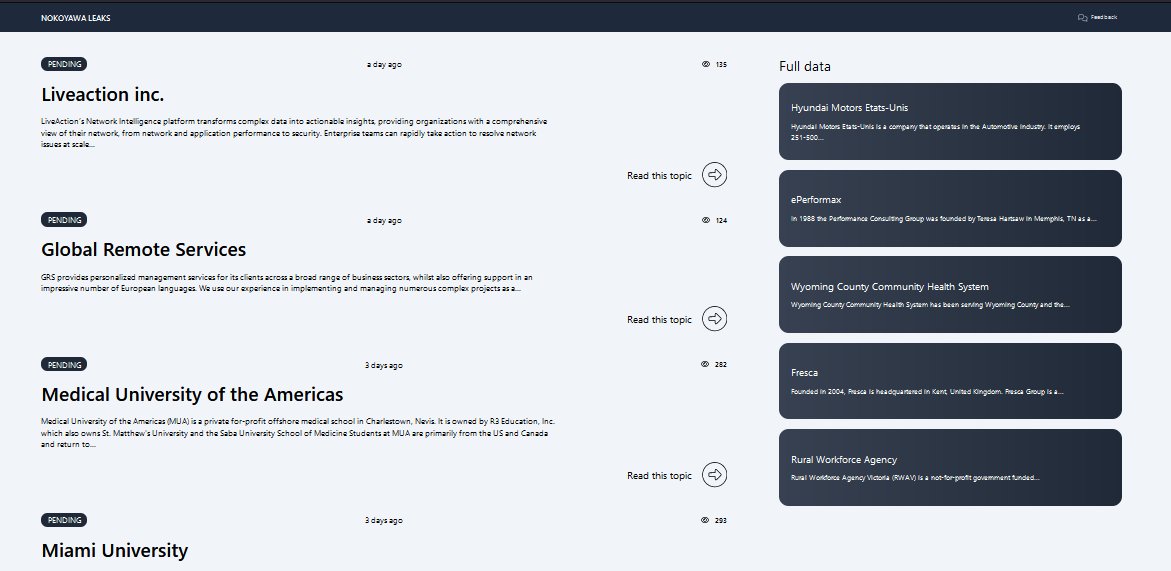
The Nokoyowa ransomware gang disclosed a list of victims, which includes notable companies such as:
- CONEX
- Miescor
- MSX International
- Gaston College
- City of Modesto
- Pueblo Mechanical & Controls
- Comcom-sgc
- Guardian Fine Art Services
- Accurate Auto Insurance
- Stockmann Natursteine & Fliesen
- Snodland C of E Primary School
- Sabin
- Canadian Nurses Association
- Rural Workforce Agency
- Fresca
- Canopy Children’s Solutions
- Wyoming County Community Health System
- ePerformax
- Hyundai Motors Etats-Unis
- Chattanooga State Community
- Miami University
- Medical University of the Americas
- Global Remote Services
- Liveaction Inc.
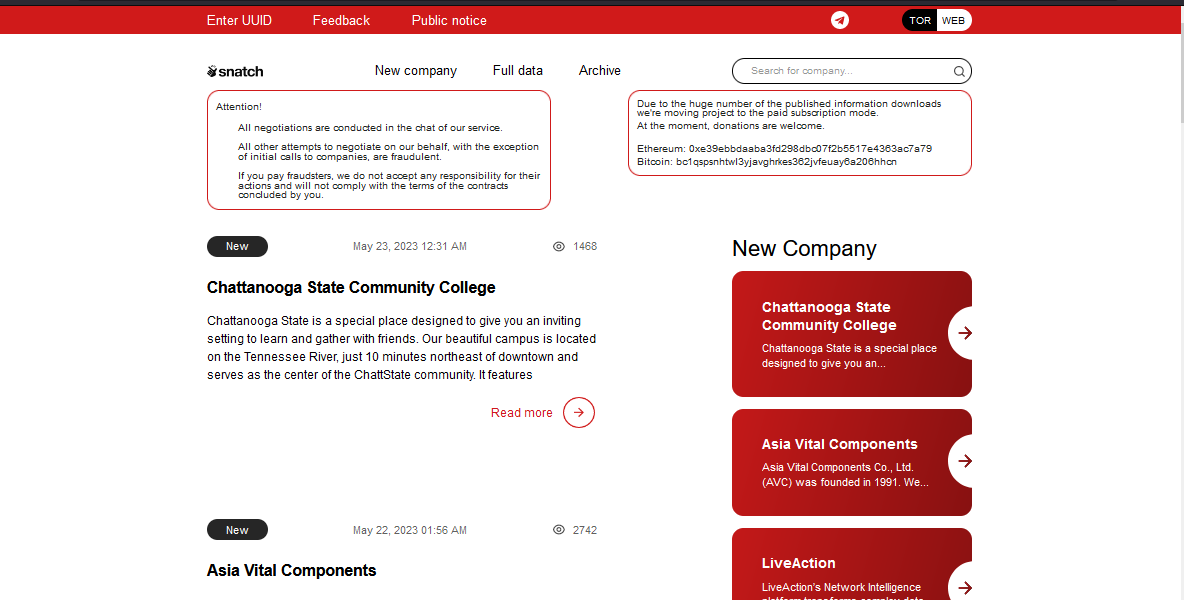
The Cyber Express found that eight of these victims — MSX International, Gaston College, City of Modesto, Canadian Nurses Association, Fresca, Chattanooga State Community, Miami University, Liveaction Inc– were earlier claimed by Snatch, some just a day ago.

Unraveling the connection between Nokoyowa Leaks and the Snatch
Considering the origins and the history of Nokoyowa, a potential partnership between them and the Snatch ransomware group cannot be dismissed as coincidence.
However, experts from Cyble refrained from terming Snatch as a ransomware group, but acknowledged their history of extortion. It often markets stolen data on its leaked site, the researchers told The Cyber Express.
“Snatch is not a ransomware group. They are extortion group and many a times just market data on their leak site,” a Cyble threat intelligence researcher told The Cyber Express.
According to the researcher, Nokoyowa’s claims of breaching organizations appear bogus.
While Nokoyowa was relatively unknown until recently, it gained attention following a March 2022 report by Trend Micro, a leading cybersecurity firm, linking them to the Hive ransomware family.
According to the report, there are striking similarities in the attack patterns, tools utilized, and the sequential execution of steps employed by both Nokoyowa and Hive.
These findings suggest a possible connection between the two groups, hinting at a complex collaboration network among cyber criminals.
Nokoyowa primarily focuses its operations in South America, particularly emphasizing Argentina as its primary target.
This regional concentration underscores the urgent need for strengthened cybersecurity measures and enhanced collaboration among organizations and law enforcement agencies in the affected areas.
Who is the Nokoyowa ransomware gang?
Nokoyowa ransomware is a malware strain that emerged in February 2022, capable of targeting 64-bit Windows-based systems in double extortion attacks.
The group behind Nokoyowa ransomware employs a two-pronged approach: first, they exfiltrate sensitive information from organizations, then encrypt files and demand a ransom payment.
In April 2023, Kaspersky Technologies detected multiple attempts to exploit elevation-of-privilege vulnerabilities in Microsoft Windows servers belonging to small and medium-sized businesses in the Middle East, North America, and previously in Asia.
During one such attack, Kaspersky identified the CVE-2023-28252 vulnerability, where cybercriminals attempted to deploy an updated version of Nokoyowa ransomware.
Sophisticated cybercriminal groups have exploited this vulnerability to deploy Nokoyowa ransomware as the final payload.
Microsoft promptly addressed the actively exploited CVE-2023-28252 vulnerability and released a patch to mitigate the risk. As of May 2023, threat actors have shifted their focus to alternative means of initial access, such as ISO files.
As the alarming activities of Nokoyowa Leaks and the Snatch ransomware group continue, organizations and individuals must remain vigilant and implement robust cybersecurity measures.
Collaboration among stakeholders, including law enforcement agencies, cybersecurity firms, and affected organizations, is paramount in the battle against these cyber threats.
By staying informed and adopting proactive security strategies, we can effectively combat the perils posed by Nokoyowa ransomware and safeguard our digital infrastructure.
Media Disclaimer:
This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
