The NoName hacker group has allegedly carried out a cyber attack on Sweden, particularly the websites of the Swiss Parliament and the Swedish company SSG Standard Solutions Group.
Reports from threat intelligence service Falcon Feed suggest that the hacker group has claimed responsibility for the attacks, accompanied by two images showing the victim websites being inaccessible.
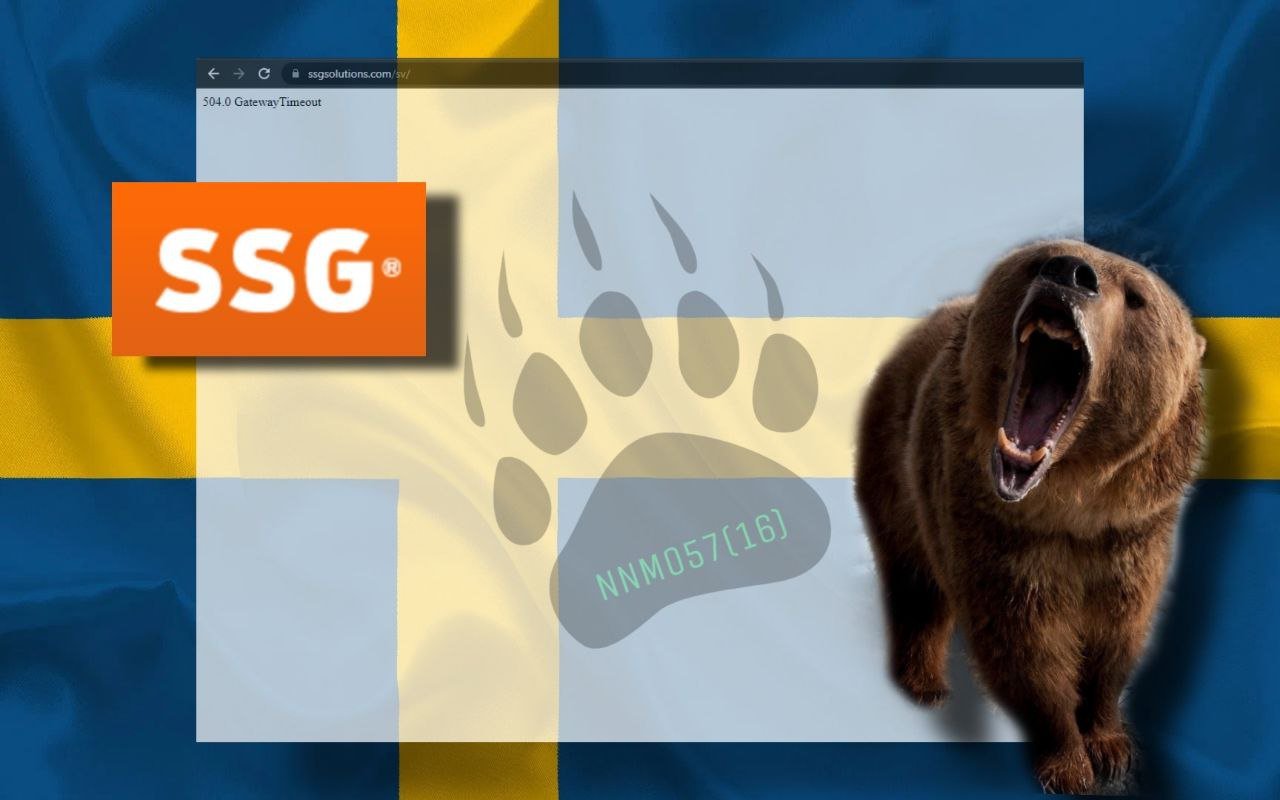
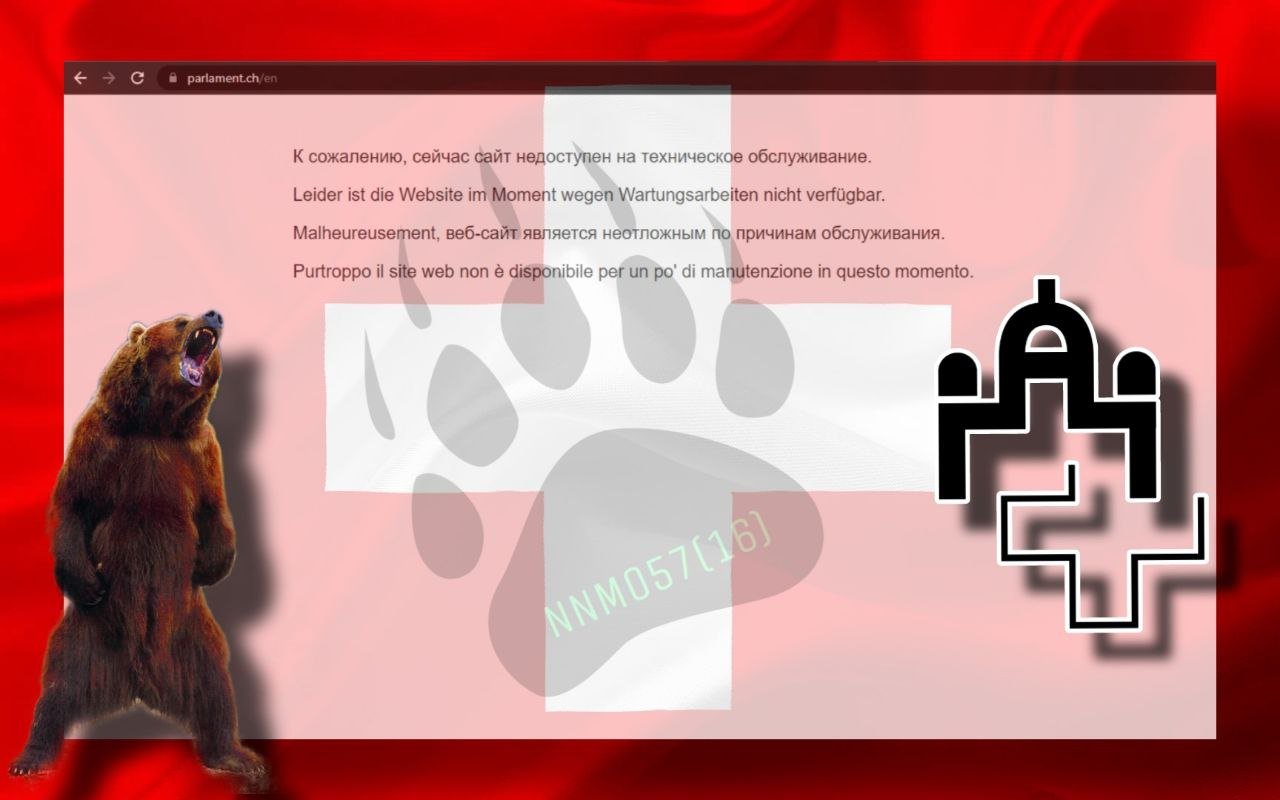
It has been verified that the websites of the Swiss Parliament and SSG were affected, resulting in unavailability. and the display of error messages such as “ERR_CONNECTION_TIMED_OUT” and “HTTP Error 503.”
The Cyber Express has reached out to the Swiss Parliament and SSG to verify the authenticity of these claims. We will update the report on receiving their response.

Cyber attack on Sweden: Victims continue to increase
The recent attack on Sweden’s parliament and SSG is the latest in the list of geopolitical hacking incidents in Sweden.
On June 3, Swiss authorities investigated another cyber attack on Sweden, wherein the threat actors targeted the IT company Xplain, which served government departments as its clients.
The PLAY ransomware group claimed responsibility for this attack, prompting Xplain to report the incident and collaborate with the National Cyber Security Centre to mitigate the damage.
No ransom was paid to the threat actor, and the full extent of the breach remains uncertain. It is worth noting that Xplain did not store applications and data, and the Federal Office of Customs and Border Security confirmed that their data remained unaffected by the attack.
Apart from launching multiple cyber attacks on Sweden, the notorious ransomware gang claimed responsibility for a cyber attack on the Danish Parliament.
Understanding cyber attack on Sweden
The NoName hacker group has been devising new methods to recruit hackers aligned with their objectives. They have taken to their Telegram channel to reach out to potential volunteers, urging them to participate in their activities.
The primary focus of these activities involves carrying out Distributed Denial of Service (DDoS) attacks on entities critical of the Russian invasion of Ukraine.
Volunteers in NoName’s “DDosia” campaign are promised compensation of up to 80,000 Rubles (approximately $1,200) in cryptocurrency for successfully executed attacks.
This recruitment tactic highlights the group’s evolving strategies in leveraging social media platforms to attract individuals and recruit hacktivists.
The ongoing conflict between Russia and Ukraine has fueled online activism on both sides.
Avast, a leading cybersecurity company, discovered that social media platforms have become breeding grounds for individuals rallying others to download DDoS tools and launch attacks on Russian websites that support Ukraine.
Since the conflict began, users in countries such as Canada and Germany have attempted to download the DDosia executable file, aiming to carry out DDoS attacks while bypassing anti-malware software exceptions on their computers.
This emerging trend emphasizes the global nature of cyber warfare and underscores the need for enhanced vigilance in safeguarding critical online infrastructure.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
