Ukraine has become the battleground for a cyber onslaught, with the NoName ransomware attack claiming responsibility for a series of attacks on various entities.
The NoName ransomware attack has specifically targeted prominent organizations in Ukraine, as revealed by the threat actor on their dark web portal. The list includes the National Securities and Stock Market Commission, Accordbank, Unex Bank, Energy Community, and VELTA.
The dark web message from the threat actor reads, “Today we went to the Ukrainian segment of the internet,” indicating a brazen intrusion into the country.
NoName Ransomware Attack
The NoName ransomware group further substantiated their claims by posting links to check-host.net reports for each targeted entity. However, the authenticity of these NoName ransomware cyberattack claims remains unverified at this time.
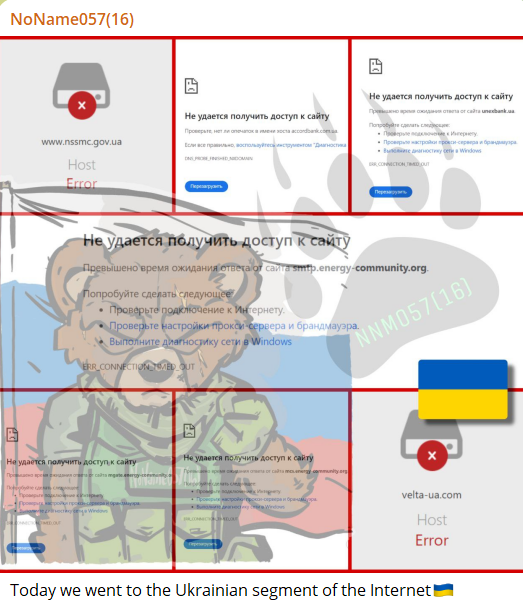
The Cyber Express has reached out to the affected organizations for confirmation, yet no official statements or responses have been received as of the time of writing.

Adding to the complexity of the situation, the entities listed on the threat actor’s portal appear to be operational and show no immediate signs of the alleged cyberattack. This uncertainty heightens the challenge of verifying the legitimacy of the NoName ransomware cyberattacks on Ukraine.
NoName057(16), the pro-Russian hacker group behind the cyber onslaught, has a history of targeting Ukrainian, American, and European websites belonging to government agencies, media, and private companies. Described as an unorganized yet free pro-Russian activist group, NoName057(16) seeks attention in Western countries through its disruptive cyber activities.
The rise of NoName Ransomware Group
The group first emerged in March 2022, orchestrating Distributed Denial of Service (DDoS) attacks on Ukrainian news and media websites, such as Zaxid and Fakty UA. Their motivations are rooted in silencing voices perceived as anti-Russian, reflecting the broader geopolitical tensions in the region.
Operating through Telegram channels, NoName057(16) utilizes GitHub to host its DDoS tool website and associated repositories. The group has developed a DDoS tool named DDOSIA, designed to execute denial-of-service attacks by inundating target sites with repeated network requests.
Within the global hacking collective landscape, NoName057(16) is a relatively new entrant with a distinct focus on disrupting Ukrainian digital infrastructure. Their prominence rose after a series of cyberattacks on government websites on the eve of the 2023 G20 Summit in India, marking a pivotal moment in their operations.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
