In a recent cyber assault attributed to the notorious NoName ransomware group, various websites across the UK have fallen victim. The motives behind this attack remain obscure, consistent with the group’s history of indiscriminate cyber assaults on its targets.
This latest onslaught has ensnared a multitude of organizations in the UK, including Transport for Edinburgh, Nexus, Brighton & Hove Buses, West Yorkshire Metro, Oxford Bus Company, Travel South Yorkshire, Edinburgh Trams, Swiftcard, and MERSEY FERRIES LIMITED.
NoName ransomware group launches new cyber attack campaign
The infamous NoName ransomware group has launched a renewed cyber attack campaign, further cementing its status as a rapidly ascending threat actor in the dark web world. Their latest offensive focuses on high-profile organizations, as they continue to outpace other cyber adversaries.
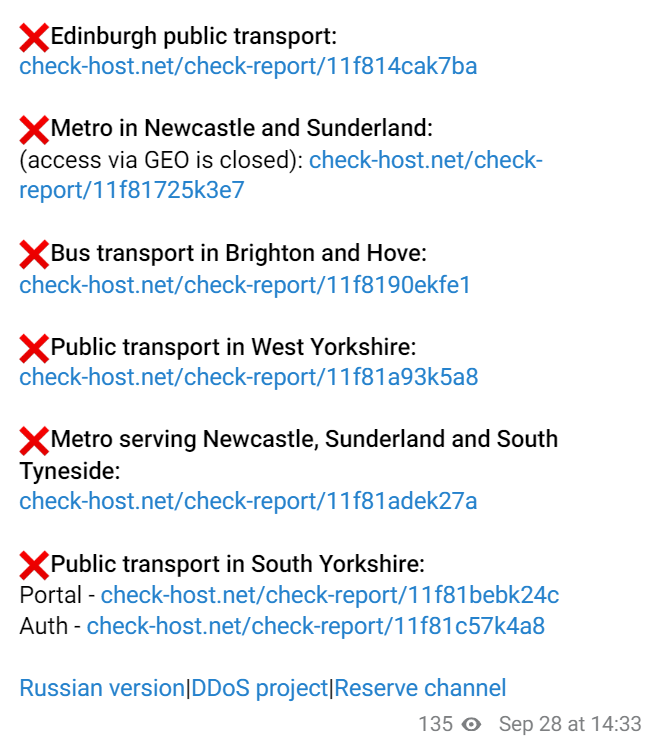
To affirm their claims, the threat actor released a subsequent message, including multiple check-host links for verification. The post provides specific targets for their attacks, zeroing in on critical public transportation infrastructure across various regions:

- Edinburgh public transport
- Metro in Newcastle and Sunderland (access via GEO is closed):
- Bus transport in Brighton and Hove
- Public transport in West Yorkshire
- Metro serving Newcastle, Sunderland, and South Tyneside:
- Public transport in South Yorkshire
Moreover, the group disclosed a Russian version, a DDoS project, and a reserve channel, emphasizing their sophisticated and multi-pronged approach to cyber warfare. This announcement was timestamped at 14:33 on September 28th.
NoName ransomware group cyber attack spree
Over the past few months, the NoName ransomware group has taken responsibility for a string of cyber attacks, firmly establishing itself as one of the fastest-growing threats in the dark web landscape. Their relentless focus on high-profile targets highlights a level of audacity and expertise that sets them apart from their competitors.
As this brazen campaign unfolds, the cybersecurity community must remain vigilant in its efforts to safeguard critical infrastructure and combat the tactics of groups like NoName057. The stakes are higher than ever, and proactive measures are imperative in the ongoing battle against cyber threats.
The Cyber Express attempted to reach out to some of the affected organizations listed. However, as of the time of writing, no official statements or responses have been received, leaving the veracity of the NoName cyber attack claims unverified.
Nevertheless, a claim of a cyber attack by the NoName ransomware group warrants serious consideration. Researchers have identified them as a lone-wolf DDoS group, known for launching distributed denial-of-service (DDoS) attacks on European financial institutions, government websites, and transportation services every morning, like clockwork.
NoName057(16) emerged as a Pro-Russian hacker group in March 2022, asserting responsibility for cyber attacks on government agencies, media, and private companies’ websites in Ukraine, the United States, and Europe. It’s characterized as an unstructured pro-Russian activist group seeking attention in Western nations.
Their initial attacks in March 2022 consisted of DDoS assaults on Ukrainian news and media websites like Zaxid and Fakty UA. Their motivations predominantly revolved around suppressing what they deemed as anti-Russian sentiment.
Operating through Telegram channels, NoName057(16) claims responsibility for their attacks, taunts their targets, issues threats, and disseminates educational content. They’ve also utilized GitHub to host their DDoS tool website and related repositories. Their DDoS tool, named DDOSIA, executes denial-of-service attacks by repeatedly bombarding target sites with network requests.
Ukrainian media personnel have received menacing missives from the NoName057(16) group, a fact confirmed by former Ukrainian Ombudsman Lyudmila Denisova. OSINT researcher Cyberknow20 has included NoName ransomware group in his comprehensive roster of hacker groups, which he periodically updates.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
