A sophisticated North Korean cyber operation has been exposed, revealing how state-sponsored hackers systematically monitor cybersecurity intelligence platforms to detect when their malicious infrastructure is discovered and rapidly deploy replacement assets to maintain operations.
The analysis, conducted by SentinelLABS in collaboration with Validin, provides unprecedented insight into the operational practices of threat actors behind the Contagious Interview campaign cluster.
The investigation uncovered that North Korean threat actors operate in coordinated teams with real-time collaboration capabilities, likely utilizing platforms such as Slack alongside multiple intelligence sources including Validin, VirusTotal, and Maltrail.
Despite being aware that their infrastructure is detectable by security researchers, the actors make only limited changes to reduce detection risk while rapidly deploying new infrastructure in response to service provider takedowns.
This approach indicates a strategic focus on continuously replacing disrupted infrastructure with fresh assets rather than investing resources in protecting existing ones.
The threat actors appear to prioritize maintaining operational readiness and sustaining high victim engagement over comprehensive infrastructure protection.
The Contagious Interview campaign primarily targets individuals in the cryptocurrency and blockchain industries, using sophisticated social engineering techniques known as ClickFix.
The attack methodology involves threat actors posing as recruiters who invite job seekers to participate in skill assessments on fabricated websites.
During these assessments, victims encounter fake error messages prompting them to execute command lines that unknowingly download and install malware.
Between January and March 2025, SentinelLABS identified over 230 victims who engaged with these fraudulent employment offers, though researchers believe the actual number is significantly higher.
The victims span multiple countries and work primarily in marketing and finance roles within cryptocurrency companies.
Coordinated Intelligence Gathering
The research revealed that North Korean actors began creating accounts on the Validin threat intelligence platform within 24 hours of a blog post about Lazarus APT infrastructure published on March 11, 2025.
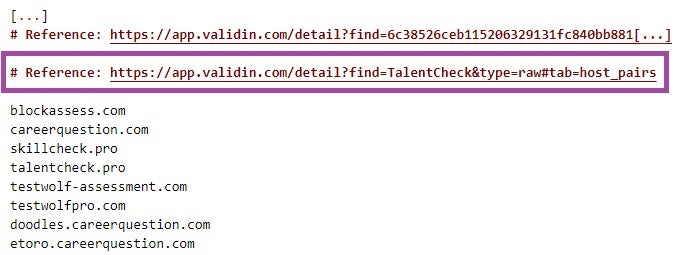
The threat actors registered multiple accounts using Gmail addresses that researchers had already identified as campaign artifacts, demonstrating their systematic approach to intelligence collection.
Analysis of user activity patterns showed the actors searched for 57 unique terms across various categories, including domain names, hashes, URLs, and IP addresses.
Significantly, they did not search for indicators mentioned in the original blog post that triggered their interest, suggesting they use Validin as part of a broader intelligence workflow incorporating multiple sources.
Despite their sophisticated intelligence gathering capabilities, the threat actors demonstrated consistent operational security failures during infrastructure deployment.
Researchers observed multiple instances of exposed files and directory contents, including error logs and victim information databases.
For most of the domains they searched, the threat actors visited every available external reference, demonstrating a determined effort to conduct thorough CTI investigations by gathering information from multiple sources.
![Reconstructed navigation path of the jimmr6587[@]gmail.com account.](https://www.sentinelone.com/wp-content/uploads/2025/07/ContInt_Validin_July2025_12.jpg)
The exposed data included ContagiousDrop applications – Node.js-based tools that deliver operating system-specific malware while logging victim information and sending email notifications to threat actors about successful engagements.
These applications effectively create comprehensive databases of victim interactions across multiple attack stages.
The limited scope of infrastructure changes, despite thorough threat intelligence examination, suggests several factors may constrain the threat actors’ defensive capabilities.
Researchers hypothesize that decentralized command structures and competitive internal incentives may limit coordinated infrastructure protection efforts.
North Korea’s annual revenue quotas for cyber teams likely create competitive pressures that incentivize operatives to make isolated adjustments protecting their individual assets rather than participating in centrally coordinated updates.
This internal competition may explain why the actors focus on rapidly replacing compromised infrastructure rather than implementing comprehensive protective measures.
Global Impact and Industry Response
The campaign’s targeting of cryptocurrency industry professionals aligns with North Korea’s broader sanctions evasion and revenue generation objectives.
These security lapses provided valuable insights into the campaign’s victimology and operational timelines.
The exposed timestamps provide insight into when the Contagious Interview operators deployed content to the server, allowing us to reconstruct their activity timeline.
![Exposed web root directory of api.release-drivers[.]online.](https://www.sentinelone.com/wp-content/uploads/2025/07/ContInt_Validin_July2025_4-768x296.jpg)
The threat actors impersonate legitimate companies including Archblock, Robinhood, and eToro, offering positions such as Portfolio Manager and Investment Manager to lure victims.
The research emphasizes the critical role of infrastructure service providers in disrupting these operations through continuous takedown efforts.
Close collaboration between service providers and the threat intelligence community has proven effective in reducing the actors’ operational capacity, though the threat actors’ rapid infrastructure replacement capabilities present ongoing challenges.
Security researchers stress the importance of the human factor in mitigating these threats. Job seekers, particularly within the cryptocurrency sector, should exercise heightened vigilance when engaging with unsolicited employment offers and associated skill assessments.
Red flags include requests to execute command-line instructions during application processes and assessments hosted on unfamiliar domains.
The investigation demonstrates how North Korean threat actors have adapted their operations to the modern threat intelligence landscape, using the same tools and platforms employed by defenders to monitor and evade detection efforts.
This cat-and-mouse dynamic underscores the need for continuous innovation in defensive strategies and improved coordination between public and private sector cybersecurity efforts.
As cyber operations become increasingly sophisticated, this research provides valuable insights into adversary decision-making processes and highlights the ongoing challenge of protecting critical infrastructure against persistent, well-resourced threat actors operating with state backing.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.



