The North Korean hacker collective Lazarus, infamous for having carried out numerous large-scale cryptocurrency heists over the years, has switched to using YoMix bitcoin mixer to launder stolen proceeds.
According to a report from blockchain analysis company Chainalysis, Lazarus has adapted its laundering process after governments sanctioned multiple bitcoin mixing services the threat actor used.
The firm says that YoMix has seen a massive influx of funds throughout 2023, that are not attributed to popularity increase but rather Lazarus activity.
Lazarus laundering ops
Crypto-theft is just one aspect Lazarus operations, albeit a very important part of its activities, which is believed to fund not only the group’s operations but also North Korea’s weapons development program.
Some of the largest cryptocurrency theft operations Lazarus conducted in recent years include the March 2022 Ronin Network (Axie Infinity) hack that yielded $625 million, the Harmony Horizon hack in June 2022 that resulted in losses of $100 million, and the July 2023 Alphapo heist from where the hackers pocketed $60 million worth of crypto.
From January 2017 until December 2023, North Korean hacking groups, including Lazarus, Kimsuky, and Andariel, have stolen an estimated $3 billion in crypto, according to a report from Recorded Future.
The money went through various coin mixing services that don’t abide by anti-laundering regulations and accept deposits even from wallets flagged for suspicious activity.
The mixers bounce the assets through an obfuscated network of cryptocurrency holders and receive them in new wallet addresses that cannot be traced to the original attacks.
Over the years, the U.S. Treasury Department’s Office of Foreign Assets Control (OFAC) identified and sanctioned some of the platforms Lazarus used for laundering their proceeds, including Blender, Tornado Cash, and Sinbad.
However, every time a platform was sanctioned and isolated from the crypto space, Lazarus moved to a new one. Chainalysis says YoMix is the latest service used by the North Korean threat actor.
2023 laundering trends
Chainalysis reports that YoMix saw a massive growth of funds in the second quarter of 2023, sustained until the end of the year, which is mostly attributed to money laundering.
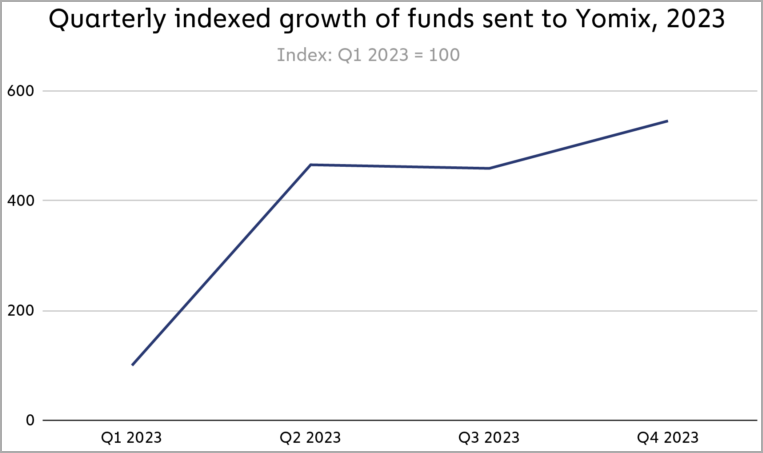
“Based on Chainalysis data, roughly one-third of all YoMix inflows have come from wallets associated with crypto hacks,” reads the report.
“The growth of YoMix and its embrace by Lazarus Group is a prime example of sophisticated actors’ ability to adapt and find replacement obfuscation services when previously popular ones are shut down” – Chainalysis
Chainalysis also says that last year it noticed a trend concerning the concentration of money laundering activities at a few fiat off-ramping services, with 71.7% of all illicit funds directed to just five services.
However, at the deposit address level, money laundering became less concentrated, suggesting that criminals are diversifying their activities to avoid detection and the freezing of assets by law enforcement and compliance teams.
Other highlights from the report include:
- Flagged crypto wallet addresses sent $22.2 billion to services in 2023, a decrease from $31.5 billion in 2022.
- 109 exchange deposit addresses received over $10 million worth of illicit cryptocurrency each in 2023, collectively receiving $3.4 billion in illicit cryptocurrency.
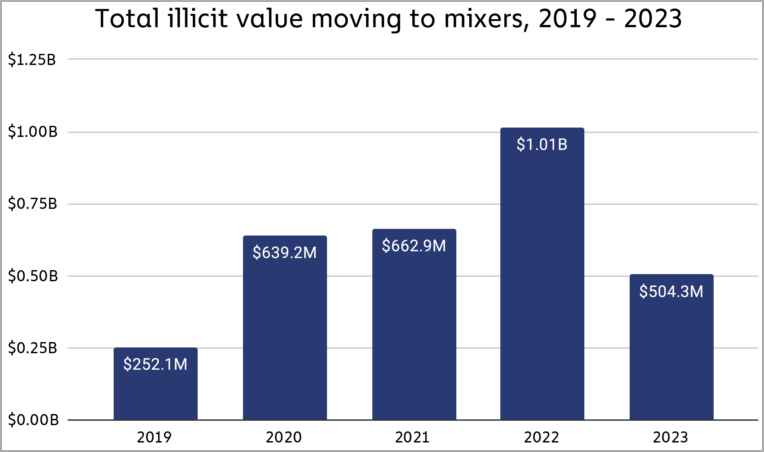
- Last year, the funds sent to mixers from flagged addresses was 504.3 million, down 50% from $1 billion in 2022.
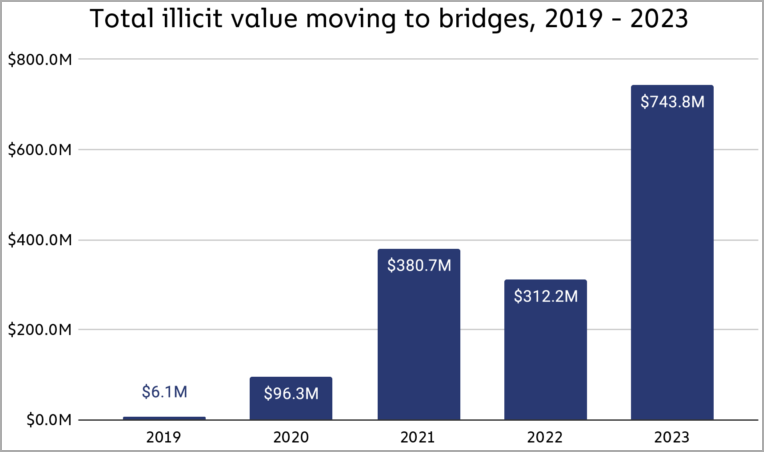
- Cross-chain bridge utilization has shown significant growth in 2023, with $743.8 million in crypto received, compared to $312.2 million in 2022.
BleepingComputer has contacted YoMix with a request for a comment about the service being used by North Korean hackers to laundering illegal funds but we are yet to receive a response.


