The North Korean state-sponsored hacking group ScarCruft has been linked to a cyberattack on the IT infrastructure and email server for NPO Mashinostroyeniya, a Russian space rocket designer and intercontinental ballistic missile engineering organization.
NPO Mashinostroyeniya is a Russian designer and manufacturer of orbital vehicles, spacecraft, and tactical defense and attack missiles used by the Russian and Indian armies. The U.S. Department of Treasury (OFAC) has sanctioned the company since 2014 for its contribution and role in the Russo-Ukrainian war.
Today, SentinelLabs reported that ScarCruft is behind a hack of NPO Mashinostroyeniya’s email server and IT systems, where the threat actors planted a Windows backdoor named ‘OpenCarrot’ for remote access to the network.
While the main purpose of the attack is unclear, the ScarCruft (APT37) is a cyber espionage group known to surveil and steal data from organizations as part of their cyber campaigns.
Discovering the breach
The security analysts discovered the breach after analyzing an email leak from NPO Mashinostroyeniya that contained highly confidential communications, including a report from IT staff warning of a potential cybersecurity incident in mid-May 2022.
SentinelLabs leveraged the information in these emails to undertake an investigation, discovering a much more significant intrusion than the missile maker realized.
Source: SentinelLabs
According to the leaked emails, IT staff at NPO Mashinostroyeniya discussed suspicious network communication between processes running on internal devices and external servers.
This ultimately led to the company finding a malicious DLL installed on internal systems, causing them to engage with their antivirus firm to determine how they had become infected.
After analyzing the IP addresses and other indicators of compromise (IOCs) found in the emails, SentinelLabs determined that the Russian organization was infected with the ‘OpenCarrot’ Windows backdoor.
A link to Lazarus
OpenCarrot is a feature-rich backdoor malware previously linked to another North Korean hacking group, the Lazarus Group.
While it is not clear if this was a joint operation between ScarCruft and Lazarus, it is not uncommon for North Korean hackers to utilize tools and tactics that overlap with other state-sponsored threat actors in the country.
The variant of OpenCarrot used in this particular attack was implemented as a DLL file, supports proxying communications through internal network hosts.
The backdoor supports a total of 25 commands, including:
- Reconnaissance: File and process attribute enumeration, scanning, and ICMP-pinging hosts in IP ranges for open TCP ports and availability.
- Filesystem and process manipulation: Process termination, DLL injection, file deletion, renaming, and timestamping.
- Reconfiguration and connectivity: Managing C2 communications, including terminating existing and establishing new comms channels, changing malware configuration data stored on the filesystem, and proxying network connections.
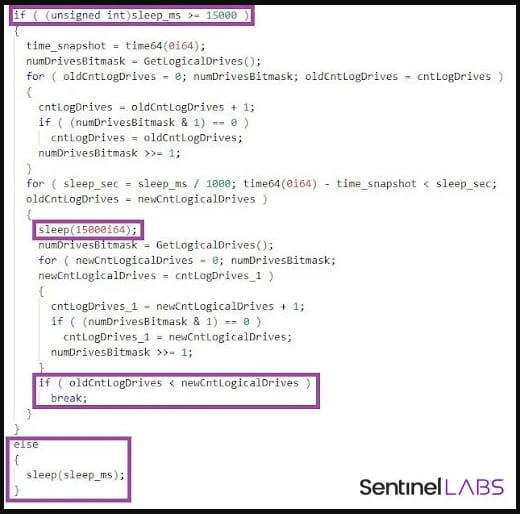
When legitimate users on the compromised devices become active, OpenCarrot automatically enters a sleep state and checks every 15 seconds for the insertion of new USB drives that can be laced and used for lateral movement.
Source: SentinelLabs
Simultaneously, SentinelLabs saw evidence of suspicious traffic originating from the victim’s Linux email server, which was beaconing outbound to ScarCruft infrastructure.
The analysts are still determining the intrusion method but mention the possibility of the threat actors using their signature RokRAT backdoor.
SentinelLabs suggests that the involvement of two state-supported hacking groups could indicate a deliberate strategy by the North Korean state that controls both.
By assigning multiple actors to infiltrate NPO Mashinostroyeniya, which they probably considered a significant target for espionage, the state may have sought to amplify the probability of a successful breach.
