North Korean cybercriminals shattered previous records in 2025, stealing at least $2.02 billion in cryptocurrency through a sophisticated campaign that represents the most successful year ever for state-sponsored digital theft despite fewer confirmed attacks.
This unprecedented haul marks a 51% increase year-over-year. It brings the regime’s cumulative cryptocurrency theft to a staggering $6.75 billion, cementing the Democratic People’s Republic of Korea (DPRK) as the dominant threat actor in the crypto crime landscape.
The record-breaking thefts accounted for 76% of all service compromises in 2025, according to blockchain analysis firm Chainalysis, which tracked the illicit flows through December.
The $2.02 billion stolen in 2025 alone exceeds the previous year’s total by $681 million, demonstrating North Korea’s evolution toward fewer but far more damaging attacks.
This shift reflects a strategic pivot from quantity to quality, with DPRK-affiliated groups focusing on high-value targets that yield maximum returns.
North Korea’s $2 Billion Crypto Theft
North Korean threat actors have refined their tactics through two primary vectors: embedding IT workers within cryptocurrency services and sophisticated impersonation schemes.
Funds stolen in the largest attacks are now 1,000 times larger than those stolen in the typical incident, surpassing even the 2021 bull market peak.
The regime’s notorious IT worker fraud operations have expanded beyond simply infiltrating companies as employees.
In a disturbing evolution, DPRK-linked operators now impersonate recruiters for prominent web3 and AI firms, orchestrating elaborate fake hiring processes designed to harvest credentials, source code, and VPN access during “technical screening” sessions.
At the executive level, bogus outreach from purported strategic investors or acquirers uses pitch meetings and pseudo-due diligence to probe for sensitive systems information and potential access paths into high-value infrastructure.
The money laundering operations supporting these thefts reveal distinct patterns that differentiate state-sponsored actors from conventional cybercriminals.
Analysis of on-chain activity shows DPRK hackers follow a structured 45-day laundering cycle beginning with immediate fund movement through DeFi protocols and mixing services.
The first five days see a 370% spike in DeFi activity as stolen assets are distanced from their source, followed by a second wave focused on integration through exchanges with limited KYC requirements.
The final phase emphasizes conversion to fiat through no-KYC exchanges, guarantee services, and Chinese-language platforms.
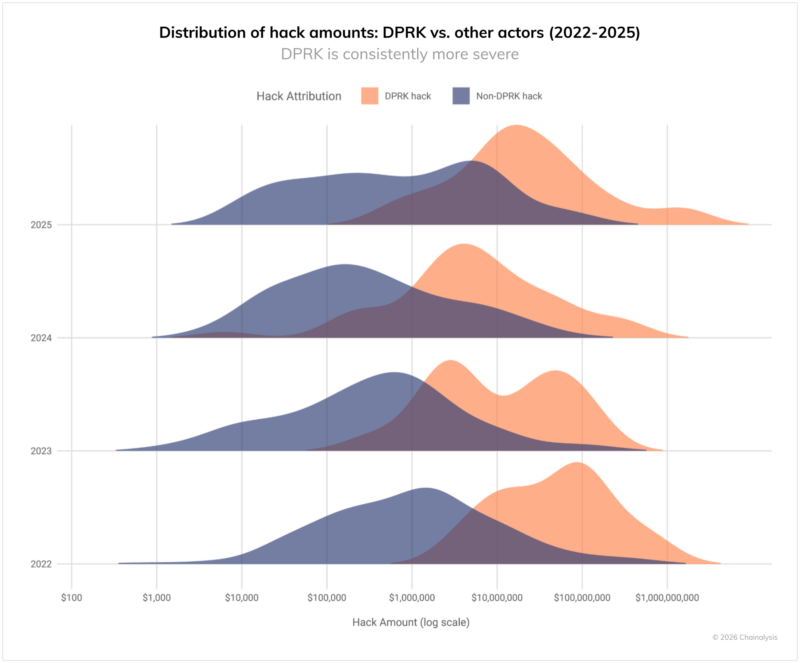
DPRK-linked actors demonstrate clear operational preferences that set them apart from other threat actors. They rely heavily on Chinese-language money movement and guarantee services, showing 355% to over 1000% greater usage compared to other criminals.
Bridge services see 97% higher utilization, while mixing services experience 100% more activity. Specialized services like Huione are favored at 356% above typical usage.
Future of Cryptocurrency
Conversely, DPRK hackers avoid lending protocols, P2P exchanges, and decentralized exchanges that other criminals commonly use, reflecting their integration with professional Asia-Pacific illicit networks rather than the broader DeFi ecosystem.
As the infamous bank robber Willie Sutton supposedly said: “Because that’s where the money is.”
The Bybit hack in February 2025 exemplifies the new paradigm, accounting for $1.5 billion of the year’s total losses in a single incident.
North Korean actors demonstrates how the DPRK’s quality-over-quantity approach can distort overall theft statistics.
When North Korean actors successfully execute a significant theft, they appear to reduce operational tempo to focus on laundering proceeds rather than launching additional attacks.
The broader cryptocurrency crime landscape reveals a concerning concentration of losses. The top three hacks in 2025 accounted for 69% of all stolen funds, with the largest attacks now 1,000 times bigger than the median incident a threshold crossed for the first time.
This extremity creates a threat environment where individual breaches have outsized impacts on yearly totals.
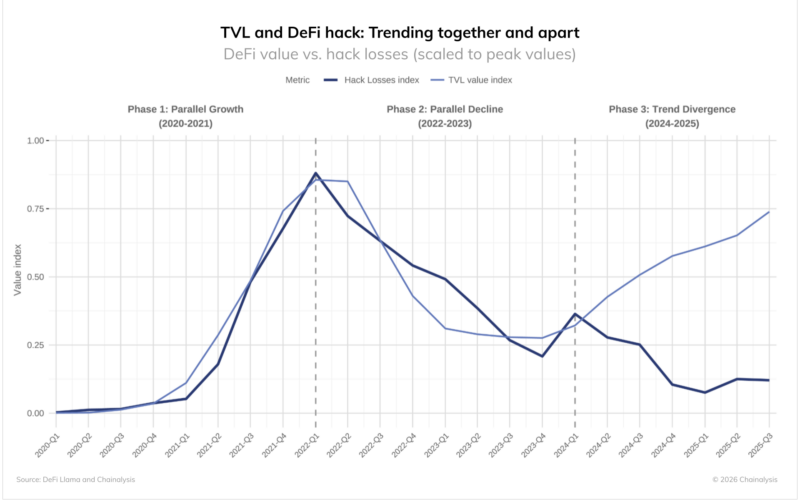
While DeFi protocols showed resilience with suppressed hack losses despite rising Total Value Locked, personal wallet compromises surged to 158,000 incidents affecting 80,000 unique victims.
However, the total value stolen from individuals decreased to $713 million from 2024’s $1.5 billion peak, suggesting attackers are casting wider nets for smaller per-victim hauls.
The cryptocurrency industry faces a critical challenge in 2026: detecting and preventing high-impact DPRK operations before another Bybit-scale incident occurs.
The regime’s consistent laundering patterns and service preferences provide detection opportunities, but its demonstrated ability to execute fewer yet far more damaging attacks signals increasing sophistication and patience.
As North Korea continues using cryptocurrency theft to fund state priorities and circumvent international sanctions, the industry’s ability to identify and disrupt these operations will determine whether 2025’s record stands or falls to even greater thefts in the coming year.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
