North Korean hackers have stolen an estimated $2 billion worth of cryptocurrency assets in 2025, marking the largest annual total on record.
The figure brings the total confirmed amount stolen by these threat actors to more than $6 billion. According to the United Nations and government agencies, these funds are used to further the development of nuclear weapons.
Blockchain experts at Elliptic say that the amount is almost triple compared to 2024, and far exceeding the previous record of $1.35 billion from 2022, which was in large part due to the Ronin Network and Harmony Bridge attacks.
“The 2025 total already dwarfs previous years and is almost triple last year’s tally, underscoring the growing scale of North Korea’s dependence on cyber-enabled theft to fund its regime,” comments Elliptic.
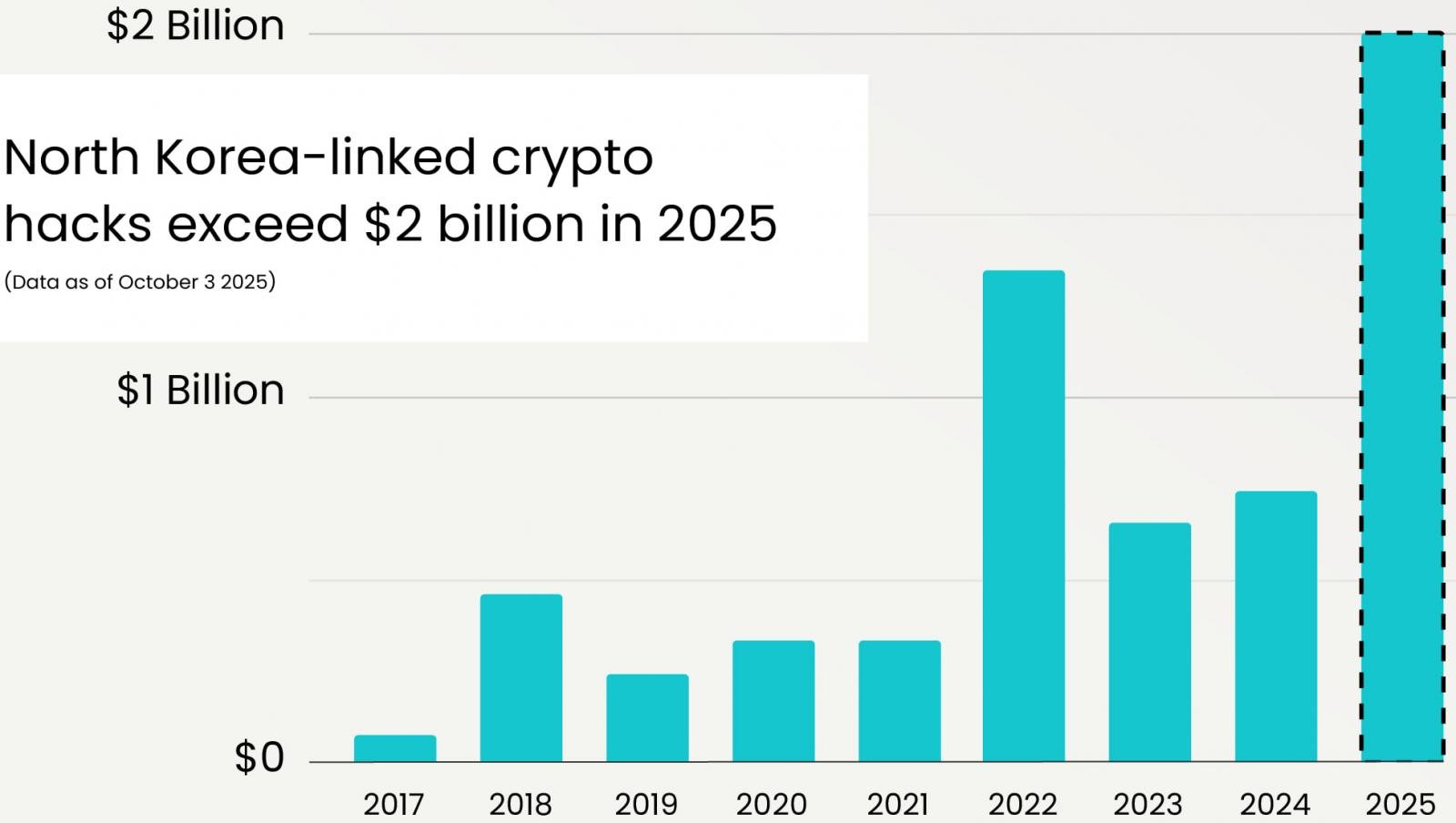
Source: Elliptic
The largest part of the record stolen amount attrributed to North Korean actors in 2025 is from the Bybit hack in February, when the threahackers stole $1.46 billion.
Throughout the year, Elliptic was able to attribute 30 crypto-heists to North Koreans, based on blockchain analysis, laundering patterns, and other intelligence data.
Other notable confirmed breaches this year include those on LND.fi, WOO X, Seedify, and the Taiwanese exchange BitoPro, from where Lazarus stole an estimated $11 million in cryptocurrency.
Elliptic underlines that the real numbers are a conservative estimation as many incidents go unreported, other attributions are low-confidence, and certain events are not counted in the reported total.
For example, Chainalysis attributed over $1.3 billion to North Korean attacks for 2024, confirming the discrepancies between reports from different companies.
One trend Elliptic identified for this year is a shift from targeting businesses to hacking individuals holding large amounts or exchange employees.
These individuals are targeted through social engineering attacks, a method that appears to have replaced exploiting technical flaws in DeFi infrastructure.
The North Koreans’ laundering strategies have also evolved this year, following pressure from overseeing bodies, blockchain analysis firms, and law enforcement agencies.
The threat actors now use more complex evasion tactics that include multiple mixing and cross-chain transfers, the use of obscure blockchains, making utility token purchases, exploiting refund addresses, or using custom tokens issued by laundering networks.
Despite these tactics, Elliptic maintains that blockchain transparency still enables investigators to trace illicit funds, making evasion harder in high-profile cases of financial theft.

Join the Breach and Attack Simulation Summit and experience the future of security validation. Hear from top experts and see how AI-powered BAS is transforming breach and attack simulation.
Don’t miss the event that will shape the future of your security strategy
