ESET researchers have uncovered a sophisticated cyberespionage campaign targeting European defense companies specializing in unmanned aerial vehicle (UAV) technology.
The attacks, attributed to the North Korea-aligned Lazarus group operating under Operation DreamJob, reveal a coordinated effort to steal proprietary manufacturing data and design specifications from critical players in the drone industry.
The campaign, observed beginning in late March 2025, successfully targeted at least three European defense contractors across Southeastern and Central Europe.
Among the compromised entities were a metal engineering firm, an aircraft component manufacturer, and a dedicated defense company—all with significant involvement in UAV development and production.
This operation marks a significant evolution in North Korean cyber capabilities, demonstrating an increasingly targeted approach toward specific technological sectors critical to their military modernization efforts.
Operation DreamJob has become synonymous with Lazarus’s preferred attack methodology: social engineering lures disguised as prestigious employment opportunities.
The campaign, first identified by ClearSky security researchers in 2020, leverages the universal appeal of high-profile job offers to compromise target organizations.
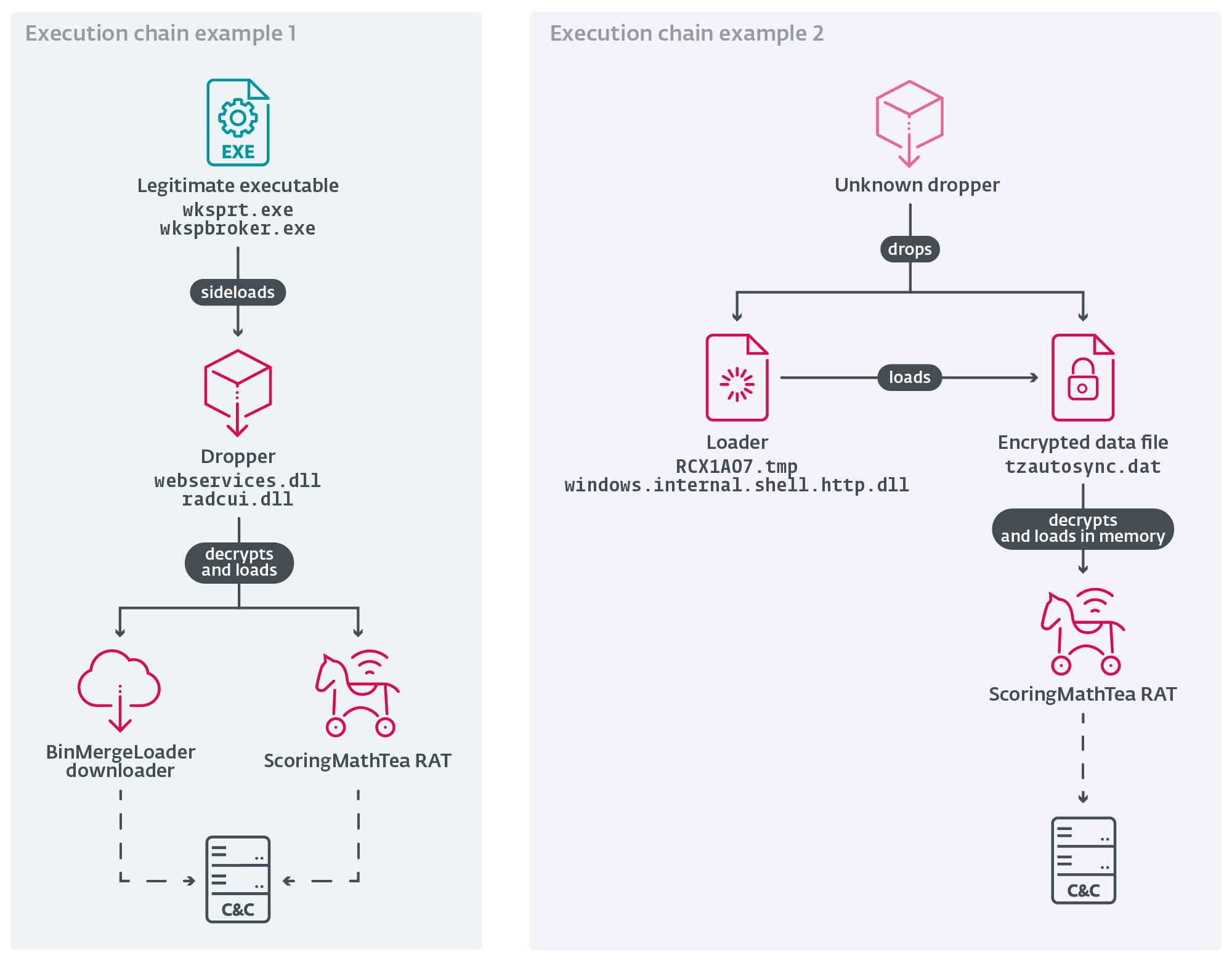
In this latest iteration, victims received expertly crafted decoy documents containing job descriptions accompanied by trojanized PDF readers—a dual approach designed to establish initial access while maintaining a veneer of legitimacy.
The attackers demonstrated notable technical sophistication by incorporating malicious loading routines into open-source projects sourced from GitHub.
BinMergeLoader leverages the Microsoft Graph API and uses Microsoft API tokens for authentication.
Throughout 2025, the campaign utilized trojanized versions of TightVNC Viewer, MuPDF reader, and popular developer tools including WinMerge plugins and Notepad++ extensions.
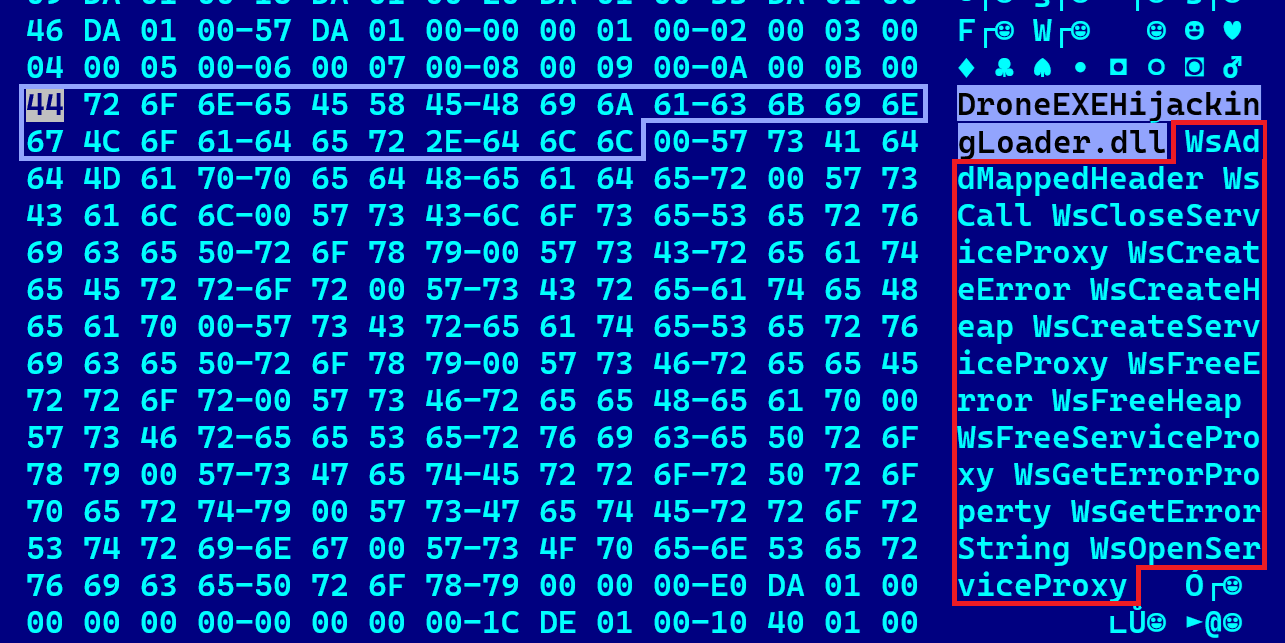
One particularly revealing indicator emerged in the form of a dropper containing the internal DLL name “DroneEXEHijackingLoader.dll”—a direct reference suggesting the campaign’s explicit focus on UAV-related intellectual property theft.
North Korean Drone Expansion
The timing and targeting of this operation aligns precisely with North Korea’s documented expansion of its domestic drone manufacturing capabilities.
We believe that the substring drone is there to designate both a UAV device and the attacker’s internal campaign name.

Recent intelligence indicates that Pyongyang is investing heavily in developing advanced UAV systems, including reconnaissance platforms like the Saetbyol-4 and combat drones such as the Saetbyol-9.
These aircraft bear striking resemblances to American counterparts—the RQ-4 Global Hawk and MQ-9 Reaper respectively—suggesting extensive reliance on reverse engineering and intellectual property acquisition.
Geopolitical factors further contextualize these attacks. At the time of Operation DreamJob’s observed activity in 2025, North Korean troops were deployed alongside Russian forces in Ukraine, providing frontline exposure to Western military equipment including the very UAV systems manufactured by the targeted companies.
This battlefield experience likely motivated efforts to obtain detailed technical specifications and manufacturing processes for systems currently deployed in active conflict zones.
ScoringMathTea: Lazarus’s Persistent Payload
The primary malware deployed across all observed attacks was ScoringMathTea, a remote access trojan that has served as Lazarus flagship payload for Operation DreamJob campaigns since late 2022.
This sophisticated RAT supports approximately 40 distinct commands, enabling attackers to manipulate files, execute arbitrary code, harvest system information, and maintain persistent command-and-control communication through compromised servers disguised as WordPress hosting platforms.
The operation underscores a critical vulnerability within sensitive technology sectors: employee awareness regarding social engineering threats remains insufficient despite extensive media coverage of Operation DreamJob tactics.
The consistent success of these campaigns suggests that targeted organizations continue to struggle with implementing robust hiring verification processes and employee security awareness programs.
For companies developing UAV technology, this campaign represents a direct threat to competitive advantage and military capability.
As North Korea accelerates its drone program expansion and reportedly begins constructing dedicated UAV manufacturing facilities, the pressure on Western defense contractors to strengthen their cybersecurity posture has never been more acute.
Organizations in aerospace, engineering, and defense sectors must prioritize verification of recruitment communications and implement advanced endpoint detection systems capable of identifying trojanized applications and malicious DLL side-loading techniques characteristic of Operation DreamJob campaigns.
IoCs
| SHA-1 | Filename | Detection | Description |
|---|---|---|---|
| 28978E987BC59E75CA22562924EAB93355CF679E | TSMSISrv.dll | Win64/NukeSped.TL | QuanPinLoader. |
| 5E5BBA521F0034D342CC26DB8BCFECE57DBD4616 | libmupdf.dll | Win64/NukeSped.TE | A loader disguised as a MuPDF rendering library v3.3.3. |
| B12EEB595FEEC2CFBF9A60E1CC21A14CE8873539 | radcui.dll | Win64/NukeSped.TO | A dropper disguised as a RemoteApp and Desktop Connection UI Component library. |
| 26AA2643B07C48CB6943150ADE541580279E8E0E | HideFirstLetter.DLL | Win64/NukeSped.TO | BinMergeLoader. |
| 0CB73D70FD4132A4FF5493DAA84AAE839F6329D5 | libpcre.dll | Win64/NukeSped.TP | A loader that is a trojanized libpcre library. |
| 03D9B8F0FCF9173D2964CE7173D21E681DFA8DA4 | webservices.dll | Win64/NukeSped.RN | A dropper disguised as a Microsoft Web Services Runtime library. |
| 71D0DDB7C6CAC4BA2BDE679941FA92A31FBEC1FF | N/A | Win64/NukeSped.RN | ScoringMathTea. |
| 87B2DF764455164C6982BA9700F27EA34D3565DF | webservices.dll | Win64/NukeSped.RW | A dropper disguised as a Microsoft Web Services Runtime library. |
| E670C4275EC24D403E0D4DE7135CBCF1D54FF09C | N/A | Win64/NukeSped.RW | ScoringMathTea. |
| B6D8D8F5E0864F5DA788F96BE085ABECF3581CCE | radcui.dll | Win64/NukeSped.TF | A loader disguised as a RemoteApp and Desktop Connection UI Component library. |
| 5B85DD485FD516AA1F4412801897A40A9BE31837 | RCX1A07.tmp | Win64/NukeSped.TH | A loader of an encrypted ScoringMathTea. |
| B68C49841DC48E3672031795D85ED24F9F619782 | TSMSISrv.dll | Win64/NukeSped.TL | QuanPinLoader. |
| AC16B1BAEDE349E4824335E0993533BF5FC116B3 | cache.dat | Win64/NukeSped.QK | A decrypted ScoringMathTea RAT. |
| 2AA341B03FAC3054C57640122EA849BC0C2B6AF6 | msadomr.dll | Win64/NukeSped.SP | A loader disguised as a Microsoft DirectInput library. |
| CB7834BE7DE07F89352080654F7FEB574B42A2B8 | ComparePlus.dll | Win64/NukeSped.SJ | A trojanized Notepad++ plugin disguised as a Microsoft Web Services Runtime library. A dropper from VirusTotal. |
| 262B4ED6AC6A977135DECA5B0872B7D6D676083A | tzautosync.dat | Win64/NukeSped.RW | A decrypted ScoringMathTea, stored encrypted on the disk. |
| 086816466D9D9C12FCADA1C872B8C0FF0A5FC611 | N/A | Win64/NukeSped.RN | ScoringMathTea. |
| 2A2B20FDDD65BA28E7C57AC97A158C9F15A61B05 | cache.dat | Win64/NukeSped.SN | A downloader similar to BinMergeLoader built as a trojanized NPPHexEditor plugin. |
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
