Cisco Talos has uncovered a new remote access trojan (RAT) family, which is XenoRAT-based malware that is under active development by a North Korean nexus cluster named “UAT-5394.”
While the new malware is dubbed “MoonPeak,” and the analysis reveals links to the UAT-5394 infrastructure and new tactics, techniques, and procedures (TTPs) of the threat actor.

This cluster of activity has some overlaps in TTPs and infrastructure patterns with the North Korean state-sponsored group “Kimsuky,” but Talos lacks substantial technical evidence to link this campaign with the APT.
Talos’ research has uncovered the testing and staging infrastructure used to create new iterations of MoonPeak, including the C2 server that hosts malicious artifacts for download and access to existing servers to update payloads and retrieve logs.
New MoonPeak Malware
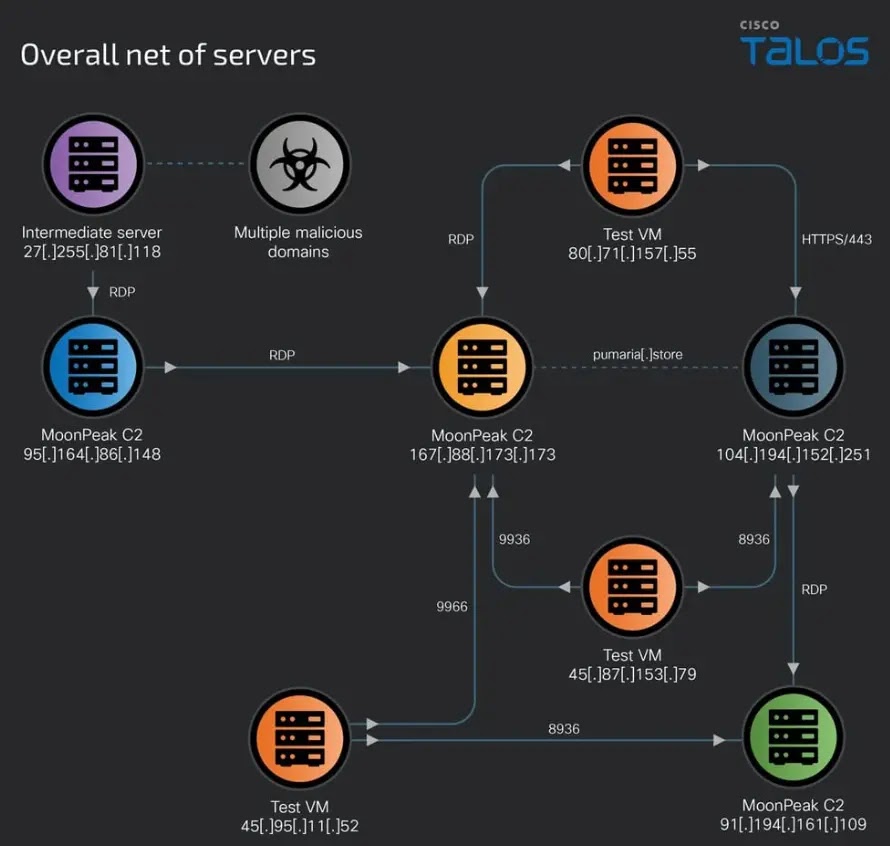
In Talos’ detailed analysis of the complex MoonPeak malware infrastructure, UAT-5394 found out that there were multiple networks consisting of malicious servers, test VMs, and command-and-control hosts.
Free Webinar on Detecting & Blocking Supply Chain Attack -> Book your Spot
These consist of remote access and C2 servers, as well as payload-hosting sites and even test VMs used by the attackers to verify their implants for MoonPeak in advance of delivering them to potential victims.
Regarding this, one key finding was that between at least 5th July 2024, this IP address, 95.164.86.148, functioned as an early Moonpeak C2 on port 9999 before subsequently being observed connecting to QuasarRAT C2 at 84.247.179.77 for possible concurrent access and persistence.
Finally, another server under the control of UAT-5394 over this period – between June 30th and July 8th – is noted to have hosted the pumaria.store domain name and was used to test samples associated with MoonPeak v2 with connections from its threat actors’ test VMs at 45.87.153.79 and 45.95.11.52 as witnessed by Cisco’s Talos Security Intelligence & Research Group research team (Talos) in January last year.
The threat actors subsequently set up 104.194.152.251 as a new MoonPeak C2, which was accessed by their test machines to validate the latest MoonPeak variants, including one compiled as recently as July 16, 2024.
.webp)
Analysis of the MoonPeak samples revealed an evolution in the malware’s obfuscation and communication characteristics, with each new increment designed to work only with specific C2 server configurations, showcasing the threat actors’ efforts to maintain control and evade detection.
With UAT-5394 deploying new infrastructure, MoonPeak’s constant evolution runs in parallel. This highlights the group’s adaptability abilities.
The XenoRAT malware has gone through changes by malefactors, including modifications to the client namespace, communication protocol, and obscuring techniques.
These changes are intended to facilitate tactical evasion and deter undesirable clients from making communications with the C2 infrastructure.
UAT-5394 threat actor has been actively updating the RAT code as seen in new features like state machines and string obfuscation that have been included.
The speed at which these changes happen indicates how fast this group is trying to spread its campaign widely while also establishing more drop points and C2 servers.
Are you from SOC and DFIR Teams? Analyse Malware Incidents & get live Access with ANY.RUN -> Get 14 Days Free Acces
