A sophisticated new variant of the North Korean-linked Contagious Interview campaign has emerged, featuring an unprecedented level of polish and technical sophistication designed to compromise job-seeking AI developers, software engineers, and cryptocurrency professionals.
Unlike typical DPRK IT worker infiltration schemes, this operation targets real individuals through an elaborate fake recruitment platform that mimics legitimate hiring processes with alarming accuracy.
Security researchers discovered the malicious platform hosted at lenvny[.]com through continuous YARA-based scanning operations.
What initially appeared as another disposable phishing page turned out to be a fully formed React/Next.js-based job platform, complete with dozens of routes, dynamically generated UUID-driven job listings, and an application workflow mirroring contemporary hiring systems.
The site claims to be an “Integrated AI-Powered Interview Tool” for recruitment, featuring professional badges, fabricated testimonials, and logos from well-known tech companies to establish credibility.
The platform’s landing page employs gradient-heavy UI design and synthetic branding intentionally tuned to resemble legitimate AI tooling ecosystems in 2025.
The actors further extend this credibility veneer with a feature comparison chart, positioning their fictitious platform alongside real companies building AI workflow or hiring-productivity tools.
Researchers note the overall theme mimics the legitimate Lever talent acquisition platform, complete with feature comparison charts positioning the fraudulent service alongside genuine AI workflow and hiring-productivity tools.
Weaponized Application Process
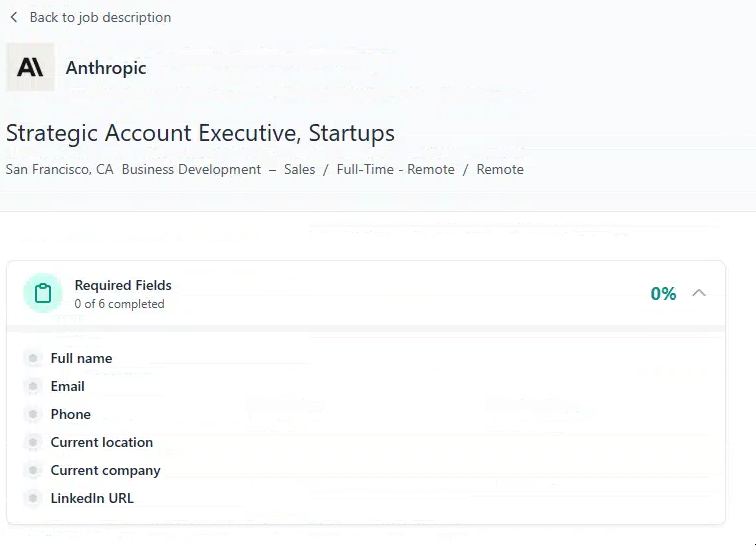
The fake career portal showcases job openings from repeatedly impersonated organizations including Anthropic, Yuga Labs, Anchorage Digital, Gate, and Digital Currency Group.
The application flow begins with a standardized form replicated across all listed positions.
Each listing contains fabricated positions spanning business development, product management, research, and finance with realistic job descriptions formatted to resemble legitimate US postings.
The application flow collects comprehensive personal information including full name, email, phone number, current employer, location, LinkedIn URL, GitHub profile, and portfolio links.
An “AI-powered auto-fill” feature encourages victims to upload actual resumes in PDF or DOCX format, enabling operators to build target-rich dossiers even if malware delivery fails.
The critical malicious stage occurs during the “Video Introduction” requirement, where applicants are asked to record a brief video explaining their interest.
When accessed with a valid invitation code, attempting to record triggers a fake error message employing the ClickFix technique. The page hijacks the victim’s clipboard, replacing copied troubleshooting instructions with a weaponized multi-stage PowerShell command.
The malicious payload masquerades as a Microsoft graphics driver update while simultaneously downloading a secondary archive from attacker infrastructure.
A VBScript loader executes in the final stage, establishing persistence and potentially downloading additional payloads.
This clipboard manipulation technique exploits routine copy-paste behavior, making accidental execution significantly more likely.
High-Value Talent
The choice to impersonate employers in AI and cryptocurrency sectors reflects documented DPRK collection priorities.
These professionals offer direct relevance to North Korean strategic programs, immediate financial utility through crypto access, and frequently operate development environments with elevated privileges.
Their workstations may contain proprietary AI research, model weights, key-management systems, or smart contract audits supporting DPRK operational and financial objectives.
Security experts advise job seekers to verify all career pages originate from official first-party domains, avoid uploading sensitive documents to unvalidated platforms, and execute unknown scripts only in isolated virtual machines or sandboxes.
The sophistication of this campaign represents a notable maturation in DPRK social engineering tradecraft, making vigilance essential for technical professionals navigating the job market.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
