North Korean threat actors planted 67 malicious packages in the Node Package Manager (npm) online repository to deliver a new malware loader called XORIndex to developer systems.
The packages collectively count more than 17,000 downloads and were discovered by researchers at package security platform Socket, who assess them to be part of the continued Contagious Interview operation.
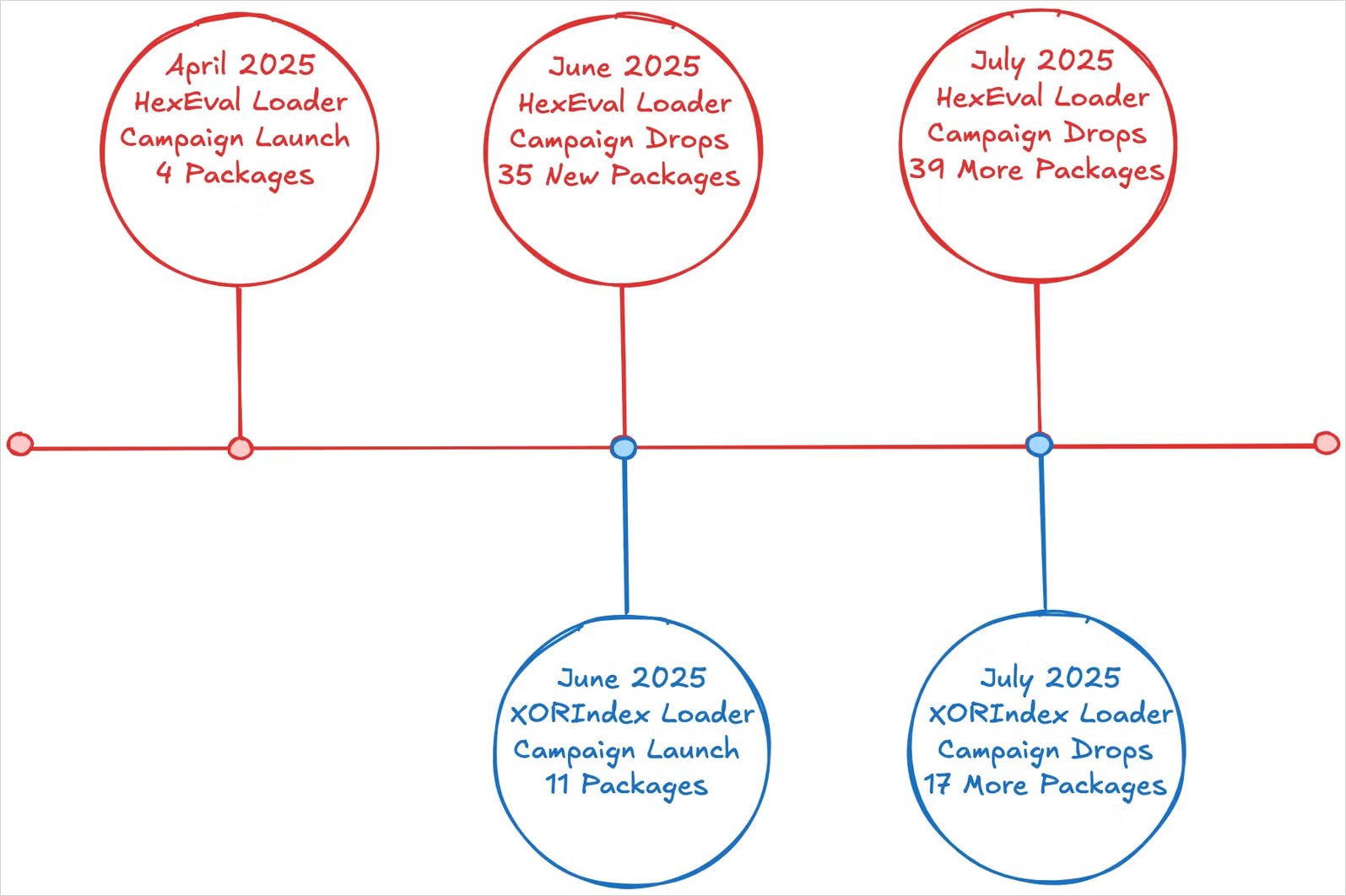
Socket researchers say that the campaign follows threat activity detected since April. Last month, the same actor infiltrated npm with 35 packages that dropped information stealers and backdoors onto developers’ devices.
Source: Socket
Overview of the attacks
Contagious Interview is a North Korean state-backed campaign that targets mostly developers with fake job offers to trick them into running malicious code on their systems.
The purpose varies from collecting sensitive information that allows breaching companies to stealing cryptocurrency assets.
The Node Package Manager (npm) is the default package manager for Node.js, a platform where developers publish and install JavaScript libraries and tools. It is widely used in web development, but also frequently exploited by threat actors for malware distribution.
Out of the 67 packages the threat actors uploaded onto npm this time, there are several that appear to mimic or blend the names of legitimate software projects and libraries, like:
- vite-meta-plugin
- vite-postcss-tools
- vite-logging-tool
- vite-proc-log
- pretty-chalk
- postcss-preloader
- js-prettier
- flowframe
- figwrap
- midd-js, middy-js
When victims install any of these packages, a ‘postinstall’ script executes to launch XORIndex Loader, a novel tool that appears to be used in parallel with HexEval Loader, a malware dropper observed in past attacks.
XORIndex Loader collects host data to profile each victim and sends it to a hardcoded command and control (C2) address, hosted on infrastructure from Vercel cloud application company.
The C2 server responds with one or more JavaScript payloads, which are executed on the victim’s system using eval(). These payloads are typically the BeaverTail and the InvisibleFerret backdoor, both attributed to North Korean Contagious Interview operations.
The two pieces of malware provide access to compromised machines, allow data exfiltration, and can download more payloads.
According to the researchers, the North Korean hackers blend old and new tools with subtle modifications to evade detection, and every time npm cleans an infection, they return via different npm accounts and package names.
“Contagious Interview threat actors will continue to diversify their malware portfolio, rotating through new npm maintainer aliases, reusing loaders such as HexEval Loader and malware families like BeaverTail and InvisibleFerret, and actively deploying newly observed variants including XORIndex Loader” – Socket
“Defenders should expect continued iterations of these loaders across newly published packages, often with slight variations to evade detection,” the researchers warn.
Socket researchers say that they reported to npm all malicious packages from the latest campaign but some of them may still be available in the repository.
It is important to double-check sourced packages to ensure they’re not typosquatting decoys, only trust well-known projects and publishers with a proven record, and scrutinize recent repository activity for signs of automation.
When possible, always examine the source code for obfuscation and execute new libraries in isolated environments to evaluate their safety.

While cloud attacks may be growing more sophisticated, attackers still succeed with surprisingly simple techniques.
Drawing from Wiz’s detections across thousands of organizations, this report reveals 8 key techniques used by cloud-fluent threat actors.




