Weeks after the first update on the Norton Healthcare cyber attack came, the ALPHV/BlackCat ransomware group disclosed that it was a ransomware attack.
Norton Healthcare earlier announced a “cyber-incident” after it got a suspicious message on May 9. Threat intelligence researcher Brett Callow posted the following blurred screenshot of the leaked data from the Norton Healthcare cyber attack.
Norton Healthcare cyber attack
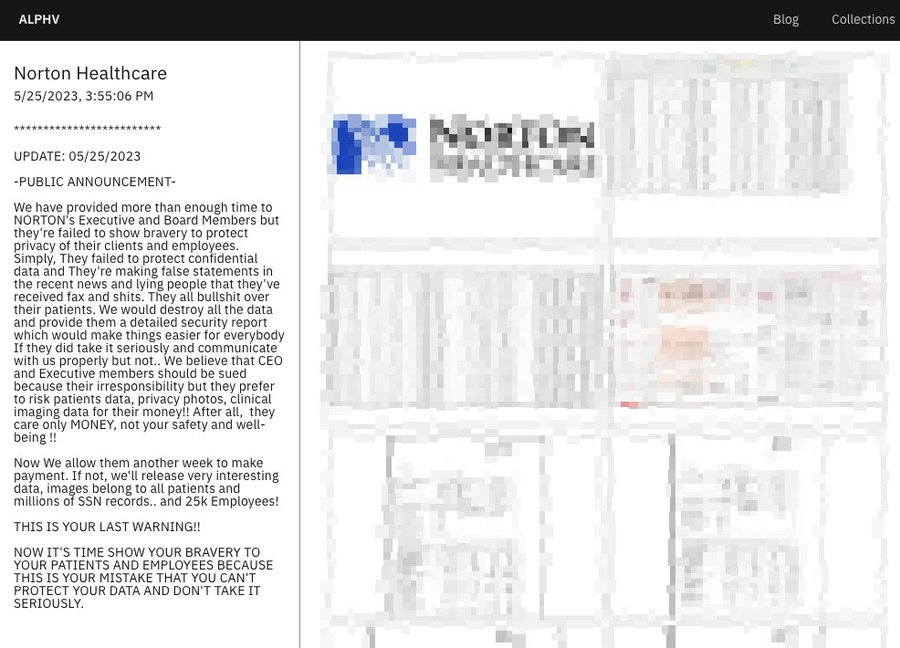
ALPHV wrote on its leak site that the time given to Norton executives and board members was exhausted wherein they did not try to protect the privacy of their clients and employees. “They’re making false statements in the recent news and lying people that they’ve received fax….”
The ransomware group said that they would destroy all the exfiltrated data and give them a detailed security report, from the Norton Healthcare cyber attack.

The ransomware group made a rant about the officials of Norton Healthcare getting sued for their irresponsibility in risking patient data, that they stole in the Norton ransomware attack.
The group exfiltrated photos, millions of SSN records, 25,0000 employee data, clinical imaging data, etc. The ALPHV post extended the ransom payment deadline another week following which if their demands were not met, they will leak the data.
This was the group’s last warning for Norton Healthcare.
History of the Norton Healthcare cyber attack
The Norton Healthcare cyber attack came to light on May 10, when the company announced on Facebook about an IT disruption that affected its services.

Disrupted services from the Norton Healthcare cyber attack were Norton eCare and Norton My Chart, the healthcare service’s electronic medical records software.
Two days later, Norton Healthcare disclosed on Facebook that it was indeed a cyber attack.

“Although- our review is ongoing, an initial analysis confirms Norton Health care was the victim of a cyber-event.” They confirmed that medical practices and other facilities were open while caregivers maintained the required protocols in the absence of accessible systems.
Further updates on the Norton Healthcare cyber attack came with a May 16 notification on Facebook, which disclosed that the cyber attack happened on May 9, following which their IT systems had to be taken offline.
“Why is no one talking about all of the non-elective, time-sensitive surgeries that are being canceled or not scheduled? No images being read, no imaging available for before, after or during surgeries,” a Facebook user responded.
Other details about the Norton Healthcare cyberattack
Several patients spoke up about delayed healthcare services for reports and results due to the Norton Healthcare cyber attack.
The last alert made by the healthcare today assured that they were closer to resuming all operations and bringing the systems back online.
According to the healthcare’s news release updated on May 24, the following services were impacted by the Norton Healthcare cyber attack:
- Same-day appointment for illnesses or minor injury
- Emergency care
- Some procedures including exams and appointments were required to be rescheduled.
- Sharing test results and images
- Prescription refill
- Online payments for Norton MyChart
“We want to let the community know that we know that our processes are a little bit different now. They’re a bit different so that care can continue,” a WDRB report on May 24 cited Renee Murphy, Norton Healthcare’s chief marketing and communications officer.
“What happened to us in the cyber event, again, was something that happened to us and we’ve responded accordingly in a way that care can continue,” he said.
It is not clear how much data was exfiltrated and the sum ALPHV ransomware group has demanded for data stolen from the Norton Healthcare cyber attack. The Cyber Express reached out to the healthcare and we will update this report as we receive a response from them.
Norton Healthcare serves nearly 600,000 patients across Louisville, a year. It has $4.7 billion worth of assets with five hospitals, eight outpatient centers, 18 urgent care clinics, and 289 doctor’s offices.
BlackCat ransomware and US healthcare
ALPHV/BlackCat ransomware group is among the top three ransomware gangs by the number of victims till date. Healthcare sector continues to be one of its preferred targets.
The Health Sector Cybersecurity Coordination Center of the US Department of Health and Human Services in January alerted about the BlackCat ransomware group’s operations in the healthcare sector, particularly its triple extortion tactic.
This means that in addition to encrypting data and demanding a ransom, the group also threatens to leak the data and launch distributed denial-of-service attacks if the ransom is not paid.
BlackCat is believed to have emerged from Darkside and BlackMatter, and is connected to former members of the REvil group.
BlackCat has demanded ransom payments as high as $1.5 million, with affiliates retaining 80% to 90% of the extortion payments. The group frequently updates its tooling and arsenal as they undergo testing and usage cycles, making it a dynamic and evolving threat.
Security researchers have identified instances where BlackCat attackers have utilized a PowerShell command to download Cobalt Strike beacons on affected systems, as well as a penetration testing tool called Brute Ratel, which exhibits remote access features similar to Cobalt Strike.
The encryption methods employed by BlackCat include ChaCha20 and AES, along with six encryption modes: Full, HeadOnly, DotPattern, SmartPattern, AdvancedSmartPattern, and Auto.
BlackCat’s latest ransomware variant, developed in the memory-safe and cross-platform programming language Rust, provides the group with enhanced flexibility and capabilities.
