Yet again, the NoName ransomware group has targeted Norway, this time claiming an attack on nine critical infrastructures within the country. This recent occurrence adds to the series of cyber attacks on Norway.
The organizations listed in the Norway cyber attack by the hacker collective include BPS Nord, Ferde AS, Ruter AS, Boreal Norge AS, Agder Public Transport, Stortinget (Norwegian Parliament), Skipsverft, BaneNor Log, and Oslo Municipality.
The assault on Norway’s infrastructure originated through a Distributed Denial of Service (DDoS) assault, as announced by the threat actors themselves. The NoName ransomware group has left its digital mark by defacing various websites, as indicated by their online posts and compromised links.
Norway cyber attack: 9 victims so far!
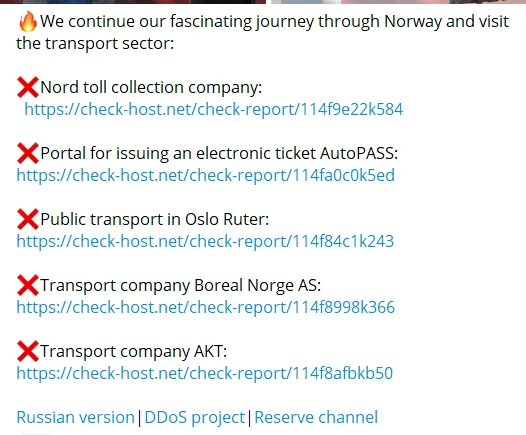
In their online posts, the ransomware gang provided a glimpse into their targets and methods, showcasing their reach and impact. “We continue our fascinating journey through Norway and visit the transport sector,” read the threat actor post.

Moreover, the NoName ransomware group also listed the victims’ names and shared some check-host links to verify their claims of launching a cyber attack on Norway.
Additionally, the hackers proclaimed their success in crippling multiple other websites, “We killed the sites of Norway,” concludes the threat actor post.
To delve deeper into the Norway cyber attack, The Cyber Express reached out to some of the alleged victims on the list.
However, at the time of writing, no official statements or responses had been issued by the organizations, leaving a cloud of uncertainty regarding the extent of the breach and its consequences.
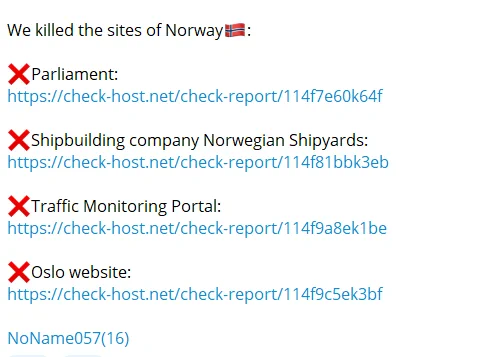
The range of victims in this Norway cyber attack spans various sectors, signaling the hackers’ indiscriminate approach.
The impacted entities include both government-controlled organizations and private companies, highlighting the breadth of the attackers’ ambitions.
Prominent entities have been named as victim in the alleged Norway cyber attack. These include Bompengeselskap Nord AS (BPS Nord), a Norwegian toll company owned by Nordland and Troms og Finnmark counties; Ferde AS, a Norwegian toll company owned by Agder, Rogaland, and Vestland counties; Ruter AS, the public transport authority for Oslo and Akershus counties; Boreal Norge AS, a Norwegian public transport operator with operations spanning multiple counties; the supreme legislature of Norway, Stortinget (Norwegian Parliament); and the administrative body of the capital city of Oslo, Oslo Municipality.
Escalating cyber attacks targeting Norway
While this Norway cyber attack is undoubtedly alarming, it’s not the first time the nation has faced such a threat.
Back in July 2023, various Norwegian government ministries were targeted in a cyber attack. This attack was attributed to a third-party vulnerability, leading to a breach that impacted twelve government ministries.
Erik Hope, head of the government agencies responsible for ministry services, stated that the source of the breach was identified and rectified.
“We identified a weakness in the platform of one of our suppliers. That weakness has now been shut,” said Erik Hope in a news conference.
The attack’s specifics, such as the responsible parties and the complete ramifications, were not shared with the general public.
Furthermore, in June 2022, Norway experienced a distributed denial-of-service (DDoS) attack that disrupted operations across numerous organizations.
The NSM Security Authority reported this attack, linking it to a “criminal Pro-Russia” group. Fortunately, sensitive information was not compromised during the cyber attack on Norway.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
