Released by the National Security Agency (NSA) and the Cybersecurity and Infrastructure Security Agency (CISA), the cybersecurity information sheet (CSI) titled “Defending Continuous Integration/Continuous Delivery (CI/CD) Environments” offers suggestions and best practices for enhancing defenses in cloud implementations of development, security, and operations (DevSecOps).
Securing a CI/CD environment critically depends on being aware of the many security threats that might impact operations and taking action to protect against each one.
.png
)
The CI/CD environments and software supply chains are prime targets for cybercriminals, as shown by the rising number of intrusions over time.
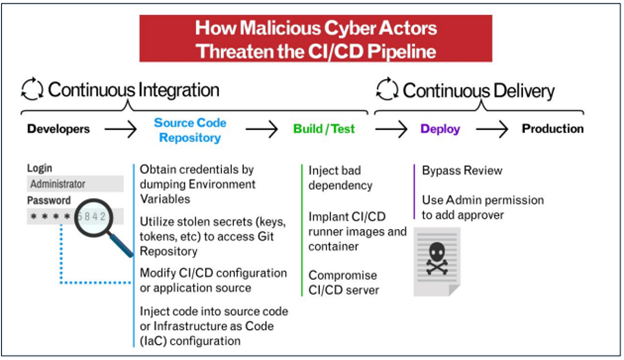
CI/CD Environments – Popular Targets
The Continuous Integration/Continuous Delivery (CI/CD) development approach helps organizations maintain a consistent application code base while dynamically merging code changes. It allows for speedy construction and testing of code changes.
The (DevSecOps) model, which incorporates security and automation throughout the development lifecycle, includes CI/CD as a critical component.
Because of the cloud’s importance to IT modernization initiatives, CI/CD pipelines are frequently deployed in commercial cloud settings.
Recommendations To Secure CI/CD Environments
- Use NSA-Recommended Cryptography
When designing cloud apps and services, the NSA and CISA advise using powerful cryptographic algorithms and configuration.
The protection of information, trade secrets, application programming interfaces (APIs), and keys created across the CI/CD pipeline is enhanced by the proper implementation and setup of these techniques.
- Minimize the use of long-term credentials
When it’s practicable, use strong credentials that resist being stolen, phished, guessed, and replayed. Use identity federation and phishing-resistant security tokens to get temporary SSH and other keys whenever human authentication is required.
- Add signature to CI/CD configuration and verify it
Secure code signing is advised by the NSA and CISA to create digital confidence inside the CI/CD pipeline.
Regardless of the level of development, make that code is consistently and correctly signed, and the signature is checked.
If the signature cannot be validated, look into what could be causing it. It may be a simple setting issue or an indication of a bigger breach.
- Utilize two-person rules (2PR) for all code updates
A single developer shouldn’t check in code without first being reviewed and approved by another developer.
This practice improves code quality in general and makes it considerably less likely that malicious code will be successfully checked in if a single developer’s credentials are compromised.
- Implement least-privilege policies for CI/CD access
Everyone in the company should not have access to the CI/CD pipeline.
Employees should only be granted restricted access with certain credentials upon request rather than being given access to all pipelines automatically.
Only the pipelines and components they are changing should be accessible to developers. Also, implement multi-factor authentication (MFA) to reduce the dangers associated with passwords.
Audit administrative user accounts regularly and sets up access limits using the least privilege and separation of duties concepts. audit records to verify the legitimacy of new accounts.
In a CI/CD pipeline, it is essential to handle secrets, tokens, and other credentials securely.
Never send confidential information across a pipeline in plaintext.
Make sure that confidential information is never left in software that may be reverse-engineered, such as passwords and private keys.
- Implement network segmentation and traffic filtering
To prevent the spread of malware and restrict access from other portions of the network that do not require access, implement and enforce effective network segmentation across networks and services.
It is recommended to establish a demilitarized zone to stop unchecked network connectivity.
Filter network traffic to prevent communications from known malicious IP addresses entering or leaving the network.
Final Thoughts
“The organizations should implement the proposed mitigations to harden their CI/CD environments and bolster organizational DevSecOps”, recommends NSA and CISA.
By implementing the proposed mitigations, organizations can reduce the number of exploitation vectors in their CI/CD environments and create a challenging environment for the adversary to penetrate”.
Hence, to protect and harden the CI/CD attack surface, keep malicious actors out by applying the following recommendations.
This is necessary to maintain a robust cybersecurity posture for the Department of Defence (DoD), the Defence Industrial Base (DIB), the federal, state, local, tribal, and territorial (SLTT) administrations, as well as owners of private sector information systems.
“AI-based email security measures Protect your business From Email Threats!” – Request a Free Demo.
