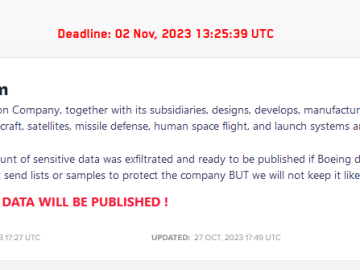
Cybercriminals are allegedly targeting gamers looking for Nvidia drivers with the Aurora crypto wallet stealer. However, the number of individuals impacted by the fraudulent Nvidia drivers scam and the amount of data stolen is yet to be known.
Technology company Namecheap, which provides domain names, hosting, security tools and more, responded to a tweet by a researcher ULTRAFRAUD, who shared details of the alleged target campaign where fake Nvidia drivers websites were being used to spread Aurora crypto wallet stealer. The company requested the researcher to submit a ticket so they could proceed with internal investigations.
Details about the fraudulent Nvidia drivers scam
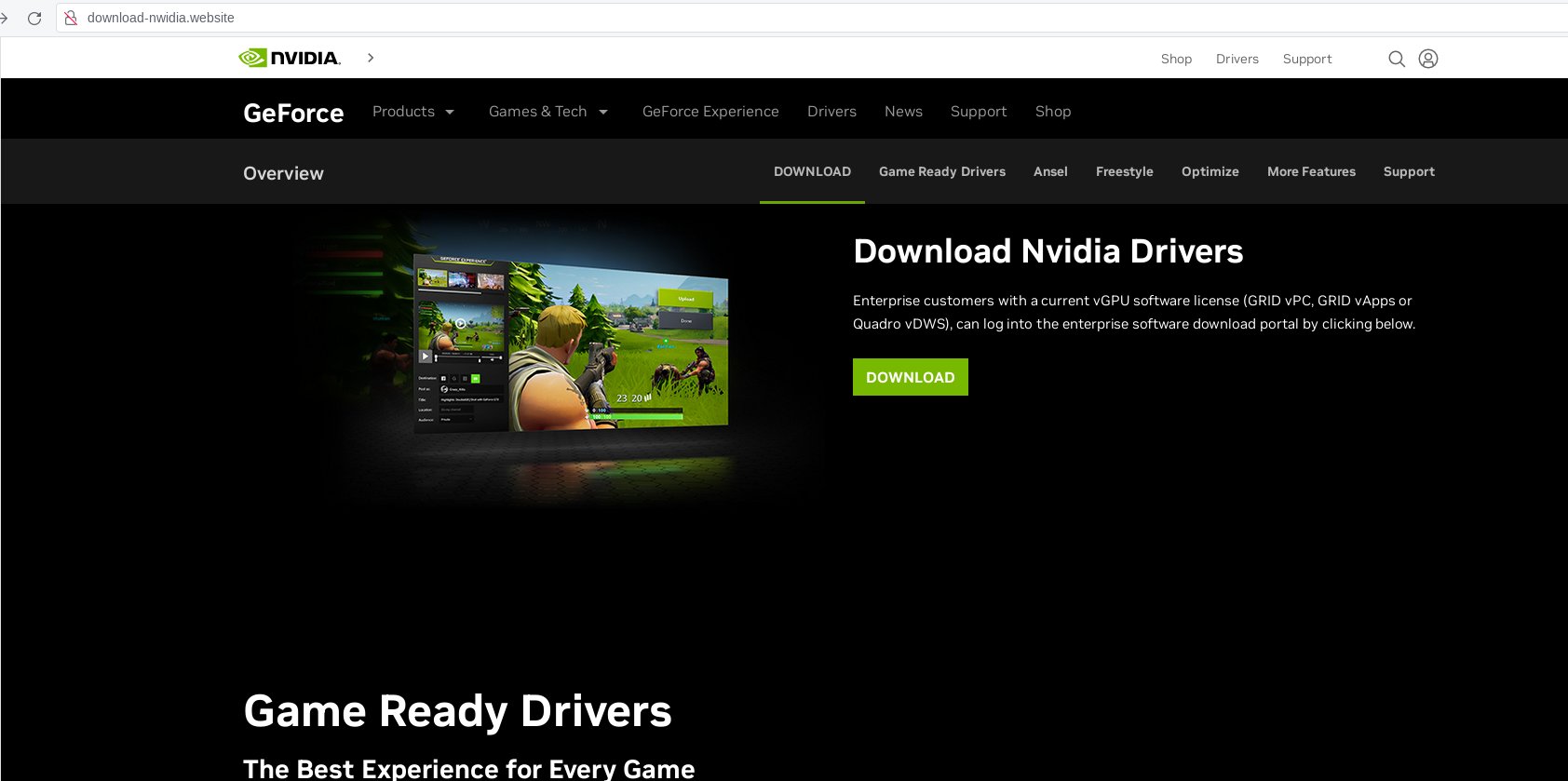
Scammers used a fraudulent website to dupe users into believing that it was the official Nvidia website for downloading Nvidia drivers.
Not much about the cyberattack has been found so far. However, based on a report by Cyble on the Aurora stealer, it can be inferred that the fraudulent Nvidia drivers website steals data from crypto wallet browser extensions.
The following fraudulent websites were found by the researcher:
- /download-nwidia.website
- /babieschristeningoutfits.com
The first link has a spelling change from the official Nvidia with a ‘v’. Scammers create fraudulent or spoofed websites often using nearly the same details to convince unsuspecting users. Hence, users are urged to download Nvidia drivers from its official web stores and sites by checking the URL.
Aurora stealer
Cyble Research & Intelligence Labs (CRIL) noted that phishing websites were being used by threat actors using the Aurora stealer to not only steal data but also to download more malware and Remote Access Trojans (RATs) into the system.
Some users, in previous incidents, were sent fraudulent websites in the form of links in phishing emails. A few of the extension IDs targeted by the Aurora stealer are mentioned below:
- MetaMask
- Yoroi
- TronLink
- Nifty Wallet
- Coinbase Wallet
- Brave Wallet
- Guarda Wallet
- BitApp Wallet
The Aurora Stealer is known to be a ‘shapeshifting’ tactic because of the versatility in its usage and impersonation of various applications and websites to infect maximum users. The Aurora malware also targets users on Telegram, Discord, and Steam applications. It saves the stolen data in JSON format.
It then compresses the data using GZIP, converts the zip file to Base64 format of encoding, and finally sends it to the command-and-control server of the cybercriminal.