This blog was written by Oath CISO and Paranoid in Chief Chris Nims and originally published on Oath.com.
A little more than three months ago, we brought 40 of the world’s best white hat hackers to an undisclosed location in San Francisco to hack our portfolio of brands and online services, including Tumblr, Yahoo, Verizon Digital Media Services and AOL. Opening up unparalleled scope for an event of this kind, it was a moment to relaunch a unified program and to bring in some heavy hitters to see what kind of gains we could make. The result: 12 hours of hacking netted $400,000 in payouts for verified bugs, a huge win for the safety and security of our users, as well as our platforms.
Since then, our program has seen a steady hum of submissions from security researchers around the world and, as of June, we surpassed $1,000,000 in payouts for verified bugs. This scale represents a significant decrease in risk and a considerable reduction of our attack surface. Every bug found and closed is a bug that cannot be exploited by our adversaries.
Bug submissions weren’t all we received from our security community. We also heard a ton of feedback that we’ve accounted for in five changes to our program policy. While we may not offer the highest payout amount for those moonshot bugs, we believe in building a program our security researchers engage with on a regular basis. This, in our view, is a better metric of success for the health and longevity of our program and subsequently our overall security. So what’s new?
- Bounties for more types of vulnerabilities. We have expanded our list of vulnerabilities that can receive bounties based on CVSS severity and the impact defined internally. We still prioritize SQLi, RCE and XXE/XMLi vulnerabilities, so they retain the top spots on our payout table. Note: All reports use the policy in effect on the date of submission.
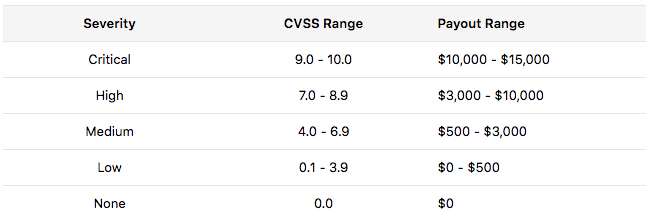
- The payout table is published. We have added this layer of transparency so that everyone can see the rewards up for grabs through the bug submission.
-
Shorter turnaround times. When we launched the program, Oath experienced an influx of interest. This meant our team took a little extra time to respond to the reports we received. Oath has committed to returning to our normal response times by following up on reports on a near-daily basis.
-
EdgeCast is joining the unified Oath program. The VDMS-EdgeCast-Partners and VDMS-EdgeCast-Customers private programs are now open to everyone who is part of this Oath private program. Previously these were private programs operated separately.
-
Structured scope for the suite of Oath brands. If you’ve looked at the Oath Brands page, you might have an idea of the scale of our bug bounty program. We will soon be defining structured scope items for each of Oath’s brands to help separate and define bugs for different assets.
The security landscape changes constantly, and we hope these updates to the bug bounty program will keep both Paranoids and security researchers alike more adept to detect threats before they cause damage to our community.
HackerOne is the #1 hacker-powered security platform, helping organizations find and fix critical vulnerabilities before they can be criminally exploited. As the contemporary alternative to traditional penetration testing, our bug bounty program solutions encompass vulnerability assessment, crowdsourced testing and responsible disclosure management. Discover more about our security testing solutions or Contact Us today.