Microsoft warns that financially-motivated threat actors are using OAuth applications to automate BEC and phishing attacks, push spam, and deploy VMs for cryptomining.
OAuth (short for Open Authorization) is an open standard for granting apps secure delegated access to server resources based on user-defined permissions via token-based authentication and authorization without providing credentials.
Recent incidents investigated by Microsoft Threat Intelligence experts revealed that attackers mainly target user accounts that lack robust authentication mechanisms (e.g., multi-factor authentication) in phishing or password-spraying attacks, focusing on those with permissions to create or modify OAuth apps.
The hijacked accounts are then used to create new OAuth applications and grant them high privileges, allowing their malicious activity to remain hidden while ensuring continued access even if the original account is lost.
These high-privileged OAuth apps are utilized for a broad spectrum of illicit activities, including deploying virtual machines dedicated to cryptocurrency mining, securing continued access in Business Email Compromise (BEC) attacks, and initiating spam campaigns that exploit the domain names of compromised organizations.
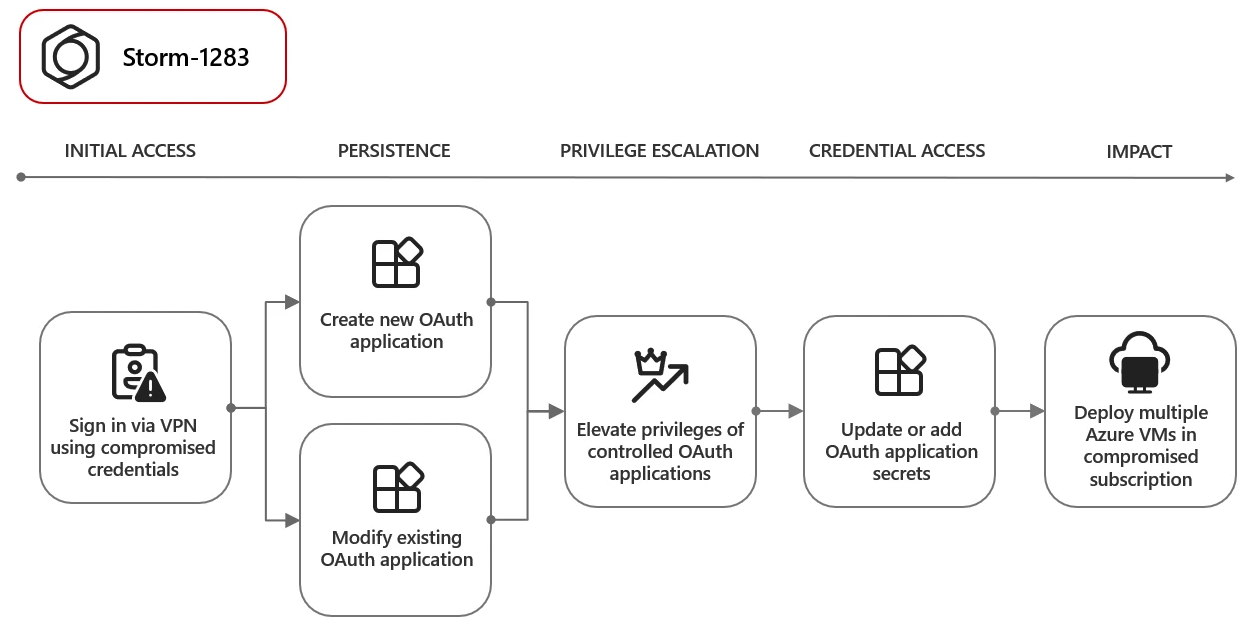
One notable instance involves a threat actor tracked as Storm-1283, who created an OAuth app to deploy cryptocurrency mining virtual machines. The financial impact on targeted organizations ranged from $10,000 to $1.5 million, depending on the attack’s duration.
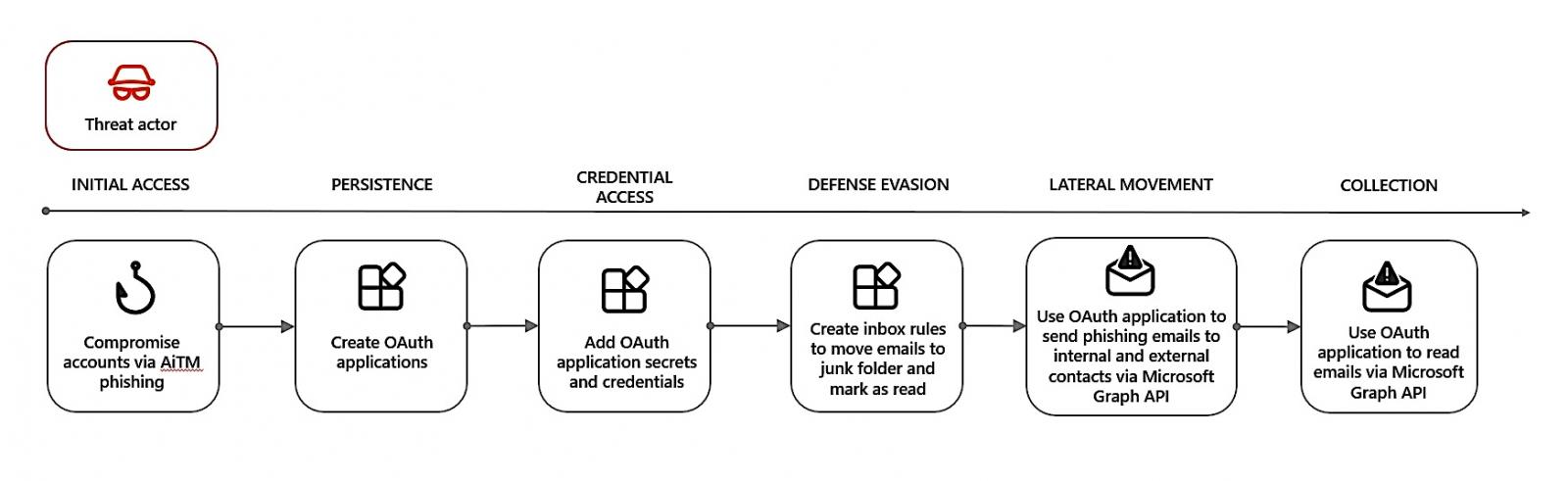
Another threat actor exploited OAuth apps created using compromised accounts to maintain persistence and launch phishing campaigns using an adversary-in-the-middle (AiTM) phishing kit.
The same assailant used the breached accounts for Business Email Compromise (BEC) reconnaissance by using Microsoft Outlook Web Application (OWA) to search for attachments linked to “payment” and “invoice.”
In separate instances, the attacker created multitenant OAuth apps for persistence, adding new credentials, and reading emails or sending phishing emails via the Microsoft Graph API.
“At the time of analysis, we observed that threat actor created around 17,000 multitenant OAuth applications across different tenants using multiple compromised user accounts,” Microsoft said.
“Based on the email telemetry, we observed that the malicious OAuth applications created by the threat actor sent more than 927,000 phishing emails. Microsoft has taken down all the malicious OAuth applications found related to this campaign, which ran from July to November 2023.”
A third threat actor tracked as Storm-1286 hacked user accounts that weren’t protected by multi-factor authentication (MFA) in a series of password-spraying attacks.
The compromised accounts were then used to create new OAuth apps in the targeted organization, which enabled the attackers to send thousands of spam emails every day and, in some cases, months after the initial breach.
To defend against malicious actors misusing OAuth apps, Microsoft recommends using MFA to thwart credential stuffing and phishing attacks.
Security teams should also enable conditional access policies to block attacks that leverage stolen credentials, continuous access evaluation to automatically revoke user access based on risk triggers, and Azure Active Directory security defaults to ensure MFA is enabled and privileged activities are protected.
