Okta is warning about custom phishing kits built specifically for voice-based social engineering (vishing) attacks. BleepingComputer has learned that these kits are being used in active attacks to steal Okta SSO credentials for data theft.
In a new report released today by Okta, researchers explain that the phishing kits are sold as part of an “as a service” model and are actively being used by multiple hacking groups to target identity providers, including Google, Microsoft, and Okta, and cryptocurrency platforms.
Unlike typical static phishing pages, these adversary-in-the-middle platforms are designed for live interaction via voice calls, allowing attackers to change content and display dialogs in real time as a call progresses.

The core features of these phishing kits are real-time manipulation of targets through scripts that give the caller direct control over the victim’s authentication process.
As the victim enters credentials into the phishing page, those credentials are forwarded to the attacker, who then attempts to log in to the service while still on the call.
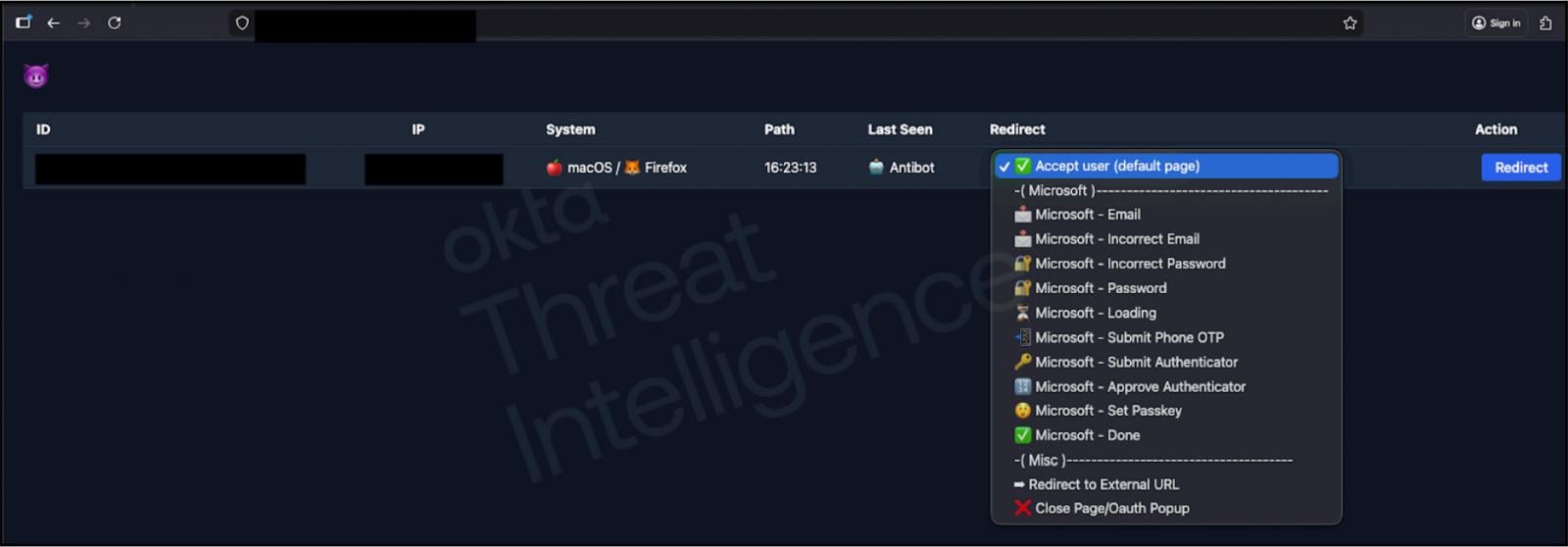
Source: Okta
When the service responds with an MFA challenge, such as a push notification or OTP, the attacker can select a new dialog that instantly updates the phishing page to match what the victim sees when attempting to log in. This synchronization makes fraudulent MFA requests appear legitimate.
Okta says these attacks are highly planned, with threat actors performing reconnaissance on a targeted employee, including which applications they use and the phone numbers associated with their company’s IT support.
They then create customized phishing pages and call the victim using spoofed corporate or helpdesk numbers. When the victim enters their username and password on the phishing site, those credentials are relayed to the attacker’s backend, commonly to Telegram channels operated by the threat actors.
This allows the attackers to immediately trigger real authentication attempts that display MFA challenges. While the threat actors are still on the phone with their target, they can direct the person to enter their MFA TOTP codes on the phishing site, which are then intercepted and used to log in to their accounts.
Okta says these platforms can bypass modern push-based MFA, including number matching, because attackers tell victims which number to select. At the same time, the phishing kit C2 causes the website to display a matching prompt in the browser.
Okta recommends that customers use phishing-resistant MFA such as Okta FastPass, FIDO2 security keys, or passkeys.
Attacks used for data theft
This advisory comes after BleepingComputer learned that Okta privately warned its customers’ CISOs earlier this week about the ongoing social engineering attacks.
On Monday, BleepingComputer contacted Okta after learning that threat actors were calling targeted companies’ employees to steal their Okta SSO credentials.
Okta is a cloud-based identity provider that acts as a central login system for many of the most widely used enterprise web services and cloud platforms.
Its single sign-on (SSO) service allows employees to authenticate once with Okta and then gain access to other platforms used by their company without having to log in again.
Platforms that integrate with Okta SSO include Microsoft 365, Google Workspace, Dropbox, Salesforce, Slack, Zoom, Box, Atlassian Jira and Confluence, Coupa, and many more.
Once logged in, Okta SSO users are given access to a dashboard that lists all of their company’s services and platforms, allowing them to click and access them. This makes Okta SSO act as a gateway to a company’s business-wide services.

Source: Okta
At the same time, this makes the platform extremely valuable for threat actors, who now have access to the company’s widely used cloud storage, marketing, development, CRM, and data analytics platforms.
BleepingComputer has learned that the social engineering attacks begin with threat actors calling employees and impersonating IT staff from their company. The threat actors offer to help the employee set up passkeys for logging into the Okta SSO service.
The attackers trick employees into visiting a specially crafted adversary-in-the-middle phishing site that captures their SSO credentials and TOTP codes, with some of the attacks relayed in real time through a Socket.IO server previously hosted at inclusivity-team[.]onrender.com.
The phishing websites are named after the company, and commonly contain the word “internal” or “my”.
For example, if Google were targeted, the phishing sites might be named googleinternal[.] com or mygoogle[.]com.
Once an employee’s credentials are stolen, the attacker logs in to the Okta SSO dashboard to see which platforms they have access to and then proceeds to steal data from them.
“We gained unauthorized access to your resources by using a social-engineering-based phishing attack to compromise an employee’s SSO credentials,” reads a security report sent by the threat actors to the victim and seen by BleepingComputer.
“We contacted various employees and convinced one to provide their SSO credentials, including TOTPs.”
“We then looked through various apps on the employee’s Okta dashboard that they had access to looking for ones that dealt with sensitive information. We mainly exfiltrated from Salesforce due to how easy it is to exfiltrate data from Salesforce. We highly suggest you to stray away from Salesforce, use something else.”
Once they are detected, the threat actors immediately send extortion emails to the company, demanding payment to prevent the publication of data.
Sources tell BleepingComputer that some of the extortion demands sent by the threat actors are signed by ShinyHunters, a well-known extortion group behind many of last year’s data breaches, including the widespread Salesforce data theft attacks.
BleepingComputer asked ShinyHunters to confirm if they were behind these attacks but they declined to comment.
At this time, BleepingComputer has been told that the threat actors are still actively targeting companies in the Fintech, Wealth management, financial, and advisory sectors.
Okta shared the following statement with BleepingComputer regarding our questions about these attacks.
“Keeping customers secure is our top priority. Okta’s Defensive Cyber Operations team routinely identifies phishing infrastructure configured to imitate an Okta sign-in page and proactively notifies vendors of their findings,” reads a statement sent to BleepingComputer.
“It is clear how sophisticated and insidious phishing campaigns have become and it’s crucial that companies take all necessary measures to secure their systems and continue to educate their employees on vigilant security best practices.”
“We provide our customers best practices and practical guidance to help them identify and prevent social engineering attacks, including the recommendations detailed in this security blog https://www.okta.com/blog/threat-intelligence/help-desks-targeted-in-social-engineering-targeting-hr-applications/ and the blog we published today https://www.okta.com/blog/threat-intelligence/phishing-kits-adapt-to-the-script-of-callers/.”

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.



