US fiber broadband company Brightspeed is investigating claims by the Crimson Collective extortion group that it stole sensitive data belonging to more than 1 million residential customers, including extensive personally identifiable information (PII), as well as account and billing details.
Brightspeed is one of the largest fiber broadband providers in the US and serves customers across 20 states.
On January 4, the Crimson Collective posted this message on its Telegram channel:
“If anyone has someone working at BrightSpeed, tell them to read their mails fast!
We have in our hands over 1m+ residential user PII’s, which contains the following:
- Customer/account master records containing full PII such as names, emails, phone numbers, billing and service addresses, account status, network type, consent flags, billing system, service instance, network assignment, and site IDs.
- Address qualification responses with address IDs, full postal addresses, latitude and longitude coordinates, qualification status (fiber/copper/4G), maximum bandwidth, drop length, wire center, marketing profile codes, and eligibility flags.
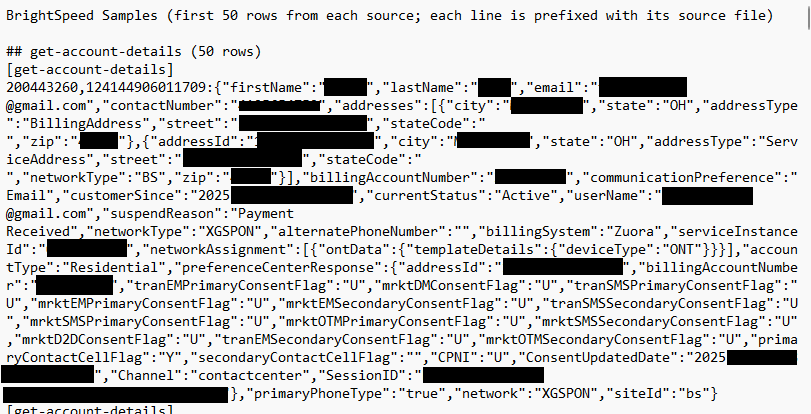
- User-level account details keyed by session/user IDs, overlapping with PII including names, emails, phones, service addresses, account numbers, status, communication preferences, and suspend reasons.
- Payment history per account, featuring payment IDs, dates, amounts, invoice numbers, card types and masked card numbers (last 4 digits), gateways, and status; some entries indicate null or empty histories.
- Payment methods per account, including default payment method IDs, gateways, masked credit card numbers, expiry dates, BINs, holder names and addresses, status flags (Active/Declined), and created/updated timestamps.
- Appointment/order records per billing account, with customer PII such as names, emails, phones, addresses, order numbers, status, appointment windows, dispatch and technician information, and install types.
Sample will be dropped on monday night time, letting them some time first to answer to us. (UTC+9, Japan is quite fun for new years while dumping company data)”
The promised sample was later made available and contains 50 entries from each of the following database tables:
- [get-account-details]
- [getAddressQualification]
- [getUserAccountDetails]
- [listPaymentHistory]
- [listPaymentMethods]
- [user-appointments]
In a separate Telegram message, the group also claimed it had disconnected a large number of Brightspeed customers. However, this allegation appears only in the group’s own messaging and has not been corroborated by any public reporting.
While there are some customer complaints circulating on social media, it remains unclear whether these issues are actually caused by any actions taken by the Crimson Collective.

Brightspeed told BleepingComputer:
“We take the security of our networks and protection of our customers’ and employees’ information seriously and are rigorous in securing our networks and monitoring threats. We are currently investigating reports of a cybersecurity event. As we learn more, we will keep our customers, employees and authorities informed.”
Protecting yourself after a data breach
If you think you have been affected by a data breach, here are steps you can take to protect yourself:
- Check the company’s advice. Every breach is different, so check with the company to find out what’s happened and follow any specific advice it offers.
- Change your password. You can make a stolen password useless to thieves by changing it. Choose a strong password that you don’t use for anything else. Better yet, let a password manager choose one for you.
- Enable two-factor authentication (2FA). If you can, use a FIDO2-compliant hardware key, laptop, or phone as your second factor. Some forms of 2FA can be phished just as easily as a password, but 2FA that relies on a FIDO2 device can’t be phished.
- Watch out for impersonators. The thieves may contact you posing as the breached platform. Check the official website to see if it’s contacting victims and verify the identity of anyone who contacts you using a different communication channel.
- Take your time. Phishing attacks often impersonate people or brands you know, and use themes that require urgent attention, such as missed deliveries, account suspensions, and security alerts.
- Consider not storing your card details. It’s definitely more convenient to let sites remember your card details, but we highly recommend not storing that information on websites.
- Set up identity monitoring, which alerts you if your personal information is found being traded illegally online and helps you recover after.
We don’t just report on threats—we help safeguard your entire digital identity
Cybersecurity risks should never spread beyond a headline. Protect your, and your family’s, personal information by using identity protection.