It was just a little over a year ago that the Rhadamanthys stealer was first publicly seen distributed via malicious ads. Throughout 2023, we observed a continuation in malvertising chains related to software downloads.
Fast forward to 2024 and the same malvertising campaigns are still going on. After a lull last summer, we noticed an increase since the fall which so far has been sustained. The most recent targeted searches are for Parsec and FreeCad, followed by WinSCP, Advanced IP Scanner, Slack and Notion.
Threat actors are targeting business users with payloads such as FakeBat, Nitrogen or Hijackloader. One other malware family we have seen here and there is Rhadamanthys. In this blog post, we detail the latest distribution chain related to this malware.
Key points
- Rhadamanthys is an infostealer distributed via malspam and malvertising.
- Google searches for popular software such as Notion return malicious ads.
- Threat actors are using decoy websites to trick users into downloading malware.
- The initial payload is a dropper that retrieves Rhadamanthys via a URL pasted online.
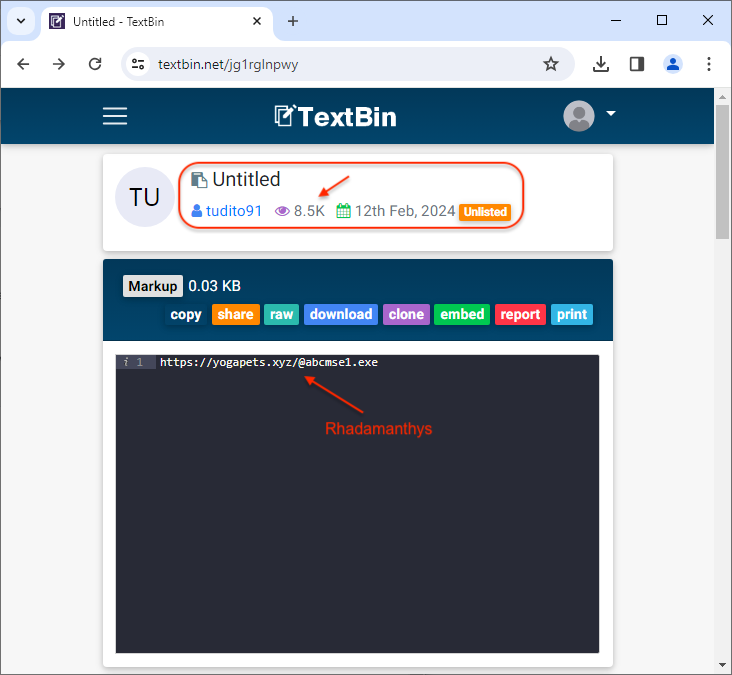
- The TexBin paste site shows the URL was seen/accessed 8.5K times.
Malicious ad
Threat actors continue to impersonate well-known brands via sponsored search results. As can be seen below in a search for Notion (productivity software), an extremely deceiving ad is shown. Because it includes the official logo and website for Notion, most users will not think twice and click on the link.
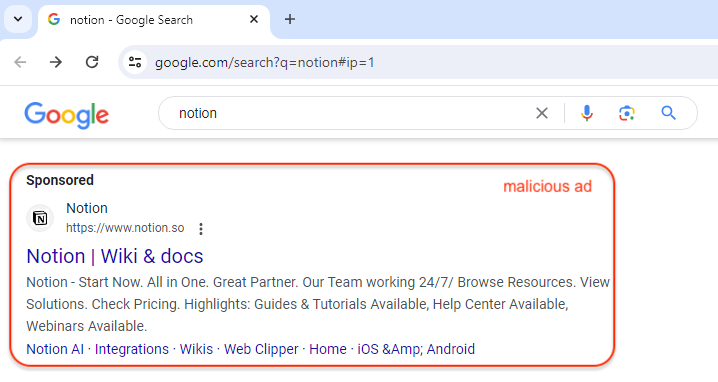
While the ad looks real on the surface, the Google Ads Transparency Center page (which can be accessed by clicking on the menu right next to the ad’s URL) shows this ad was created by a certain ‘BUDNIK PAWEŁ’ from Poland. According to the same report, the first ad first appeared on January 23, 2024.
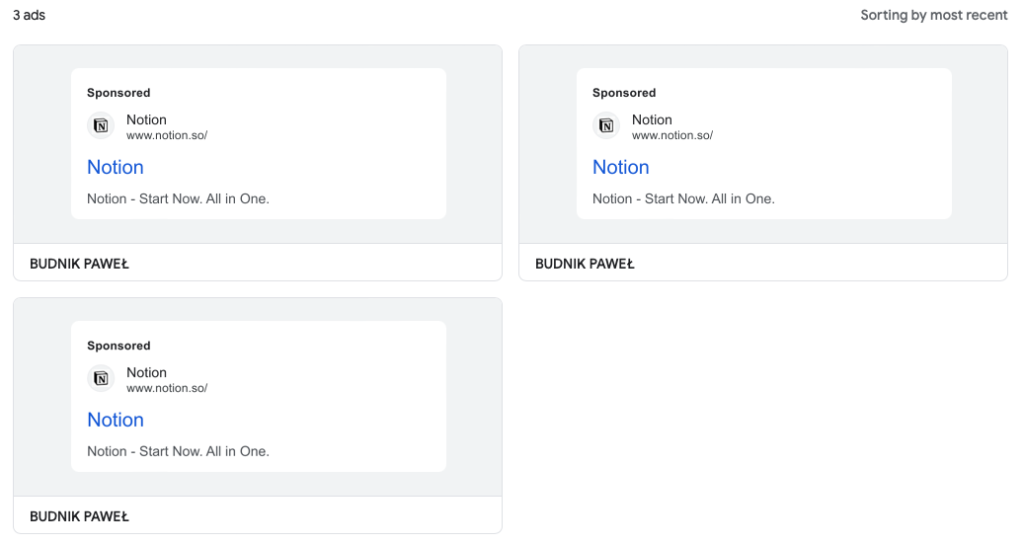
As a matter of fact, we have been tracking this fraudulent advertiser for a few weeks and had reported it to Google in early February, when we first ran into it. At the time, victims who clicked the ad and visited the site were tricked with a download for NetSupport RAT.
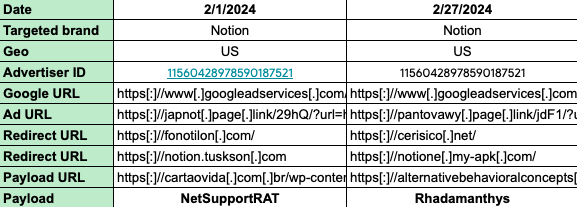
In this more recent campaign, the threat actor is pushing Rhadamanthys as the final payload, after an initial dropper. In the web traffic seen below, we can see that the threat actor uses a number of redirects to evade detection. URL shorteners and redirectors are quite common for the initial ad click, often followed by an attacker-controlled domain responsible for cloaking traffic.
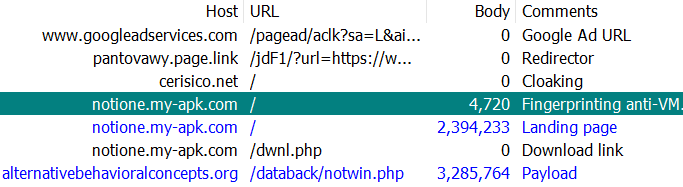
There is one more check within the browser via JavaScript to detect virtual machines before the actual landing page is displayed to the victim.
Landing page and payload
The landing page is the decoy site that victims will see after they click on the ad. Apart from the URL in the address bar, it looks very similar to the official web site for Notion, although somewhat simplified. There are two download buttons, one for Mac and the other for Windows.
The Windows binary is a signed file but its digital signature is not valid. The name of the signer that shows here is from the inventor of PuTTY, a popular admin tool. This digital certificate is likely fake or was revoked, but it may evade detection in some cases.
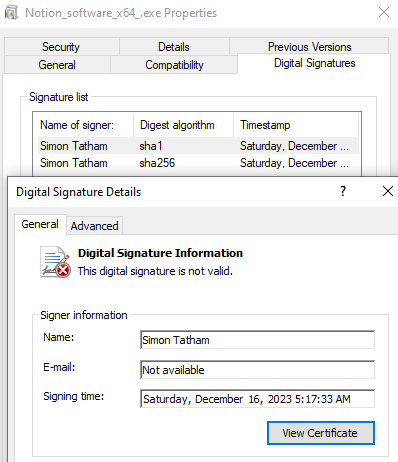
This dropper contacts the paste site TextBin where it retrieves a URL for the followup payload, Rhadamanthys. If the numbers are correct this unlisted paste was viewed 8.5k times already.
Rhadamanthys attempts to steal credentials stored in applications such as PuTTY, WinSCP and mail programs (screenshot from Joe Sandbox):

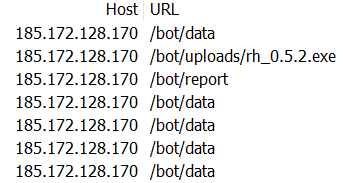
Upon execution, Rhadamanthys reports to its command and control server, sends and receives data.
Conclusion
Not a lot has changed with malvertising campaigns focused on software downloads as we enter the second year of actively tracking them. Sponsored search results continue to be highly misleading due to the fact that any verified individual is able to impersonate popular brands by using their logo and official site within the ad itself.
We are aware of reports shared within private circles, that businesses were compromised after an employee clicked on a malicious ad. Follow-up activities post infection include the usual ‘pentesting tools’ that precede a company-wide breach or ransomware deployment.
The infrastructure used in this particular attack was reported to the relevant parties. Malwarebytes and ThreatDown customers are protected against the payloads and distribution sites.
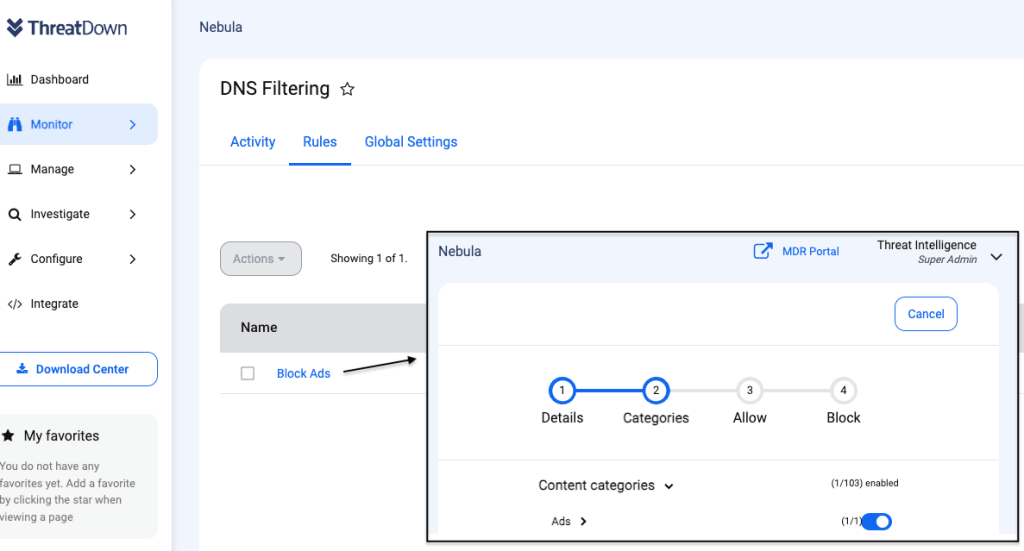
Additionally, EDR customers who have DNS Filtering can proactively block online ads by enabling the rule for advertisements. This is a simple, and yet powerful way to prevent malvertising across an entire organization or in specific areas.
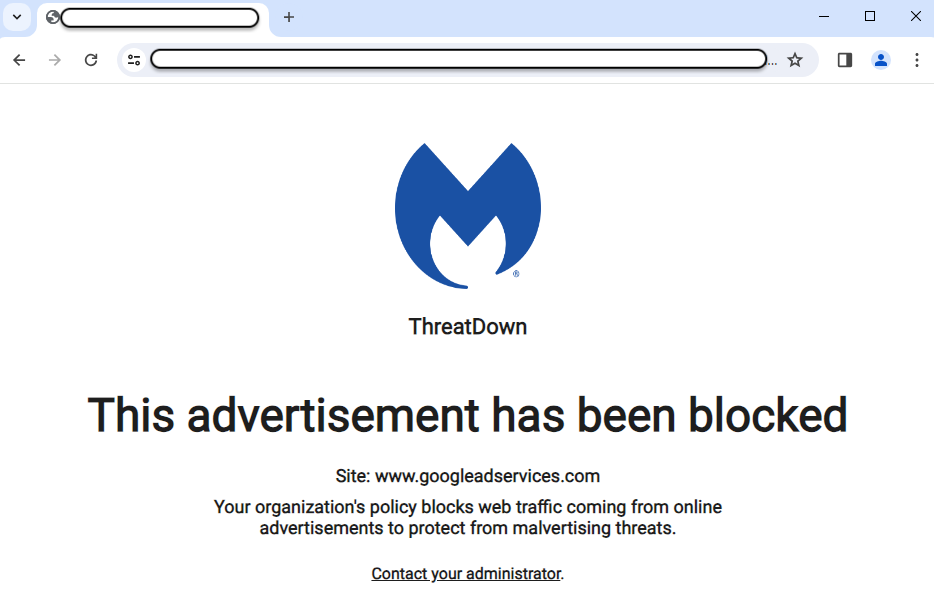
Endpoint users will see a customizable message when they click on an ad such as those that appear on a search engine results page:
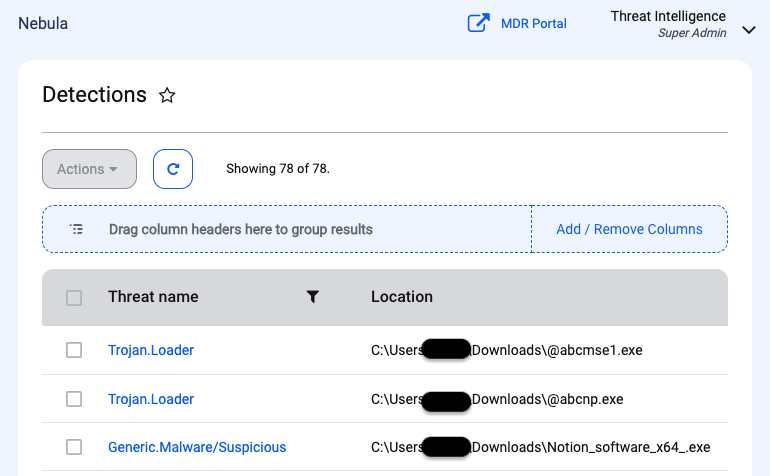
Indicators of Compromise
Malvertising chain
pantovawy.page[.]link cerisico[.]net notione.my-apk[.]com alternativebehavioralconcepts[.]org
Dropper
6f4a0cc0fa22b66f75f5798d3b259d470beb776d79de2264c2affc0b5fa924a2
Dropper IP
185[.]172[.]128[.]169
Rhadamanthys download URL
yogapets[.]xyz/@abcmse1.exe birdarid[.]org/@abcnp.exe
Rhadamanthys
e179a9e5d75d56140d11cbd29d92d8137b0a73f964dd3cfd46564ada572a3109 679fad2fd86d2fd9e1ec38fa15280c1186f35343583c7e83ab382b8c255f9e18
Rhadamanthys C2
185[.]172[.]128[.]170
