A newly discovered spearphishing campaign is targeting executives and senior leadership across multiple industries by exploiting trusted OneDrive document‐sharing notifications.
The Stripe OLT SOC has identified this sophisticated attack, which leverages highly tailored emails to impersonate internal HR communications and harvest corporate credentials through a convincing Microsoft Office/OneDrive login page.
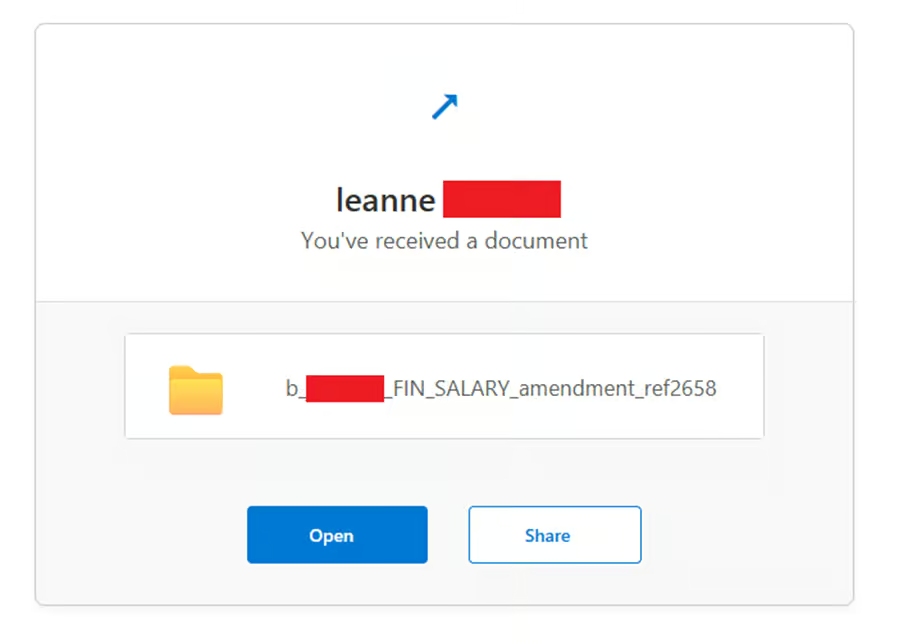
At the heart of the campaign are subject lines referencing “Salary amendment” or “FIN_SALARY,” designed to trigger concern and urgency among C-suite and leadership recipients.
Emails appear to originate from OneDrive’s document-sharing system, claiming that a shared file requires immediate review. When clicked, the embedded link directs victims to a credential theft page that perfectly mimics Microsoft’s Office 365 login interface.
Both the phishing email and the subsequent login page are customized with the recipient’s name and company details, lending an air of authenticity that fools even vigilant professionals.
Actors behind this operation are using Amazon Simple Email Service (SES) for delivery, rotating among roughly 80 domains and subdomains to evade detection by secure email gateways.
Domains are frequently registered through Mat Bao Corporation and Web Commerce Communications Limited (WebNic.cc), with DNS and nameserver services provided by Cloudflare and Luxhost.
Hosting infrastructure for the phishing pages resides on Akamai Cloud (formerly Linode). To “warm up” inboxes and avoid spam filters, the attackers send benign emails days before the malicious ones, establishing familiarity with the target mail servers.
Anti-detection techniques are a hallmark of this campaign. The attackers embed hidden characters and obfuscate high-value trigger words like “Open” and “Share” in separate light and dark mode renditions of the email body. In Light Mode, buttons display as ordinary clickable text: “Open” and “Share.”
In Dark Mode, concealed padding reveals randomized alphanumeric strings—such as twPOpenHuxv and gQShareojxYI—breaking up regex-based detection patterns. Single-use phishing URLs self-destruct upon access, further complicating incident response and forensic analysis.
Security experts warn that this campaign’s focus on C-level targets and the use of trusted internal communication themes make it especially dangerous.
Executives—often pressed for time and accustomed to receiving high volumes of messages—may bypass normal suspicion thresholds when confronted with an “HR‐related” document. The inclusion of real names and company logos heightens the illusion of legitimacy.
To mitigate the threat, organizations should implement a blend of user awareness, technical controls, and proactive threat hunting:
- Executive and Assistant Awareness
Conduct targeted briefings for C-suite personnel and their assistants, highlighting the campaign’s use of “salary amendment” themes and OneDrive notifications. - Document Link Skepticism
Reinforce policies requiring verification of HR or payroll links. Encourage recipients to access documents only through known corporate portals. - Rapid Reporting Mechanisms
Establish clear escalation paths for reporting suspicious emails to security teams. Early detection can prevent credential harvesting at scale. - Comprehensive Training
Extend phishing simulations and training to executive support staff, who are equally high-value targets for lateral credential attacks. - Technical Controls and IOC Hunting
Security and IT teams should hunt for indicators of compromise (IOCs) associated with this campaign’s domains and email patterns. Blocking SES-hosted emails from unrecognized subdomains and registrars can reduce exposure.
For proactive threat detection in Microsoft Sentinel, SOC analysts recommend the following KQL query to identify inbound emails matching the observed subject lines:
textEmailEvents
| where Subject contains "FIN_SALARY"
| where EmailDirection == "Inbound"
| project Timestamp, RecipientEmailAddress, SenderMailFromDomain, Subject, ConfidenceLevel, NetworkMessageId, EmailAction
By combining heightened vigilance among executives, robust user training for assistants, and targeted technical controls, organizations can defend against this advanced OneDrive spearphishing campaign and safeguard critical corporate credentials.
Find this Story Interesting! Follow us on LinkedIn and X to Get More Instant Updates.
