
PcComponentes, a major technology retailer in Spain, has denied claims of a data breach on its systems impacting 16 million customers, but confirmed it suffered a credential stuffing attack.
The Spanish e-commerce company specializes in the sale of computers, laptops, peripherals, and hardware, and has an estimated 75 million unique marketplace visitors per year.
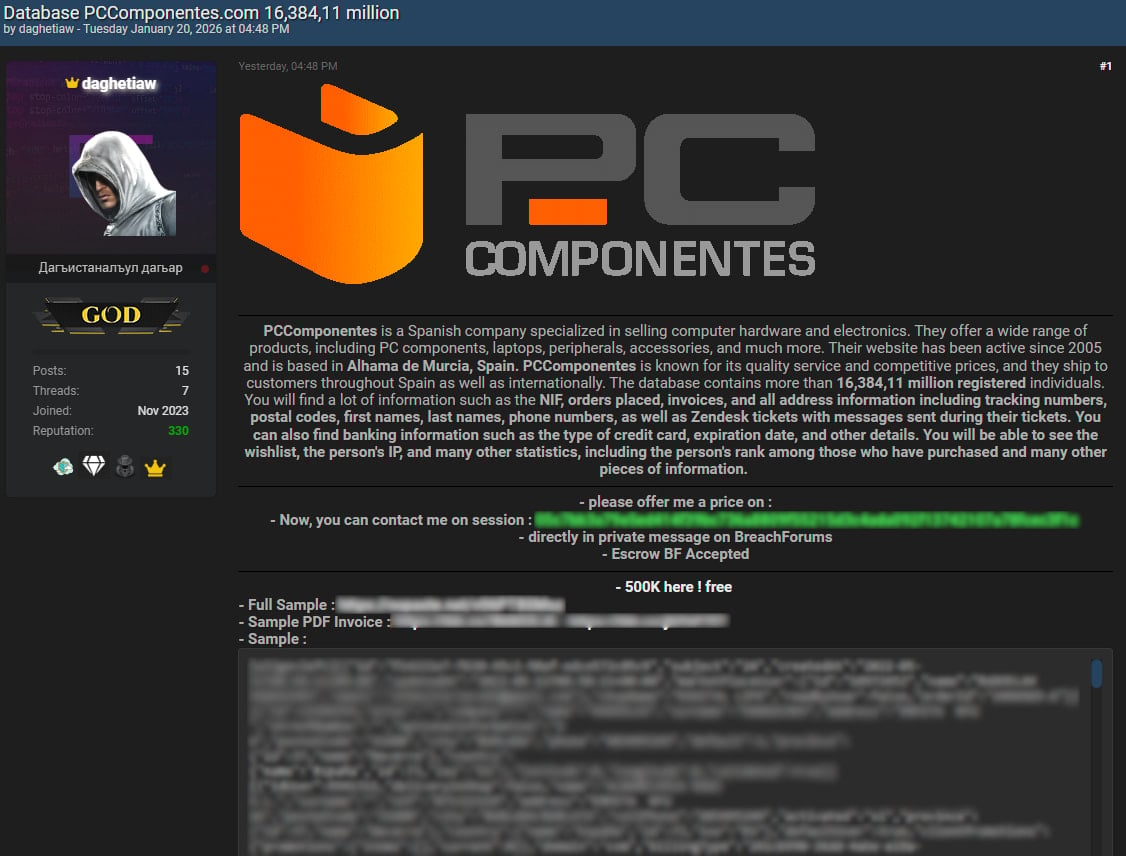
Yesterday, a threat actor named ‘daghetiaw’ published what they claimed to be a customer database stolen from PcComponentes, containing 16.3 million records. The threat actor leaked 500,000 records and offered to sell the rest to the highest bidder.

The leaked data contains order details, physical addresses, full names, phone numbers, IP addresses, product wish-lists, and customer support messages exchanged with the firm via Zendesk.
Source: BleepingComputer
In an announcement today, PcComponents says that it investigated a possible breach of its systems, but its security experts found no evidence of unauthorized access.
“There has been no illegitimate access to our databases or internal systems,” the company assures, adding that “the figure of 16 million supposedly affected customers is false, as the number of active PcComponentes accounts is significantly lower.”
The company also underlined that no financial details or customer passwords are stored on its systems.
However, PcComponentes admitted that its investigation discovered evidence of a credential stuffing attack on its platform. This means that a threat actor tried email addresses and passwords from other security breaches or leaked databases to find PcComponentes accounts.
Credential stuffing attacks are typically automated and rely on large volumes of reused login credentials from other services.
An investigation from threat intelligence company Hudson Rock discovered that the attackers likely collected the login data from computers infected with info-stealing malware.
“Every single email we checked from the threat actor’s sample was found in existing infostealer logs,” Hudson Rock says in a post today, adding that some of the logins were as old as 2020.
A screenshot that Hudson Rock published shows a set of six email addresses that were verified and all of them were marked as previously compromised in infostealer infections.
According to PcComponentes’ announcement, the following data was exposed for a small number of compromised accounts:
- First and last names
- National ID number
- Physical addresses
- IP addresses
- Email addresses
- Phone numbers
In response to the incident, PcComponentes has implemented a set of defenses that include CAPTCHA on the login pages, mandatory activation of two-factor authentication (2FA) for all accounts, and invalidation of all active sessions.
As a result, customers will be automatically logged out, and accounts without two-factor authentication (2FA) will be required to enable it before regaining access.
PcComponentes also recommends that customers use strong, unique passwords for each account, store their passwords in a password manager, and stay vigilant for potential phishing messages.
BleepingComputer has contacted PcComponentes to ask how many customers have been impacted precisely, but a statement wasn’t immediately available.

It’s budget season! Over 300 CISOs and security leaders have shared how they’re planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
