In a recent cyber assault on the popular creator-led content-sharing platform, OnlyFans, the services were brought to a grinding halt for a one-hour duration.
The OnlyFans cyber attack, attributed to Anonymous Sudan, left the website non-operational during that time, marking a significant downtime.
While the threat actor claimed responsibility for the OnlyFans cyber attack, it was part of a broader campaign targeting companies in the United States, including Microsoft Azure and CNN.
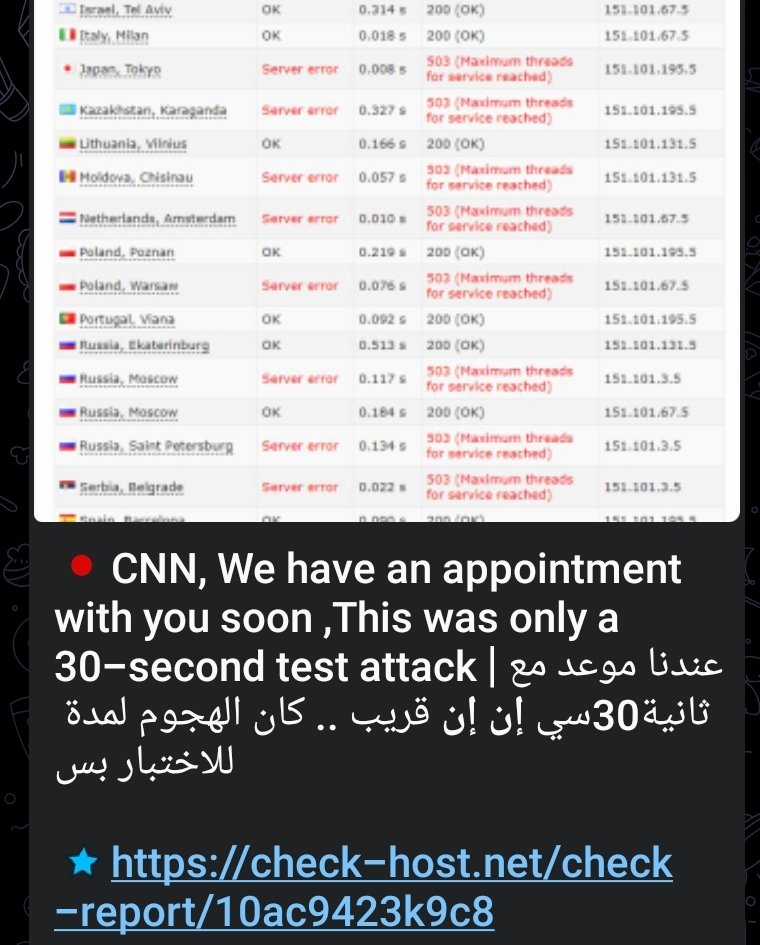
Anonymous shared a post on the internet, exclusively marking CNN alongside OnlyFans, as one of its victims in the attack.
“CNN, we have an appointment with you soon, This was only a 30-second text attack”, reads the threat actor post.
Moreover, along with the alleged OnlyFans cyber attack, the threat actor has been posting data breach claims over the last few weeks, naming big corporations in the US as its victims.
The Cyber Express reached out to the platform to learn more about the alleged OnlyFans cyber attack. However, at the time of writing this, no official statement or response had been received. We will update the report on receiving a confirmation from the company.
The growing threat of OnlyFans cyber attack
OnlyFans, a London-based internet content subscription service, is primarily known for its usage by adult industry workers to share adult content.
Nevertheless, it also accommodates other creators, including fitness experts and musicians. Regrettably, this diverse user base and the presence of sensitive content have made it an attractive target for cyber attackers seeking to exploit its vulnerabilities.
In a recent incident, a malicious campaign aimed at smartphone users was discovered, leveraging fake OnlyFans content to disseminate the malicious Remote Access Trojan (RAT) known as DcRAT malware.
This campaign, active since January 2023, poses a significant threat to users’ devices and personal data.
The campaign’s modus operandi involves luring victims with explicit OnlyFans content, specifically targeting those who engage with adult-oriented photos and videos.
Once enticed, victims are prompted to download ZIP files containing a VBScript loader, purportedly granting access to premium OnlyFans content.
Unbeknownst to them, executing this action installs the DcRAT Trojan, granting hackers remote control over their devices. DcRAT exhibits a multifaceted threat, including keylogging, webcam monitoring, file manipulation, device access, and theft of web browser credentials and tokens.
The dark side of OnlyFans cyber attack

While the recent OnlyFans cyber attack by Anonymous Sudan can garner significant attention, it represents only one facet of the threat landscape.
Another alarming aspect emerges from exploiting unsuspecting internet users, who fall prey to fake websites and webpages offering “OnlyFans tricks” or “OnlyFans Mods” to lure them into clicking malicious links.
These deceptive websites promise users free photos, videos, and other content, but in reality, they harbor hackers who distribute manipulated versions of the OnlyFans APK.
The .APK file, commonly used by the Android operating system for managing apps, becomes a potential gateway for attackers to compromise devices.
Though not on the scale of large-scale campaigns against corporations like the Anonymous Sudan’s claimed OnlyFans cyber attack, these assaults demonstrate the criminal side of the internet and exploit vulnerable users.
Media Disclaimer: This report is based on internal and external research obtained through various means. The information provided is for reference purposes only, and users bear full responsibility for their reliance on it. The Cyber Express assumes no liability for the accuracy or consequences of using this information.
