Risk management company Crisis24 has confirmed its OnSolve CodeRED platform suffered a cyberattack that disrupted emergency notification systems used by state and local governments, police departments, and fire agencies across the United States.
The CodeRED platform enables these agencies to send alerts to residents during emergencies.
The cyberattack forced Crisis24 to decommission the legacy CodeRED environment, causing widespread disruption for organizations that use the platform for emergency notifications, weather alerts, and other sensitive warnings.

In statements and an FAQ shared with impacted customers, Crisis24 says its investigation found that the attack was contained to the CodeRED environment and did not affect any of its other systems.
However, they have confirmed that data was stolen from the platform during the attack. This stolen information includes names, addresses, email addresses, phone numbers, and passwords used for CodeRED user profiles.
Crisis24 tells customers that they have seen no indication that the stolen data has been publicly published.
“CodeRED has informed us that while there are indications that data was taken from the system, at this time, there is no evidence that this information has been posted online,” warned an announcement by the City of University Park, Texas.
Because the attack damaged the platform, Crisis24 is rebuilding its service by restoring backups to a newly launched CodeRED by Crisis24 system. However, the available data is from an earlier backup on March 31, 2025, so accounts will likely be missing from the system.
Numerous counties, cities, and public safety agencies nationwide have reported on the cyberattack and disruption, stating that they are working to restore emergency alert systems for their residents.
INC Ransom gang claims responsibility
While Crisis24 only attributed the breach to an “organized cybercriminal group,” BleepingComputer has learned that the INC Ransomware gang has taken responsibility for the attack.
The group created an entry for OnSolve on its Tor data leak site and published screenshots that appear to show customer data, including email addresses and associated clear-text passwords.
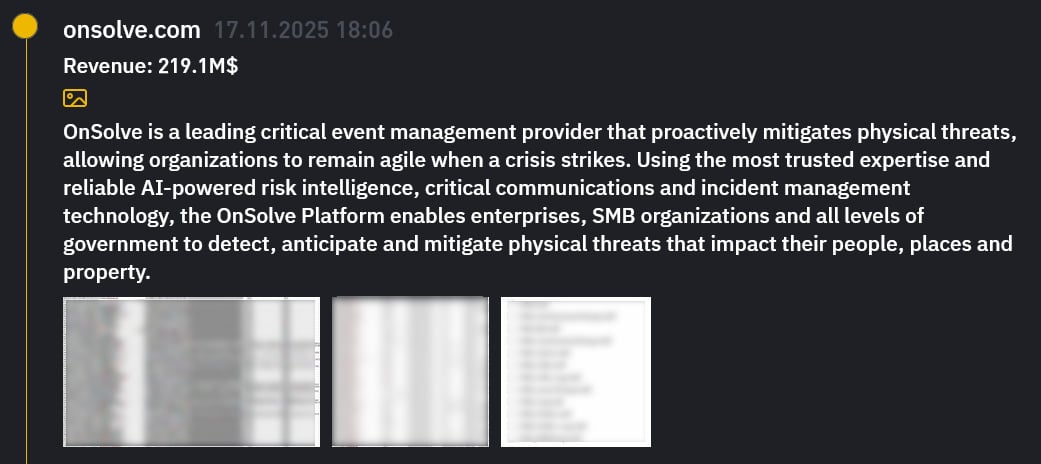
Source: BleepingComputer
The ransomware gang claims to have breached OnSolve’s systems on November 1, 2025, and encrypted files on November 10. After allegedly failing to receive a ransom payment, the threat actors say they are now selling the data stolen during the attack.
As the passwords shared in the screenshots are in clear text, customers are advised to reset any CodeRED passwords that were reused on other sites.
INC Ransom is a ransomware-as-a-service (RaaS) operation that launched in July 2023 and has since targeted organizations worldwide.
Its list of victims spans a wide range of sectors, from education and healthcare to government and entities like Yamaha Motor Philippines, Scotland’s National Health Service (NHS), food retail giant Ahold Delhaize, and the U.S. division of Xerox Business Solutions (XBS).

Whether you’re cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
