Phishing attacks using open redirect flaws are on the rise again, according to Kroll’s Cyber Threat Intelligence (CTI) team, which means organizations should consider refreshing employees’ awareness and knowledge on how to spot them.
Malicious URL redirection
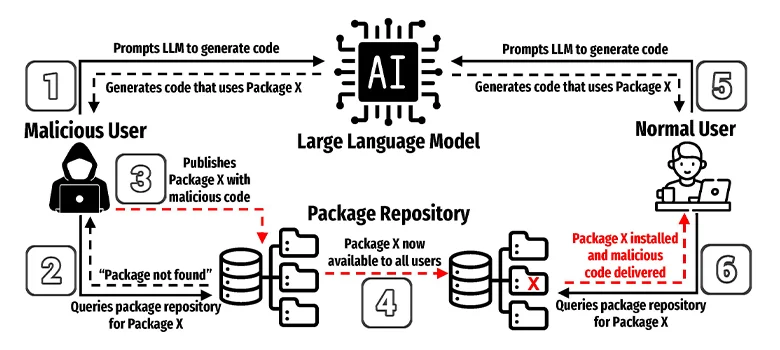
Open redirect vulnerabilities in web applications allows threat actors to manipulate legitimate URLs to redirect victims to an external malicious URL.
“They occur when a website allows for user-supplied input as part of a URL parameter in a redirect link, without proper validation or sanitization,” says George Glass, Kroll’s Head of Threat Intelligence.
Anatomy of an open redirect link. (Source: Kroll)
The targets are more inclined to trust the URL because the first part of it usually contains a trustworthy, legitimate domain. Once the victim is redirected to a malicious site, threat actors can steal sensitive information, such as login credentials, credit card details or personal data.
URL redirection is not, in itself, a malicious technique. For example, URLs that have been shortened via URL shortening services are often used by organizations to make URLs reflect their brand and easier to share, and they lead to legitimate, benign web pages.
Unfortunately, shortened URLs in phishing emails and direct messages usually point to malicious pages. (URL shortening is just one of the many URL redirection tricks employed by attackers.)
Employees as the last line of defense
By leveraging phishing kits to create seemingly legitimate sites and take advantage of open redirect vulnerabilities, phishers are able to successfuly trick victims into clicking URLs embedded within phishing emails.
While the campaigns Kroll observed used email as the attack vector, the open redirect technique can be used to deliver legitimate-looking links via social media, forum posts, text/IM messages or enterprise tools – and users are less likely to be wary of those.
Organizations should implement email security tools that can detect and block open redirect links in emails, he says. But since such defenses are regularly bypassed, employees should have regular cybersecurity training to update their knowledge on social engineering techniques used to deliver malware or lead to phishing pages, and they should be given the means to easily report possible threats.