Operation DreamJob, a longstanding North Korean cyberespionage campaign, has once again demonstrated its lethal effectiveness by targeting manufacturing organizations through deceptive job-related messages delivered via WhatsApp Web.
In August 2025, Orange Cyberdefense’s CyberSOC and CSIRT investigated an intrusion targeting an Asian subsidiary of a large European manufacturing organization, revealing how threat actors leveraged social engineering and advanced malware variants to breach enterprise networks and maintain persistent access.
The initial attack vector remains disturbingly simple yet highly effective. A WhatsApp message claiming to offer a Project Manager position lured a project engineer into downloading a ZIP archive containing a malicious PDF file, a legitimate SumatraPDF.exe executable, and a trojanized DLL named libmupdf.dll.
This technique exploits human psychology and trust in familiar recruitment processes a hallmark of Operation DreamJob’s approach since its emergence in 2016.
Upon opening the PDF, the legitimate application sideloaded the malicious DLL, executing a backdoor that would grant threat actors initial network access.
The sophistication of this attack lies not merely in the initial compromise but in the multi-stage infection chain that followed.
Once inside the network, the threat actors deployed hands-on-keyboard activities for at least six consecutive hours, leveraging compromised WordPress sites with vulnerable plugins as command-and-control infrastructure.
The attackers systematically conducted reconnaissance by making multiple LDAP queries to extract Active Directory lists of users and computers.
They subsequently compromised both backup and administrative accounts, employing the pass-the-hash technique to move laterally across domain servers without requiring plaintext passwords.
Operation DreamJob Attacks
The malware arsenal deployed in this campaign represents an evolution of previously observed Operation DreamJob variants.
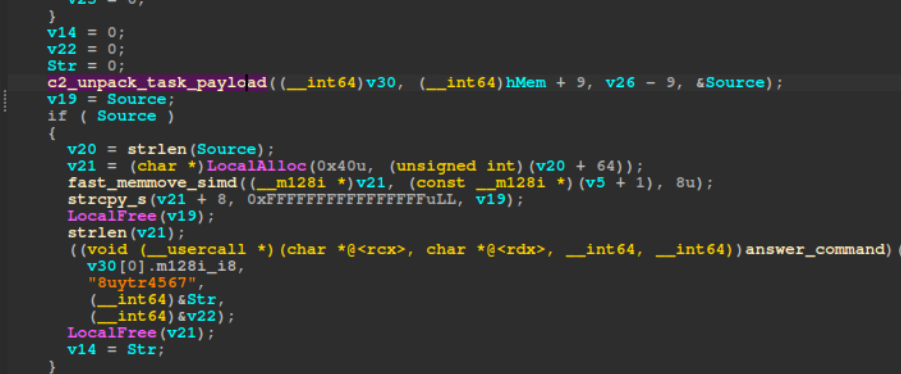
The libmupdf.dll file analyzed by Orange Cyberdefense exhibits substantial code overlaps with BURNBOOK samples documented in 2024, though the 2025 variant implements simplified functionality optimized for enterprise environments.
Notably, the newer BURNBOOK version dynamically loads netapi32.dll and netutils.dll to detect domain-joined systems a feature suggesting the threat actors specifically target corporate infrastructure rather than individual systems.
What elevates this campaign’s threat level is the deployment of MISTPEN, a sophisticated backdoor responsible for downloading and executing secondary payloads.
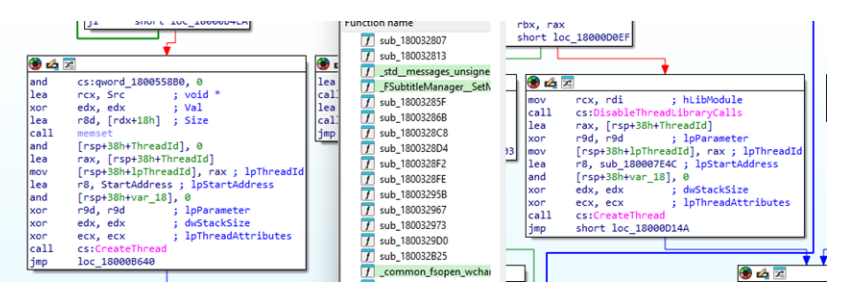
The analysis revealed that MISTPEN was injected into legitimate binaries to establish command-and-control communications with SharePoint based infrastructure.
This multi-stage approach culminated in the deployment of ReleasePvPluginx64.dll, an information-stealing module that exfiltrates sensitive data from compromised systems.
The attribution of this attack to UNC2970, linked to North Korean state-sponsored activities, underscores the persistence and resources dedicated to targeting critical manufacturing sectors.
Social Engineering Campaign
Manufacturing organizations remain attractive targets due to their intellectual property value, supply chain significance, and technology development capabilities.
The campaign’s use of job-related lures specifically targets technical professionals project engineers, developers, and system administrators individuals who typically possess elevated network privileges.
Organizations must recognize that this threat extends beyond traditional email-based phishing.
The use of WhatsApp Web represents an evolution in delivery mechanisms, exploiting messaging applications less scrutinized than corporate email systems.
Security teams should implement strict controls restricting WhatsApp Desktop usage in corporate environments and establish monitoring for suspicious activity patterns associated with messaging applications.
Additionally, deploying application control solutions capable of blocking DLL sideloading attempts provides critical protection against this infection technique.
Proactive threat hunting for indicators of DLL sideloading particularly legitimate executables like SumatraPDF created and executed from temporary directories can identify compromise attempts before lateral movement occurs.
The indicators of compromise from this investigation remain available for threat intelligence integration, enabling organizations to strengthen their defensive posture against this persistent adversary.
Follow us on Google News, LinkedIn, and X to Get Instant Updates and Set GBH as a Preferred Source in Google.
