Operation Morpheus took down 593 Cobalt Strike servers used by threat actors
An international law enforcement operation code-named Operation Morpheus led to the takedown of 593 Cobalt Strike servers used by crooks.
An international law enforcement operation, code-named Operation Morpheus, aimed at combatting the criminal abuse of an older, unlicensed version of the Cobalt Strike red teaming tool.
The Cobalt Strike platform was developed for Adversary Simulations and Red Team Operations, currently provided by the cybersecurity software company Fortra. It has also become popular among threat actors over the past years, including APT29, FIN7, RYUK, Trickbot and Conti.
It is quite easy to find pirated versions of the software that were used by attackers in the wild.
Operation MORPHEUS, led by the UK National Crime Agency, included law enforcement authorities from Australia, Canada, Germany, the Netherlands, Poland, and the United States. This disruptive action, which concluded a complex investigation, began in 2021.
The operation took place between June 24 and 28 and was coordinated by Europol, which also collaborated with private partners, including BAE Systems Digital Intelligence, Trellix, Spamhaus, abuse.ch, and The Shadowserver Foundation. These partners used enhanced scanning, telemetry, and analytical capabilities to identify malicious activities and cybercriminal use.
The law enforcement experts identified 690 IP addresses and various domain names associated with criminal activities. The operation led to the takedown of 593 of these IP addresses across 27 countries.
“Fortra has taken significant steps to prevent the abuse of its software and has partnered with law enforcement throughout this investigation to protect the legitimate use of its tools. However, in rare circumstances, criminals have stolen older versions of Cobalt Strike, creating cracked copies to gain backdoor access to machines and deploy malware. Such unlicensed versions of the tool have been connected to multiple malware and ransomware investigations, including those into RYUK, Trickbot and Conti.” reads the press release published by Europol.
“Law enforcement used a platform, known as the Malware Information Sharing Platform, to allow the private sector to share real-time threat intelligence with law enforcement. Over the span of the whole investigation, over 730 pieces of threat intelligence were shared containing almost 1.2 million indicators of compromise.” concludes the press release. “Europol’s EC3 organised over 40 coordination meetings between the law enforcement agencies and the private partners. During the week of action, Europol set up a virtual command post to coordinate law enforcement action across the globe.”
In April 2023, Microsoft Digital Crimes Unit (DCU) announced that had collaborated with Fortra, the company that develops and maintains the tool, and Health Information Sharing and Analysis Center (Health-ISAC) to curb the abuse of Cobalt Strike by cybercriminals.
The Microsoft DCU secured a court order in the U.S. to remove cracked versions of Cobalt Strike (“refer to stolen, unlicensed, or otherwise unauthorized versions or copies of the tool”) so they can no longer be used by cybercriminals.
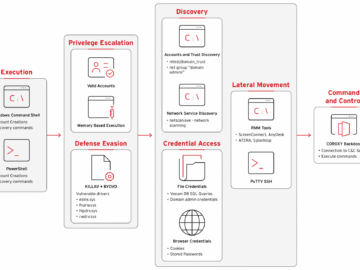
Threat actors, including ransomware groups and nation-state actors, use Cobalt Strike after obtaining initial access to a target network. The tool is used to conduct multiple malicious activities, including escalating privileges, lateral movements, and deploying additional malicious payloads.
“More specifically, cracked versions of Cobalt Strike allow Defendants to gain control of their victim’s machine and move laterally through the connected network to find other victims and install malware. This includes installing ransomware like Conti, LockBit, Quantum Locker, Royal, Cuba, BlackBasta, BlackCat and PlayCrypt, to arrest access to the systems. In essence, Defendants are able to leverage cracked versions of Cobalt Strike to brutally force their way into victim machines and deploy malware.” reads the court order. “Additionally, once the Defendants deploy the malware or ransomware onto computers running Microsoft’s Window operating system, Defendants are able to execute a series of actions involving abuse of Microsoft’s copyrighted declaring code.”

Example of an attack flow by threat actor DEV-0243.
Microsoft observed more than 68 ransomware attacks, involving the use of cracked copies of Cobalt Strike, against healthcare organizations in more than 19 countries around the world.
The attacks caused huge financial damages to the attacked hospitals in recovery and repair costs, plus interruptions to critical patient care services.
Microsoft also observed nation-state actors, including APT groups from Russia, China, Vietnam, and Iran, using cracked copies of Cobalt Strike.
“Microsoft, Fortra and Health-ISAC remain relentless in our efforts to improve the security of the ecosystem, and we are collaborating with the FBI Cyber Division, National Cyber Investigative Joint Task Force (NCIJTF) and Europol’s European Cybercrime Centre (EC3) on this case. While this action will impact the criminals’ immediate operations, we fully anticipate they will attempt to revive their efforts. Our action is therefore not one and done.” concludes the report.
In November 2022, Google Cloud researchers announced the discovery of 34 different Cobalt Strike hacked release versions with a total of 275 unique JAR files across these versions.
Google Cloud Threat Intelligence (GCTI) researchers developed a set of YARA rules to detect hacked variants in the wild with a high degree of accuracy. The researchers noticed that each Cobalt Strike version contains approximately 10 to 100 attack template binaries
Pierluigi Paganini
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
(SecurityAffairs – hacking, newsletter)