Oracle has linked an ongoing extortion campaign claimed by the Clop ransomware gang to E-Business Suite (EBS) vulnerabilities that were patched in July 2025.
While the company has yet to attribute the attack to this ransomware operation, Rob Duhart, the Chief Security Officer of Oracle, confirmed that customers had received extortion emails from the gang.
Duhart also urged Oracle customers to update their software and advised those requiring further assistance to contact the Oracle support team.
“Oracle is aware that some Oracle E-Business Suite (EBS) customers have received extortion emails, Duhart said in a Thursday statement. “Our ongoing investigation has found the potential use of previously identified vulnerabilities that are addressed in the July 2025 Critical Patch Update. Oracle reaffirms its strong recommendation that customers apply the latest Critical Patch Updates.”
Although it didn’t pinpoint a specific vulnerability that could have been exploited, Oracle addressed nine security flaws impacting its E-Business Suite as part of its July 2025 Critical Patch Update, three of them (CVE-2025-30745, CVE-2025-30746, and CVE-2025-50107) exploitable remotely without requiring user credentials.
Mandiant and the Google Threat Intelligence Group (GTIG) told BleepingComputer this week that executives at multiple companies have received emails requesting ransoms to prevent sensitive data allegedly stolen from their Oracle E-Business Suite systems from being leaked online.
According to Genevieve Stark, the head of GTIG’s cybercrime unit, the attackers began sending these extortion emails “on or before September 29, 2025,” and the threat analysts are still investigating this malicious activity.
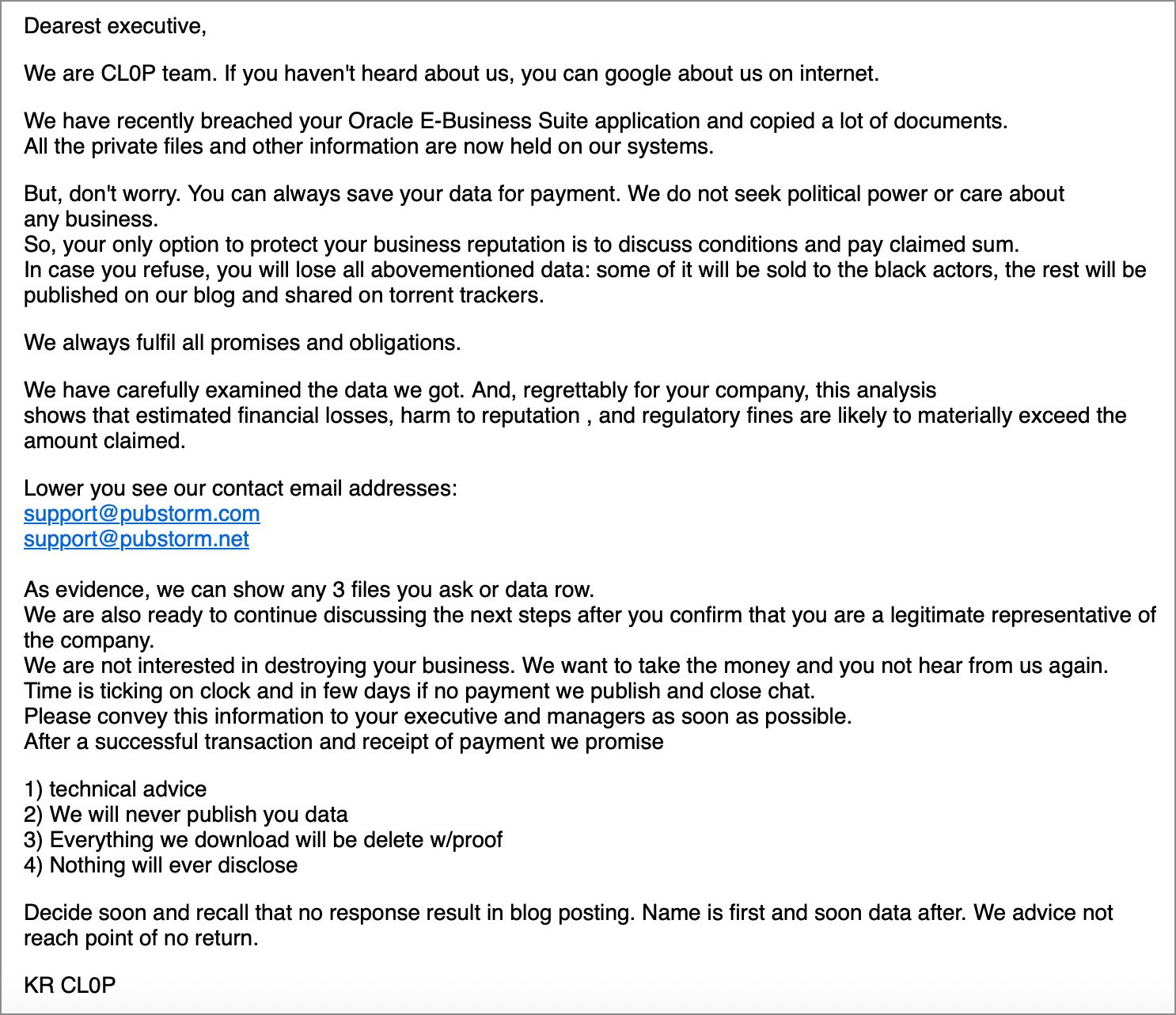
“We are CL0P team. If you haven’t heard about us, you can google about us on internet. We have recently breached your Oracle E-Business Suite application and copied a lot of documents. All the private files and other information are now held on our system,” an extortion email shared with BleepingComputer reads.
While Mandiant Chief Technology Officer Charles Carmakal stated that there is insufficient evidence to determine if data has actually been stolen, the Clop gang claimed in a statement shared with BleepingComputer that they are involved in the extortion campaign, linking the attacks to a bug in an Oracle product.
“Soon all will become obvious that Oracle bugged up their core product and once again, the task is on clop to save the day. We do not damage to systems and only expect payment for services we provide to protect hundreds of biggest companies in world,” Clop said.
Clop’s claims follow the extortion of dozens of victims in January, who were breached in a massive wave of data theft attacks targeting a zero-day vulnerability (CVE-2024-50623) in Cleo’s secure file transfer software.
Previously, the cybercrime group was linked to multiple other data theft campaigns targeting zero-day flaws in Accellion FTA, GoAnywhere MFT, and MOVEit Transfer, with the latter impacting over 2,770 organizations worldwide.
The U.S. State Department now offers a $10 million reward for any information linking Clop ransomware attacks to a foreign government.

Join the Breach and Attack Simulation Summit and experience the future of security validation. Hear from top experts and see how AI-powered BAS is transforming breach and attack simulation.
Don’t miss the event that will shape the future of your security strategy




