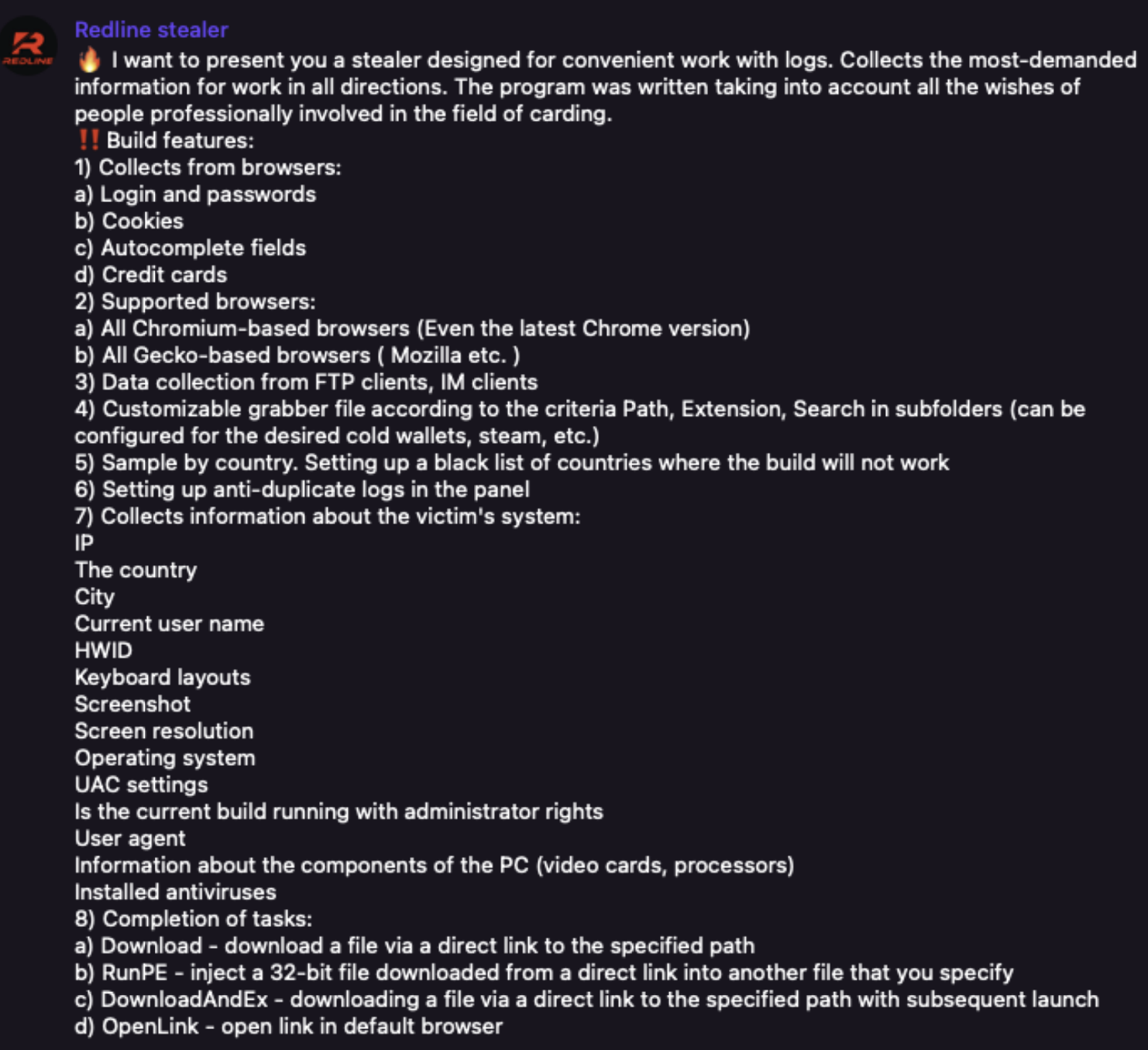
The rapid increase of info stealers has emerged as a major risk for organizations, including chatGPT, and has led to a rise in cybercrime in the last three years.
These info stealers are sold on malware-as-a-service platforms by threat actors and distributed through phishing emails and other software to steal credentials and personal information.
According to Flare research on more than 19.6 million stealer logs, 1.91%of stealer logs have access to credentials for business applications.
The stealer logs access to banking and retired portal applications can be fetched from high prices on the Genesis market.
Stealer Logs With Login Credentials
From the analysis they have discovered that 2,00,000 stealer logs contain access to open AI credentials.
Additionally, 46.9% of stealer logs contained access to Gmail accounts and that shows 8 million infected devices.
For better understanding, Flare has classified stealer logs into three categories such as corporate credentials, financial services, and consumer applications.
Corporate credentials include RDP, SAAS, and other devices of the organization. Since the employees access corporate services from their devices, this increases the risk.
These corporate credentials have high value in illicit markets and are sold in dark web markets.
Financial and banking service logs are also high value and can be fetched at an average price of $112 from the Genesis market.
And these consumer application logs are sold at publicly available telegram channels starting from a price range of $10 to several hundred dollars.
Also, logs are sold at a dark web marketplace known as the Russian market specializes in selling device information as well as at the Genesis market.

They also found around 179411 logs of AWS console credentials and 2344 google cloud credentials.
These are related to student accounts who registered on AWS and Cloud for research purposes.
Also, research revealed that 64548 docusign and 15591 quick books logs contain access and 23267 salesforce account, 42873 Hubspot, and 66050 CRM.
Stay up-to-date with the latest Cyber Security News; follow us on GoogleNews, Linkedin, Twitter, and Facebook.
